Akira Ransomware Breaches 3
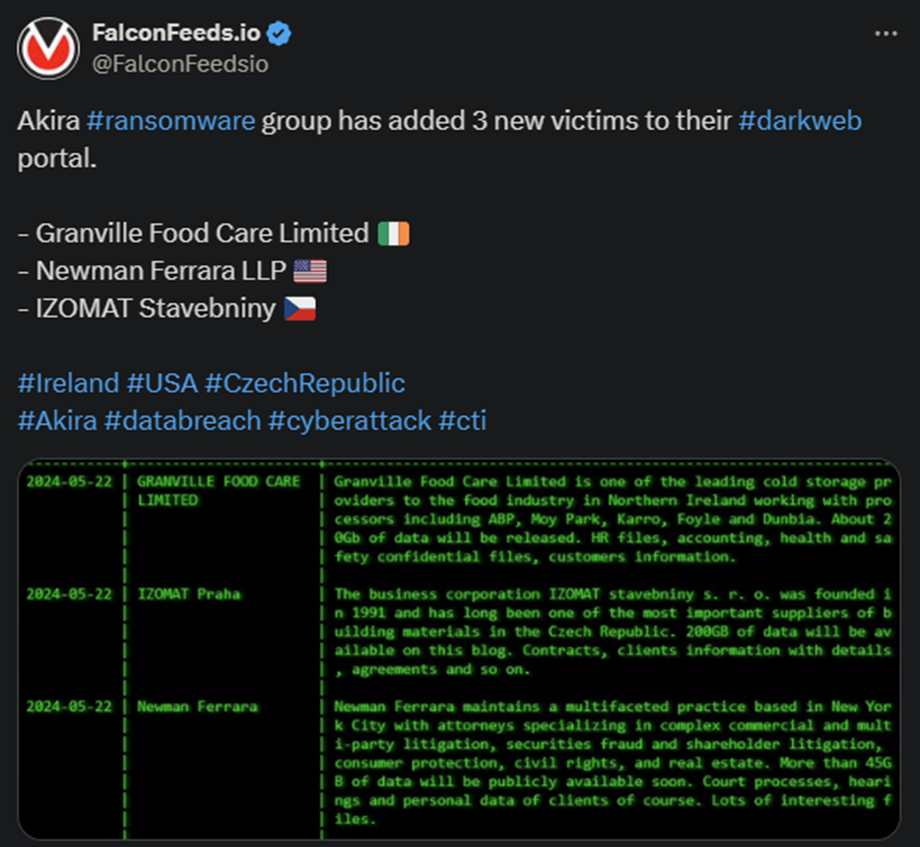
The Akira hackers announced 3 more victims today, coming from 3 different countries. These are Ireland, the US, and the Czech Republic. The hackers posted short summaries of the 3 companies, as well as the amount of data they’ve managed to steal.
- According to the original post, Akira operators managed to run with 20 to 200 GB of confidential data, depending on the victim
- The hackers use the stolen data as leverage during the negotiations, increasing the value of the ransom dramatically
- Akira is a newcomer in the ransomware space, after coming publicly in March of last year
The organization has been extremely active since, conducting hundreds of operations within its first year. This wouldn’t mean much if many of these operations weren’t successful. This suggests that the hackers are by no means amateurs.
Akira uses the double-extort method to increase the leverage during negotiations. The victim needs to bargain for the decryption key as well as the deletion of the stolen data. The latter rarely works.
As experts explain, the hackers will confirm that they’ve deleted the data after the ransom is paid. But that typically isn’t the case. That’s because the stolen information can still be useful, either directly or indirectly.
Unlike other ransomware gangs, Akira members don’t leave behind any ransomware notes. They only provide the victim with the contact details where they can be reached. All of the other details are discussed in the private chat.
Akira operators are known to show little flexibility during negotiations. They typically stick to the original ransom, which they always adjust based on the victim’s revenue. But what do we know about Akira so far?
Akira Ransomware – An In-Depth Look
Akira is one of the more active ransomware gangs, alongside Lockbit, RansomHouse, and several others. So much so that it managed to attract the attention of the FBI and the Europol, alongside several other agencies worldwide.
Several officials across multiple law enforcement agencies (CISA, FBI, Europol, and NCSC-NL) have warned that Akira ranks high on the danger scale. According to the initial reports, the hackers managed to amass around $42 million in ransom money.
This is quite the run if we consider that all of this was achieved in little over a year. According to the same experts, Akira is responsible for over 250 confirmed medium and high-profile victims. This is a staggering number.
Not to mention, experts have identified an increased trend in Akira’s attack pattern. The gang appears to become more active as time goes on. One explanation for this comes from assessing the group’s finances and financial activity.
As research has shown, Akira members have paid around $600,000 to Conti-affiliated addresses. The payments were made in Bitcoin and other cryptos. More importantly, 2 of the recipient wallets belong to Conti’s leadership.
This explains how the organization was able to grow so fast and become so aggressive and effective. Akira appears to be, at least in part, funded and supported by Conti, somehow beyond the grave.
The latter was dismantled in 2022, after an anonymous internal source leaked 60,000 confidential messages. These contained, among other things, Conti’s source code.
Which forced the gang to eventually dismantle. Apparently, this wasn’t enough to erase it from existence, as Akira’s case seems to hint at.
Our Mission
We believe security online security matters and its our mission to make it a safer place.

