Cactus Ransomware Reaches Canada and Mexico
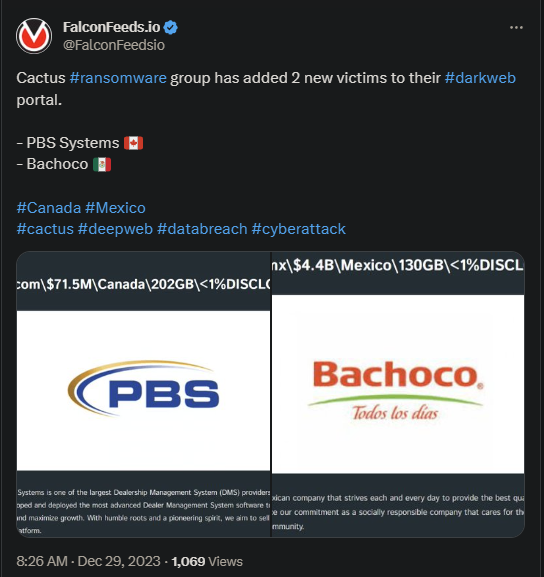
Cactus is responsible for 2 more victims, PBS Systems and Bachoco, from Canada and Mexico respectively. The cyberthreat actor is on a rampage lately, targeting high-profile targets almost exclusively.
- The recent attacks follow the actor’s trend since conception, victimizing high-profile organizations
- PBS Systems ranks as one of the largest DMS (Dealership Management Systems) providers in North America with over 30 years of experience
- Bachoco is a Mexican food provider with a reputable presence in the food industry
- Cactus published evidence of the attacks on their public platform
The attacks are evidence that the group is becoming more daring with every hit. Cactus is a new-coming player into the hacking sphere, as the organization first became public in March of 2023.
Since then, it has only targeted high-profile victims, whether public institutions or private corporations. This allowed it to climb to the 7th spot in the VPM category (Victims Per Month.)
There are no details regarding the outcome of the attacks, aside from the fact that Cactus managed to penetrate their victims’ defenses. The operator always uses the double extortion method.
This MO implies downloading the victim’s data, encrypting it on the parent system, and demanding a ransom in exchange for the decryption key. The attack often disrupts the victim’s operation and business, which is why many prefer to pay and cut their losses.
Who is the Cactus Ransomware Group?
This cyber-threat actor came to prominence in March of 2023 and quickly made a name for itself. The most unusual aspect about it is the frequency of the attacks. NCC reported that Cactus was responsible for more than 500 hits by September of this year.
More importantly, it seems like the group sped up its attack rate over time. It also appears that many attacks were successful in extracting the ransom, but many others failed.
In one infamous screenshot, a Cactus representative argues with one of the victims (a healthcare provider) who refuses to pay. As a result, the admin published the stolen data on their Tor platform.
This is common procedure when the victim refuses to pay and arguing does nothing to circumvent it. Cactus has several methods of attack, but prefers to rely on exploiting vulnerabilities in certain VPN services. Fortinet VPN is one of them.
The actor also encrypts itself to avoid detection and circumvent the firewall. This shows the need for upgrading defenses and investing in cyber-protection more than anything.
Our Mission
We believe security online security matters and its our mission to make it a safer place.

