Brave Browser 1.27 and Below Permanently Logs the Server Connection Time for All v2 Tor Domains
Cybersecurity researcher Sick.Codes has discovered a major vulnerability on Brave browser 1.27 and below where the browser permanently logs the server connection time for all v2 tor domains to ~/.config/BraveSoftware/Brave-Browser/tor/data/tor.log.
The case was filed under CVE-2021-22929 and has been addressed and patched by Brave on August 16 2021.
The discovered vulnerability can allow an attacker who obtains physical access to a device to view the exact timestamps that someone connected to a v2 onion address. This is obtained by reading the ~/.config/BraveSoftware/Brave-Browser/tor/data/tor.log file, where Brave saves this data.
This can help the attacker establish when the user is connected to a new v2 .onion site. This data can then be compared with server connection logs obtained from a compromised Tor endpoint, or the attacker may have been the party controlling the server (i.e., honeypot).
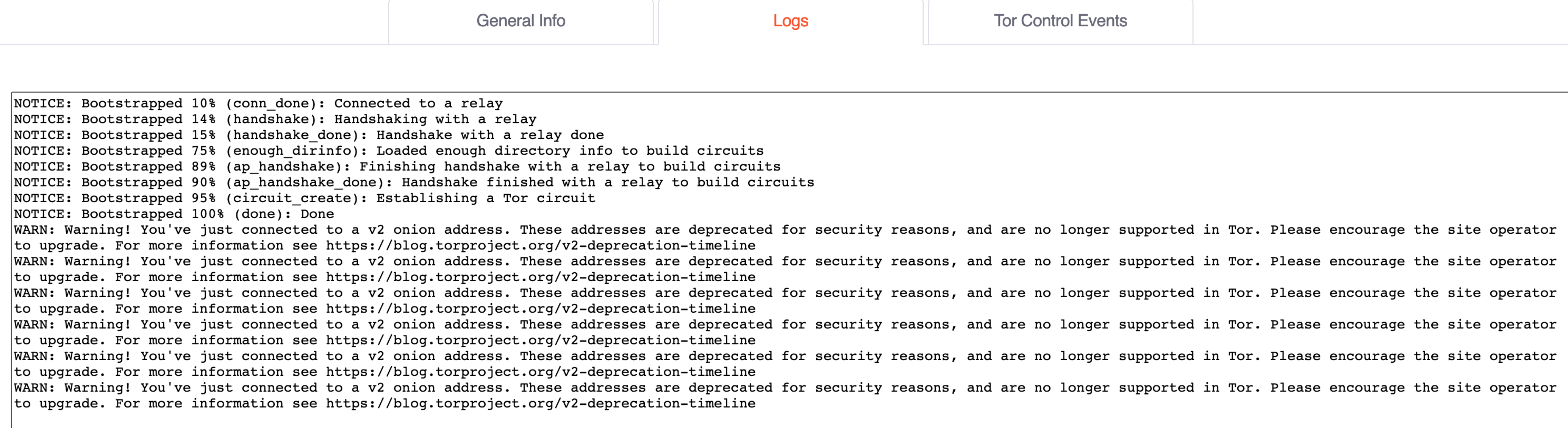
A log file would contain something like this:
Jul 01 08:40:50.000 [warn] Warning! You've just connected to a v2 onion address. These addresses are deprecated for security reasons, and are no longer supported in Tor. Please encourage the site operator to upgrade. For more information see https://blog.torproject.org/v2-deprecation-timeline
Jul 01 08:40:50.000 [warn] Warning! You've just connected to a v2 onion address. These addresses are deprecated for security reasons, and are no longer supported in Tor. Please encourage the site operator to upgrade. For more information see https://blog.torproject.org/v2-deprecation-timeline
Jul 01 08:40:51.000 [warn] Warning! You've just connected to a v2 onion address. These addresses are deprecated for security reasons, and are no longer supported in Tor. Please encourage the site operator to upgrade. For more information see https://blog.torproject.org/v2-deprecation-timeline
A classic example would be when a journalist in an authoritarian country accesses a whistleblower v2 .onion site secretly run by the government, who will then raid the suspected user and compare Brave log files with server logs.
They will then be able to correlate the Brave timestamps, and the server logs and determine that the raided user was indeed the one accessing the website.
This vulnerability affected any Brave version, including and below v. 1.27. Brave users must update the browser as soon as possible if they use its built-in Tor Connectivity feature and still run v. 1.27 or any other version below.
The update is available since 16 August.
Why is this happening?
In September 2020, Tor announced that it would deprecate v2 onion addresses. Beginning June 2021, the Tor browser started warning users about this change whenever they accessed a v2 domain. Users receive warnings when accessing a new v2 domain, even during the same browsing session.
The Brave browser versions 1.27 and below logged these events in the ~/.config/BraveSoftware/Brave-Browser/tor/data/tor.log file.
Because the Brave log timestamps coincide with the server connection time (when the warning is displayed), an attacker could determine the user’s identity if physical access to a device is obtained.
Sick Codes explained to Privacy Affairs during a phone interview that he also notified Tor of this issue, but Tor did not consider this a major problem.
Sick Codes commented:
“V2 tor domain only 16 characters but companies like Facebook can brute force vanity URLs such as Facebook’s facebookcorewwwi.onion. This is a massive security risk because generating the same vanity URL can perform all kinds of attacks given that the tor network is distributed.
So the tor project made v3 domains now a whopping 56 characters long.”
Tor will release a new client in October 2021 that will disable v2 domains.
You can read more about Tor’s v2 deprecation timeline here: https://blog.torproject.org/v2-deprecation-timeline
A Brave user can check if they are affected by this vulnerability by doing the below:
- Visit http://wikitoronionlinks.com/ while using Tor Private Browsing on the Brave Browser.
- Click on a few .onion v2 URLs
- Inspect ~/.config/BraveSoftware/Brave-Browser/tor/data/tor.log
- If you are affected you should be able to see all v2 domain access logs at full connection time (server connection)
They should be seeing something like this:
(Click image to enhance)
Impact evaluation
Sick has previously reported a vulnerability to the Brave project – https://hackerone.com/reports/1024668 – which received a CVSS of 5.5. The previous vulnerability merely related to the last time a device had used Tor.
The impact of the vulnerability released today is expected to be much larger, given it includes the exact timestamp of every single 16-character tor domain visited.
Not only does it log the timestamp of the connection, but the logging is entered only once the server response, magnifying the timestamp’s accuracy. Sick Codes, in a phone interview, mentioned that the client, “should not be logging connection timestamps with that specificity.”
Sick also stated that the client should be logging at the time of entering the address into the address bar, as opposed to waiting for the remote server, which may even be compromised, to log at the same time as the client.
Sick Codes commented the following:
“A cold boot attack, you know, where you freeze the RAM of the PC, which still affects the Tor project as we speak, would essentially be a perfect correlation attack. I’m not a statistician, but I think the probability of someone opening 20 tabs in the exact timestamps that are logged, over a whole browsing session, in both Brave & even Tor project’s browser, is… like the ultimate fingerprint. Why can’t they log in once per session? Weirdly, they added so many logs about connecting to v2 domains.”
Sick added that:
“Tor closed the report as informative, which is another issue with bug bounty programs that I have: legitimate and dangerous vulns are being ignored. I just requested the CVE for tor since it should be removed ASAP.”
Brave quickly patches vulnerability
Sick Codes explained that Brave was very quick in fixing and patching this. In a phone interview, he said to Privacy Affairs that he was impressed the speed and professionalism Brave showed after the vulnerability was reported.
Sick Codes further pointed out that he was equally impressed by Brave’s professionalism in operating its bug bounty program, something he explained is rather rare, especially when involving large corporations, such as John Deere, for example.
This is also not the first time Sick Codes discovered an important vulnerability regarding Brave and Tor. Earlier in 2021 Sick Codes found that Brave’s Tor Mode sent queries for .onion domains to public internet DNS resolvers rather than Tor nodes.
Such a leak creates a major footprint that an adversary could use to correlate and determine the user’s identity.
Like this time, Brave was also quick in fixing and patching the problem back then.
Sick Codes explained to Privacy Affairs that while solutions such as Brave’s built-in Tor mode can greatly simplify accessing the dark web for the general public, from a security standpoint, nothing substitutes “old-school” methods such as using the Tor browser itself from a clean device not used for any other purpose or even booting a privacy OS from a USB stick.
Our Mission
We believe security online security matters and its our mission to make it a safer place.