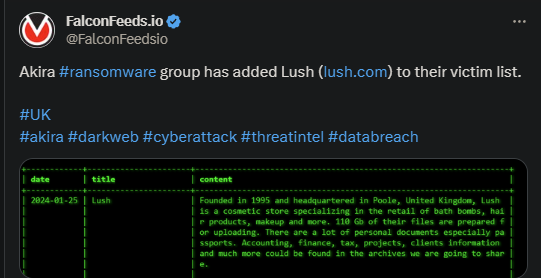
Akira Ransomware Infiltrates UK-Based Lush
Akira attacked another UK-based corporation, Lush, which specializes in bath bombs, hair products, and makeup, among other products and services. Lush didn’t provide a public comment on the attack.
- Akira posted evidence of the ransomware hit on its TOR network
- The organization stated that they managed to secure over 110 GB of data, which they’re ready to make public
- This may suggest that Lush refused to negotiate or that the negotiation failed to reach a satisfying conclusion for both parties
- Akira is known to be flexible with its ransom demands, but rather rigid in its negotiation tactics
Akira qualifies as a novel ransomware actor, as it only hit the public sphere in March of 2023. However, the organization’s progress and evolution since then have been nothing short of impressive. Akira is extremely adaptable, dangerous, and flexible.
The recent attack is proof of that, with Akira managing to infiltrate and rob a large corporate entity with roots dating back to 1995. And this is but one of the many attacks initiated by the cybercriminal group over the past several days.
Part of what makes Akira scarier than other ransomware actors is its ability to innovate and adapt to the market. The ransomware organization is known to constantly update and innovate its structure and MO to ensure a higher hit success rate.
The organization’s profile is also an indicative of its abilities. As it turns out, Akira shares significant code similarities with the now defunct Conti. And Conti ranked as the most prolific ransomware actor in the world, itself being a descendant of the famous Ryuk.
Akira’s Scary Profile
Akira is deemed as a more-than-competent cybercriminal actor with an even scarier potential. The group relies on the double-extortion method which is standard among ransomware actors.
This implies exploiting the victim’s vulnerabilities, encrypting the targeted data, cloning and downloading it, and hold it for blackmail purposes. As is the case with all ransomware MOs, the data will go public if the victim refuses to pay.
Which is often the case, given that Akira’s ransom demands vary between $200,000 and $4 million. However, experts generally advise against paying the ransom anyway, as this only incentivizes the attacker to continue doing what it does best.
Not to mention, paying the ransom doesn’t guarantee that the attacker will keep its word and not publish or sell the sensible data. That being said, it always comes down to the victim, and its specific requirements, to determine when it’s worth paying the ransom or not.
Our Mission
We believe security online security matters and its our mission to make it a safer place.

