BlackCat Ransomware Group Goes Down in Flames
Just yesterday, on the 19th of December, the FBI announced that they’ve disrupted the infamous ALPHV/BlackCat ransomware group. They’ve also offered a free decryption tool to over 500 victims around the world.
- BlackCat has attacked more than 1,000 organizations since its inception, quickly becoming one of the biggest cyber threats on the global scene
- The FBI has developed a decryption tool that has saved over 500 victims worldwide, saving them from demands totaling around $68 million
- The FBI has also seized multiple websites operated by the prolific threat actor
- One BlackCat spokesperson claims that the FBI has only seized BlackCat’s old blog, while the new one is still functional
- BlackCat’s eradication has caused tremors among other ransomware groups, particularly LockBit
The FBI has been tracking the group ever since its first appearance in December 2021. BlackCat quickly became the second-most prolific ransomware group in the world, after LockBit.

A BlackCat representative has said, however, that the FBI has only managed to close down their old blog site which they hadn’t been using for a long time. This has been further confirmed by an announcement made by BlackCat on its new blog site.
How Did the Takedown Happen?
The U.S. Justice Department publicly stated that the FBI has finally disrupted BlackCat’s operations after a long 18-months campaign against the group.
Court documents give us the whole story – the FBI has cooperated with multiple law enforcement agencies across multiple countries, including Switzerland, Germany, Australia, the U.K., Denmark, the U.S., Spain, and Austria.
Apparently, the FBI had an undercover agent posing as a client who managed to gain access to BlackCat’s dashboard and use the insider vulnerability to expose the group to the FBI’s larger assault.
There were speculations of a law enforcement action against BlackCat after it’s leak portal suddenly became offline on December 7th this year. But it came back online five days later, showcasing another victim.
The FBI also cooperated with dozens of BlackCat victims throughout the US to devise and implement a decryptor to the ransomware strain. Over 500 victims were saved from ransoms totaling $68 million.
With this opportunity at hand, the FBI also discovered how the group’s computer network works, and they managed to collect 946 public/private key pairs that hosted the TOR sites operated by the group. And they managed to shut down all these sites.
Is BlackCat Finished?
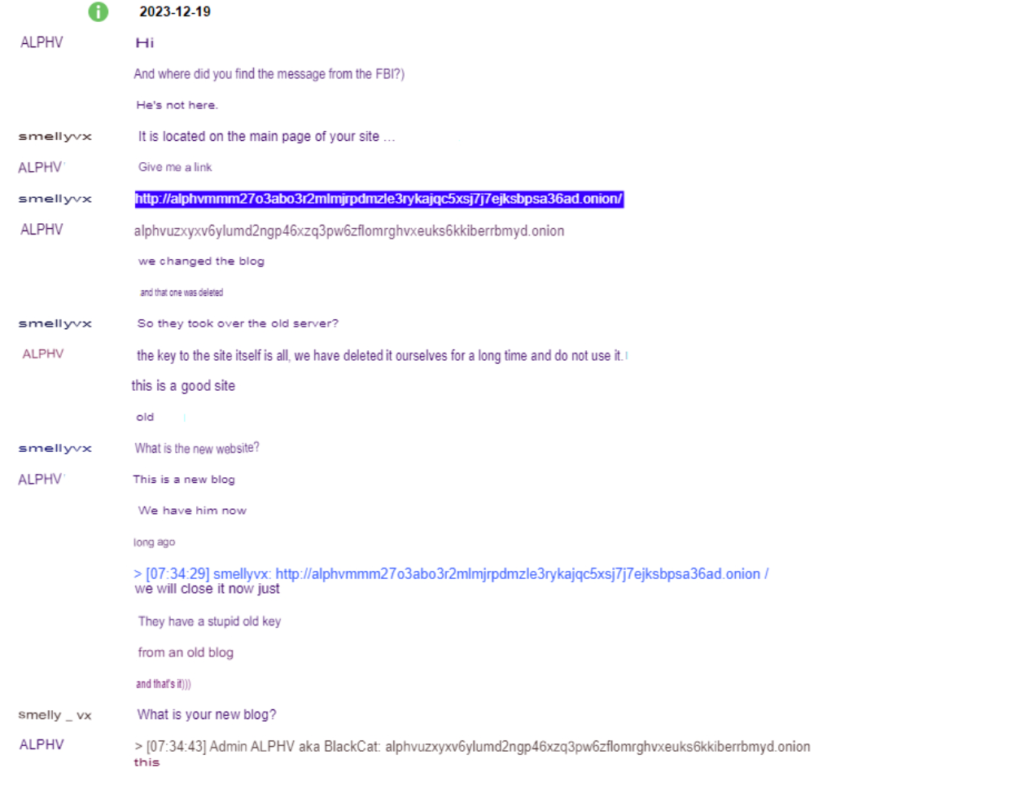
There’s one big problem about this FBI takedown of BlackCat – it appears to have missed the target. Firstly, the malware research group vx-underground has talked to an ALPHV/BlackCat representative.
https://twitter.com/vxunderground/status/1737091053218414592
According to the spokesperson, the FBI only managed to take down BlackCat’s old blog site, which doesn’t really harm their operations much.
While it’s true that the ransomware group can’t use the old blog site now, they don’t need to. A few hours after the FBI posted the takedown notice on the group’s old site, GOLD BLAZER (the threat group responsible for BlackCat) posted a notice on its new blog site.
You can see it below:
https://www.secureworks.com/blog/law-enforcement-takes-action-against-alphv-blackcat-ransomware
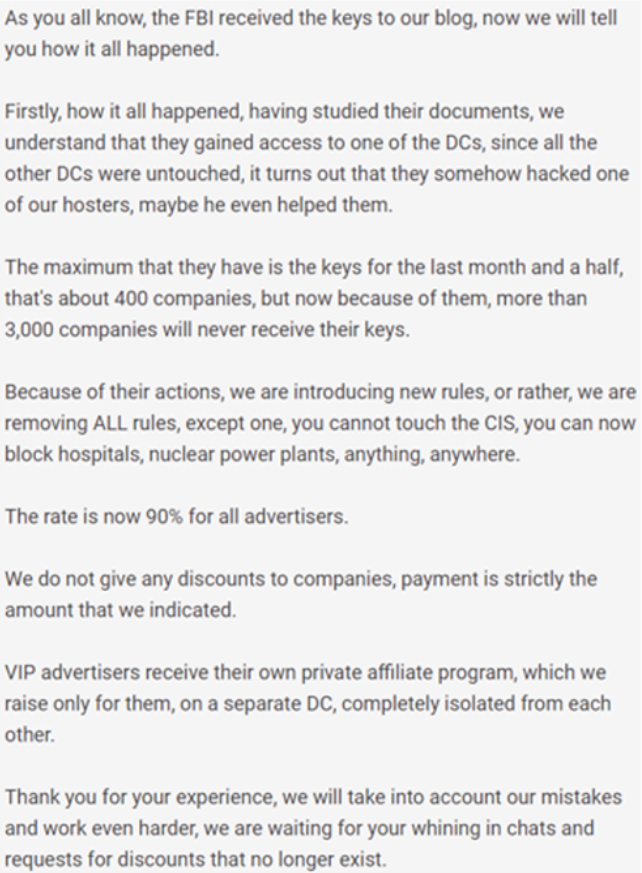
It seems that the FBI only managed to get its hands on a limited set of public/private keys for the ransom-group’s TOR websites. These keys only account for the last 1.5 month’s worth of victims, a total of around 400 companies.
In retaliation, BlackCat says that they will not hand over the decryption keys to over 3,000 of their victims, and they’re changing the rules of their RaaS service.
Clients are now able to attack anything except the Commonwealth of Independent states, including nuclear power plants, hospitals, or anything else. And this offer extends globally.
They also raised the payment rate to all advertisers and refuse to offer any more discounts to their clients, which sends a clear message – BlackCat is hurting, and they’re in deep financial straits.
The FBI attack seems to have had some effect, at least. But it also did not destroy the ransomware group entirely. They also seem to have re-seized the website again, though we don’t have much information about this.
The Aftermath of the FBI Seizure
In the aftermath of BlackCat’s network seizure by the FBI, other ransomware groups have begun making moves, like vultures to a corpse.
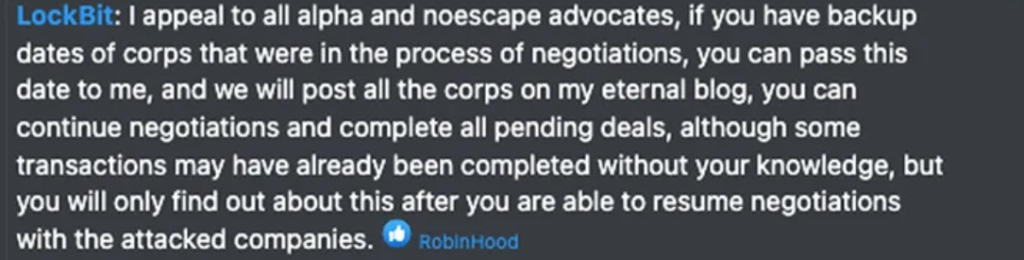
LockBit announced that they’re recruiting any affiliates that have been displaced by the BlackCat seizure, offering its own data leak site for clients to resume the victim negotiations.
https://thehackernews.com/2023/12/fbi-takes-down-blackcat-ransomware.html
BlackCat and LockBit are direct competitors in the RaaS (Ransomware-as-a-Service) industry, so it’s not a surprise that the former’s demise has prompted this answer from LockBit.
But not everything looks rosy for LockBit. If anything, this shows that even they may fall prey to government action soon.
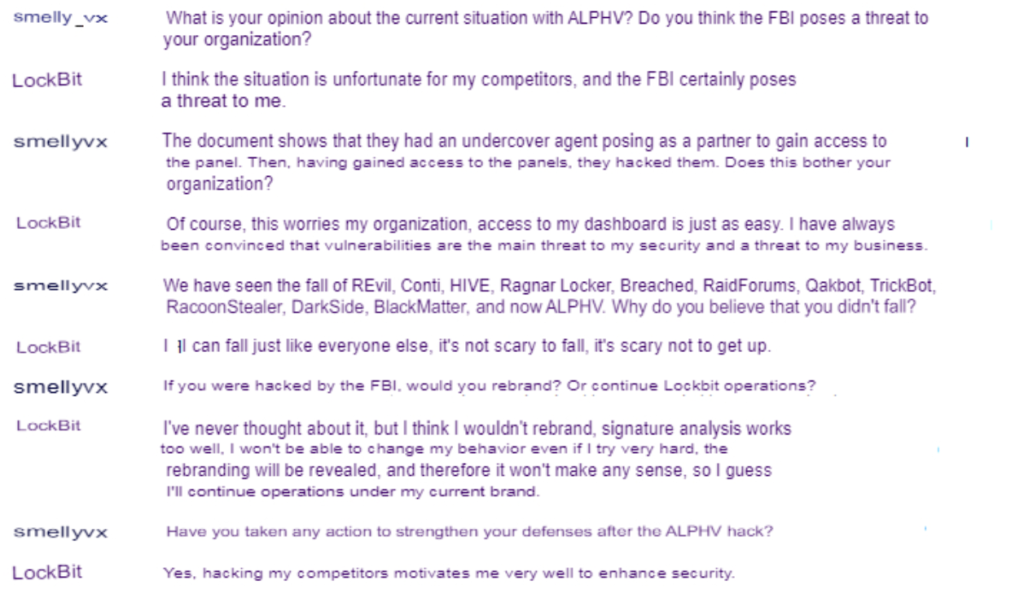
vx-underground talked to a LockBit administrator who said that he’s quite worried about BlackCat’s seizure by the FBI. He admits that the FBI is as much of a threat to him as it was to BlackCat.
https://twitter.com/vxunderground/status/1737294727383294375
By their own admission, LockBit’s administrator says that their data leak site’s dashboard is just as vulnerable as BlackCat’s, so technically, the FBI could launch an attack on them pretty soon.
Internal vulnerabilities have always been a threat to LockBit, according to their administrator, but BlackCat’s fall has taught them a valuable lesson.
They’re determined to improve their security and not suffer the same fate. But if they do, the claim that they won’t rebrand, instead opting to continue operations under the same name.
We’ll keep you in the loop if anything else changes!
Our Mission
We believe security online security matters and its our mission to make it a safer place.

