Cybersecurity Deep Dive: What Is Cybercrime-as-a-Service?
Cybercrime-as-a-Service (CaaS) takes everything we know about cybercrime and gives it a whole new meaning. Anyone can now launch sophisticated cyberattacks by hiring a black hat hacker on the dark web.
Instead of well-established hacker groups with known attack patterns and coding knowledge, we now have disgruntled employees, jealous exes or unethical competitors paying someone to hack you.
CaaS is effectively run like a business for cybercriminals. Threat actors offer their tools, knowledge, and infrastructure to conduct high-scale cyberattacks to anyone who pays.
There are 5 models of Cybercrime-as-a-Service:
- Ransomware-as-a-Service, where the hacker sells the ransomware encryption code to the seller. The seller can then deploy the code with ease and launch ransomware attacks unimpeded
- DDoS-as-a-Service, where the hacker sells access to a botnet so that anyone can launch a DDoS attack. Anyone can flood a business’ servers with requests and stop its operations
- Phishing-as-a-Service, where the hacker sells a phishing kit that contains a tutorial and the necessary software to launch a phishing attack
- Malware-as-a-Service, where the hacker sells a malware kit that you can use to carry out trojan attacks or spread viruses
- Access-as-a-Service, where the hacker gives you access into a business network. The client can then steal data, insert a worm, or any other malicious activity
Below, I’ll go through each CaaS model, explain how they work, how much they cost, and how to protect against them.
Ransomware-as-a-Service
Ransomware-as-a-Service is a business model where a threat actor sells a ransomware kit to a paying customer. The model can vary, though, and currently, there are four RaaS payment models:
- Client pays a monthly subscription
- Client enters an affiliate program (monthly fee) but the ransomware developer takes some of the profits from ransomware attacks
- Once-time payment for the ransomware kit with no profit sharing
- Profit sharing
Irrelevant of the revenue model, ransomware developers are making a lot more money selling the kit than by engaging in direct cybercrime.
The paying customer can pay anything from $100 to a couple thousand dollars, depending on the ransomware itself.
There’s also a difference in how sophisticated the RaaS model is. Some operators only give you a rootkit and instructions on how to use it. Others offer a much more comprehensive package.
Here’s what you might get from a RaaS package:
- The source code of the ransomware
- Instructions
- Infrastructure to manage the ransomware
- Customization tools for things like writing a custom ransom note, targeting a specific operating system, etc.
- Control panel
- Technical support
- Private forum
- Portal where you can see the status of all infections, total payments, information about the targets, etc.
As you can see, Ransomware-as-a-Service can be extremely comprehensive in the services it provides.
1. Examples of Ransomware-as-a-Service Groups
Ransomware as a service comes under many names:
- DarkSide – a very notorious RaaS group responsible for the Colonial Pipeline attack from May 2021. This resulted in a ransom of $5 million USD paid to a DarkSide affiliate and the loss of 100GB of data
- Dharma – formerly known as CrySis, this RaaS group was first discovered in 2016. Attackers using the Dharma ransomware usually demand 1-5 bitcoins from their targets and they’re not very selective of their targets either
- REvil – this group is known to have made over $100 million in profit in a single year, and they’ve notoriously demanded $10 million in a single ransom. The PINCHY SPIDER threat actor is selling this ransomware and takes around 40% of the profits following a successful ransomware payout
- Hive – the group became infamous for attacking Microsoft’s Exchange Server customers, with thousands of victims and millions of dollars on paid ransoms. The Department of Justice of the US announced on January 2023 that they’d seized two back-end servers associated with Hive in Los Angeles
These are just a few of the known RaaS services that have wreaked havoc in the world recently.
And all of them can be purchased via the Dark Web by any threat actor.
2. Prevention Methods Against RaaS Attacks
RaaS attacks aren’t any different from standard ransomware attacks. They’re just more unexpected, potentially more common, and they come from surprising places.
Here’s how you can prevent a RaaS attack:
- Create system backups for your databases. You can then recover the data if a RaaS encrypts it during an attack
- Use endpoint protection that works 24/7 and doesn’t need manual intervention
- Segment your network so you limit the attack surface and make it harder for a hacker to encrypt your entire system all at once
- Use anti-phishing protection to seal off the initial access to a RaaS attack
- Train your employees in cybersecurity awareness and emphasize a culture of security
- Keep up-to-date with your security patches to prevent any vulnerabilities in your network
With the emergence of Ransomware-as-a-Service, ransomware attacks will become more common. The threat vectors have multiplied exponentially and there’s no way to stop it.
All we can do is exercise more caution, be more aware of threat actors, and defend our data even more carefully.
DDoS-as-a-Service (DDoSaaS)
DDoS stands for distributed-denial-of-service. And DDoS-as-a-Service means that you can hire a hacker to launch a DDoS attack on a target of your choosing.
You don’t get a software, or a platform, or even a crash tutorial on how to launch a DDoS. Someone else does it all for you.
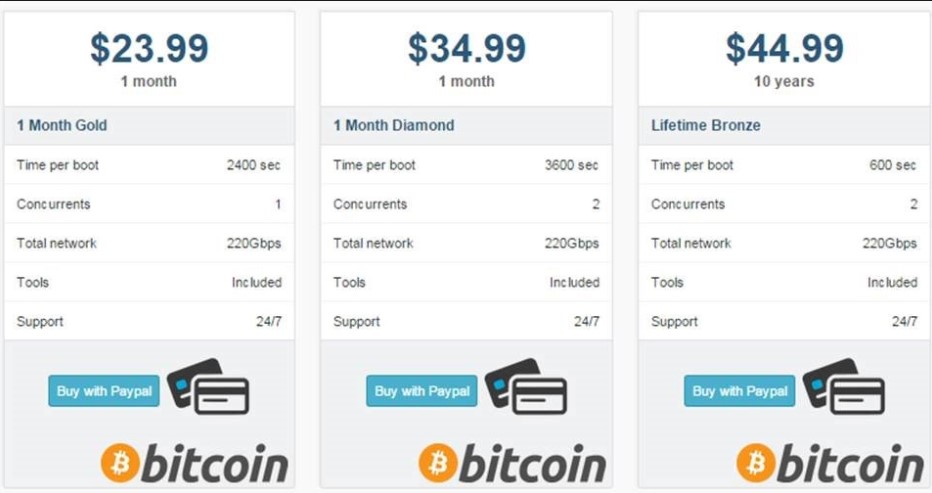
https://www.imperva.com/learn/ddos/booters-stressers-ddosers/
The model is simple:
- The hacker owns a botnet, which is a network of infected computers that can launch a DDoS
- The hacker advertises DDoS services on the Dark Web
- The buyer contacts the hacker and gives them a target, the type of DDoS they want, and the duration of the attack
- The buyer pays the hacker for the DDoS attack in cryptocurrency
- The hacker launches the DDoS attack
Since the payout is in cryptocurrency, the entire process is anonymous. Neither the hacker nor the buyer can be identified.
1. Types of DDoSaaS
There are two main types of DDoS-as-a-service:
- Booters
Booters are botnet networks that you can rent for a fee and use to launch DDoS attacks. The hacker-vendor will provide an interface and various tools to facilitate the DDoS attacks for the client.
With this, the client can launch a DDoS attack in seconds, and they don’t need any computing knowledge. The interface is easy-to-use and intuitive.
Alternatively, they can pay the hackers to launch DDoS attacks on their behalf.
Subscriptions start at $19.99/month and may go up to $500 per month
- Stressers
Stressers can be used to test the integrity and strength of a network by sending multiple queries at once. This doesn’t outright kill the network entirely but disrupts several of its services for testing purposes.
Stressers cost between $20 – $1000, depending on how long you want the “test” to last.
In reality, there’s no difference between Booters and Stressers. Both have the capacity for a full-scale DDoS.
It’s just that Stressers are officially used for “testing purposes”, not for cybercrime. One hacker pretends to be more ethical than the other, basically.
2. Prevention Methods Against DDoSaaS
There’s no difference between DDoS and DDoSaaS in terms of attack vectors or prevention methods.
Whichever cybersecurity methods work for one will also work for the other. This could mean:
- Network segmentation (same as before)
- Rate limiting, which lets you limit the rate at which traffic comes and goes to a server, preventing DDoS attacks
- Load balancing, which distributes the traffic to multiple servers, preventing the overload of a single server during DDoS attack
- IP blocking, which blocks traffic coming from suspected malicious sites to prevent DDoS attacks from them
This isn’t really revolutionary since DDoS attacks have been around for some time. DDoSaaS is the same thing, so the same protection works against it.
Phishing-as-a-Service (PhaaS)
Phishing-as-a-Service is one of the latest money-makings schemes invented by cybercriminals to make money easier.
PhaaS platforms provide you with a phishing kit in exchange for money. In some cases, you may also get a tutorial or other extra tools for a more sophisticated attack.
Normally, conducting a phishing attack needs:
- A phishing kit or software, which you have to create yourself or procure from somewhere else and adapt to suit your needs
- The creation of a phishing page, depending on which method you’re using to scam your victims
- Tuning your phishing system to identify and steal specific personal information or use a vulnerability in the victim’s system
There’s a lot of specialized knowledge you need to engage in phishing. But only if you did it the traditional way.
With PhaaS, you no longer need any of that. You can buy the phishing kit, which comes with everything you need to launch a phishing attack.
Once the phishing attack succeeds, the hacker can proceed with identity theft or financial fraud, depending on what information they were able to extract.
1. What Does a Phishing Kit Include?
Phishing kits sold by PhaaS vendors can include email templates, templates for fake websites, detailed instructions, customer support services, and even lists of targets.
Other phishing kits are more insidious and they’re instructed to make a copy of the data they steal and send it to the vendor. The hacker is essentially playing both sides:
- They’re selling a phishing kit to the paying customer
- They’re getting the valuable data stolen through the phishing kit that they sold
Phishing was the fastest-growing cybercriminal activity in 2021, according to the Internet Crime Report by the FBI. There were 323,972 cases of phishing in 2021, compared to 241,342 in 2020.
This is a clear indication that Phishing-as-a-Service trivializes cybercrime because criminals no longer need technical abilities to pull off a phishing attack.
The process is faster, more accessible, and anyone can do it as long as they have an internet connection and they pay for the phishing kit.
Legally, it’s much more difficult to stop PhaaS because, technically, the creator of the phishing kit did not carry out the attacks personally. They only provided the tools necessary to commit them.
And there’s almost no way to identify who carried out the attack since most Dark Web transactions are made with cryptocurrency.
2. Prevention Methods Against PhaaS
Phishing-as-a-Service relies entirely on known phishing tactics like email phishing, website phishing, and infostealers.
Consequently, you should apply the same security solutions for PhaaS as you would for normal phishing.
Cybersecurity awareness is number one. Know how a phishing attempt looks like, don’t download attachments from suspicious emails, and always double-check the URL of any site you access.
Secondly, use an antimalware service that can identify suspicious websites and files that you may download online.
Malware-as-a-Service (MaaS)
Malware-as-a-service is the largest model of Cybercrime-as-a-Service. MaaS operators will sell a variety of malware, including:
- Loaders, which are programs that download other malware onto the victim’s system
- Backdoors, programs that provide attackers with remote access to the victim’s device
- Ransomware, which allow you to encrypt a victim’s system and demand a ransom to unencrypt it
- Infostealers, which extract data from the victim’s system and redirect it to the hacker
Malware-as-a-Service is less of a specific category of Cybercrime-as-a-Service but more a general bucket for the idea of selling malware to threat actors.
The malware can be a phishing kit, a ransomware kit, or access to a botnet for DDoS attacks. The terminology is still fresh and it’s not as clear-cut yet.
1. Ecosystem of Malware-as-a-Service
Malware-as-a-Service systems aren’t made up of only vendors and consumers. There’s a lot more going on in the background.
Here are the main actors in a MaaS scheme:
- Malware Development – Hackers with technical knowledge who research vulnerabilities and construct malware that exploit those vulnerabilities
- Malware Vendors – Vendors that sell the malware created by the hackers. They’re responsible for offering the malware packages and hosting management service to clients.
- Malware Consumers – Regular people or criminals without technical knowledge who buy malware for illegal purposes. Alternatively, security researchers can also buy malware to develop security patches for them
Malware-as-a-Service is run like a business through and through. Many MaaS enterprises have customer support, technical support, and entire hierarchical structures.
The first phase is the hardest and requires the most technical knowledge. But that’s what the Malware-as-a-Service system fixes.
Hackers no longer need specialized knowledge to launch cyberattacks. Someone else already created the malware and they buy it. Easy and simple.
2. Features of Malware-as-a-Service
If you thought that Malware-as-a-Service only sells malware, think again. There’s an entire ecosystem of features sold by malware vendors, such as:
- Off-the-shelf Malware – These include ransomware, trojans, viruses, worms, or bots that are 100% operations and can be deployed as-is
- Customer Support – If the paying customer faces any issue with the product, the hacker-customer-support team is there to help. Just like how regular businesses operate
- Attacking Targets – If the customer does not want to get involved, they can ask the MaaS company to do it for them
- Cybersecurity Advice – MaaS companies can also provide advice to clients (for a price) on how to defend against malware in the future
There’s also a variety in terms of how MaaS systems distribute their malware services to clients.
Here are the three main ways MaaS systems work:
Most phishing emails work via email, so MaaS systems will almost always include this package. The malicious link includes an automated malware that activates itself when the victim clicks the link.
Then, after the victim’s system is compromised, more malware will be downloaded on the system and the MaaS-owned botnet will gain control.
- Malvertising
The second most popular MaaS option is to inject malicious code into legitimate advertising. Once the victim clicks on these ads, they’ll be redirected to a carefully-crafted website.
The website will install malware on the victim’s device, and this happens every time the victim clicks on an infected ad.
- Torrent Files
Torrenting itself is illegal, so naturally, hackers will include malware into these torrent files whenever possible.
Ransomware and crypto miners are common occurrences when downloading torrent files.
3. Prevention Methods Against MaaS
- Don’t click any suspicious links or download weird attachments from emails. This is a general rule you should always follow. Malware-as-a-Service packages are commonly transmitted through phishing emails
- Use anti-malware to protect yourself from malware
- Install the latest security updates
There’s not much else you can do to guard against MaaS compared to regular malware. That’s because they’re one and the same.
Access-as-a-Service
Access-as-a-Service is a distinct subset of Cybercrime-as-a-Service, where the product offered is unauthorized access to a target’s business network. The hacker provides the access credentials, allowing the buyer to carry out their intended actions.
Typically, Access-as-a-Service vendors only supply the credentials needed to infiltrate a system and offer no additional services.
The buyers are often hackers who prefer not to navigate the complexities of breaching a business network on their own.
There are three types of access brokers:
- Opportunistic Sellers who happen to gain access to a company or business and decide to offer one-off access to their networks in web-based forums
- Dedicated Access Brokers who gain access to business networks for a living and sell it to affiliates
- Online Shops consisting of multiple sellers who sell access to a single machine in a business network (usually)
All these brokers sell anonymous access to networks, meaning that the victim does not know about the infiltration.
Buyers will be able to escalate the infiltration to a full-fledged attack, whether that involves malware, phishing, or ransomware.
1. How Do Access Brokers Get Their Data?
Access brokers get their data through various means such as:
- Malware logs, which are collections of credentials gathered through botnets after monitoring infected users’ internet connections
- Vulnerability Exploitation, where data brokers find server vulnerabilities, exploit them, and find access credentials
- Data Breaches, where hackers perform data breaches and obtain password hashes that they crack to obtain credentials
The most dangerous data breaches involve zero-day vulnerabilities that result in the loss of access data.
If security vendors are not fast enough to develop security patches, the access brokers can spread the access credentials on the entire Dark Web.
Irrespective of the method used by access brokers, access data is the bread and butter of Access-as-a-Service activities.
2. Prevention Methods Against Access-as-a-Service
- Use 2FA
- Prepare incident response teams
- Apply the Zero-Trust Principle
- Ensure you install the latest security patches against the most common security threats
I won’t go into much details here because these are common sense security methods used against all threat actors and attack vectors.
Is Cybercrime-as-a-Service Here to Stay?
In all likelihood, Cybercrime-as-a-Service is not going anywhere. Rather, we should fully expect a continuous advancement in the number of threat actors, attack vectors, and attack surface.
The most dangerous aspect of CaaS is that it takes away the complexity and technical difficulty of cybercrime.
Many threat actors no longer need to:
- Scan systems for vulnerabilities
- Create malware from scratch
- Adapt existing malware or phishing software to match new scenarios
- Use social engineering to infiltrate into a network
- Plan out an attack and build an attack strategy
All of these are provided by black hat vendors that offer everything from the attacking tool (malware) and tutorials on how to use them, to the architecture for launching high-scale attacks, and access codes to business networks.
With enough money, you can order the launch of a DDoS attack on Facebook in a few minutes. Or you can buy your way into the servers of a Fortune 500 company.
The options are near limitless for how cybercrime can spread and evolve. We’ve just entered a phase where anyone can engage in cybercrime.
That’s the scariest thing about CaaS. And the only fighting chance we have is to stop being negligent with our data, start implementing robust security systems, and increase our cybersecurity awareness.
Half-measures are no longer relevant. The playing field has just become a battlefield, and it’s no longer viable to hope for the best.
Either you take precautionary measures or you become a victim.
PrivacyAffairs will continue to report on the growing menace that is Cybercrime-as-a-Service and offer you actionable advice on how to protect yourself.
Stay tuned for more cybersecurity information right at your fingertips!
Sources
Privacy Affairs – Cybersecurity Deep Dive: Everything About DDoS Attacks
Encyclopedia – Ransomware-as-a-Service (RaaS)
TechTarget – Ransomware as a Service (RaaS)
Crowdstrike – Ransomware as a Service (RaaS) Explained. How It Works & Examples
FBI Archives – Internet Crime Report 2021
Privacy Affairs – Why Is Phishing so Common & How to Protect Against It?
Tripwire – What Is Malware as a Service (Maas)?
Heimdal Security – DDoS-as-a-Service Attacks. What Are They and How Do They Work?
Heimdal Security – Access-as-a-Service: How to Keep Access Brokers Away from Your Organization
Privacy Affairs – The Art of Cyber Deception: Social Engineering in Cybersecurity


1 Comment
sam cullen
June 11, 2025 2:11 am
This is an outstanding deep dive into the evolving landscape of Cybercrime-as-a-Service. The breakdown of each CaaS model—RaaS, DDoSaaS, PhaaS, MaaS, and AaaS—makes it clear how low the entry barrier to cybercrime has become. What’s most alarming is how CaaS mirrors legitimate business models, offering technical support, user-friendly dashboards, and even affiliate programs.
The way you’ve highlighted the economic mechanics and infrastructure behind each service model is eye-opening, especially for businesses underestimating these threats. The inclusion of real-world examples like DarkSide and REvil adds a powerful sense of urgency.
One suggestion: a visual chart comparing the costs, complexity, and potential damage of each CaaS type would add even more value for readers looking to assess their risk levels quickly.
Looking forward to reading more insights from https://topmediaoutreach.com/current-cybersecurity-trends/this kind of clear, actionable content is needed now more than ever.