Biggest Cybersecurity Attacks in Europe in 2023
As of the time of writing this article, there have been 953 cyberattacks throughout the year in Europe, with over 5.3 billion records stolen.
According to a Statista survey conducted in June 2023, 70% of respondents in Europe, the Middle East, and Africa think that cyberattacks are a threat to their organizations.
Another study shows the average cost of cyberattacks to European and North American firms in 2023, by size:
- Very small (0-9 employees) – $5,300
- Small (10-49 employees) – $9,500
- Medium (50-249 employees) – $10,700
- Large (250-999 employees) – $24,800
- Enterprise (1000+ employees) – $53,500+
Moreover, several European countries are seeing an increase in average cyberattack costs over the 2021-2023 period:
- The Netherlands – $12,000 in 2021, $18,000 in 2022, and $21,400 in 2023
- Spain – $12,000 in 2021 and 2022, and $12,400 in 2023
- Belgium – $12,000 in 2021, $10,000 in 2022, and $18,700 in 2023
Other countries like the UK, Germany, France, and Ireland have instead seen a decrease in average cyberattack costs.
In this article, I’ll go over the 20 biggest cyberattacks in Europe in 2023. First, here’s a summary:
| Cyberattack | Records Breached/People Affected |
| DarkBeam | 3.8 billion records exposed |
| Luxottica | 74.4 million records leaked |
| UK Electoral Commission | 40 million records leaked |
| Motel One | 24 million data records leaked |
| JD Sports | 10 million customer records leaked |
| Pôle employ | 10 million records leaked |
| Elevel | 7 million records stolen |
| Kadaster | 6.5 million data records compromised |
| Shadow | Over 530,000 customer data exposed |
| Unidentified Limerick-based IT service company | Over 512,000 breached drivers’ licenses and debit card details |
| Swiss Emigrants | Over 425,000 data records leaked |
| Deutsche Bank | Personal data of bank clients (unknown scale) |
| Vodafone Italy | Personal data of clients, including subscription details, contact details, and identity documents |
| Orange | Subscription details, contact details, and identity documents |
| Kadaster | Residential addresses exposed for a month |
| 24 Hours of Le Mans Virtual | DDoS attacks on the servers, which disrupted the competition |
| Air France and KILM | Customer data compromised |
| NortonLifeLock | Attempted unauthorized access to users’ accounts |
| Norwegian Government | Attempted unauthorized access to users’ accounts |
| Italian Banks | Disruption of service at least five Italian banks |
Now, let’s go over each cyberattack in more detail and see what happened!
DarkBeam

https://techspark.co/company/darkbeam/
- When: September 18th, 2023
- What: 3.8 billion records exposed
- How: Misconfigured Elastisearch and Kibana interface
On September 18th, 2023, the CEO of SecurityDiscovery discovered that DarkBeam had “left an Elastisearch and Kibana interface unprotected, exposing records with use emails and passwords from previously reported and non-reported breaches.”
DarkBeam patches the vulnerability right away once it was announced but the fact still stands – more than 3.8 billion records had been exposed publicly.
These records are mainly from previous data breaches, with DarkBeam having gathered them to alert its customers to security incidents, but the data breach took place this year.
It’s quite ironic that a data dump meant to protect its clients ended up causing another massive data breach, impacting its customers.
It’s not clear whether someone accessed it or not but the way the data was structured, it would allow anyone to carry out extensive phishing campaigns with a high degree of credibility.
Luxottica

https://www.cascade.app/studies/luxottica-strategy-study
- When: 2021 (confirmed in 2023)
- What: 74.4 million records of 77 million accounts were leaked
- How: Unknown attack method
On April 30th and May 12th, 2023, the Luxottica database containing 74.4 million records stolen in November of 2021 was finally leaked publicly.
Andrea Draghetti, a leading researcher for Italian cybersecurity firm D3Lab said that the data dump contains 2.6 million unique domain email addresses.
Luxottica only learned of it in November 2022 when a post popped up on the dark web, describing the data breach.
The company reported the incident to the FBI and the Italian police, and the dark web site was closed, with its owned arrested by the FBI.
However, that didn’t count for much because now the data has been leaked online for free, and it’s unclear who leaked it.
Luxottica hasn’t made any official statements yet but the size of the data breach is huge.
UK Electoral Commission

https://en.wikipedia.org/wiki/Electoral_Commission_(United_Kingdom)
- When: August 8th, 2023
- What: 40 million records exposed publicly
- How: Potential vulnerability exploited by hackers
On August 8th, 2023, the Electoral Commission made a public statement about a “complex cyber-attack“ that resulted in a leak of 40 million records.
The data contained names, addresses, email addresses, telephone numbers, as well as the date on which the individuals achieved voting age. Apparently, the hackers had managed to access the Electoral Commission’s servers and hijack the control systems, stealing data between 2014 and 2022.
The incident originated in August 2021 when suspicious activities had been identifies on the systems. Though, at the time, the Commission ignored it only to realize what it was back in October 2022.
The plot thickens, though. A whistleblower told the BBC that the Commission had recently failed the Cyber Essentials audit right when the data breach happened.
Security researcher Kevin Beaumont also claimed that the Commission had been using an unpatched version of Microsoft Exchange Server that would have easily been breached by ProxyNotShell attacks.
While this hasn’t been proven, it stands to reason to assume that the hackers could have exploited a vulnerability in the Commission’s weak security system.
Motel One

https://en.wikipedia.org/wiki/Motel_One
- When: October 2023
- What: 24,449,137 breached data records
- How: Ransomware attack by the ALPHV/BlackCat hacker group
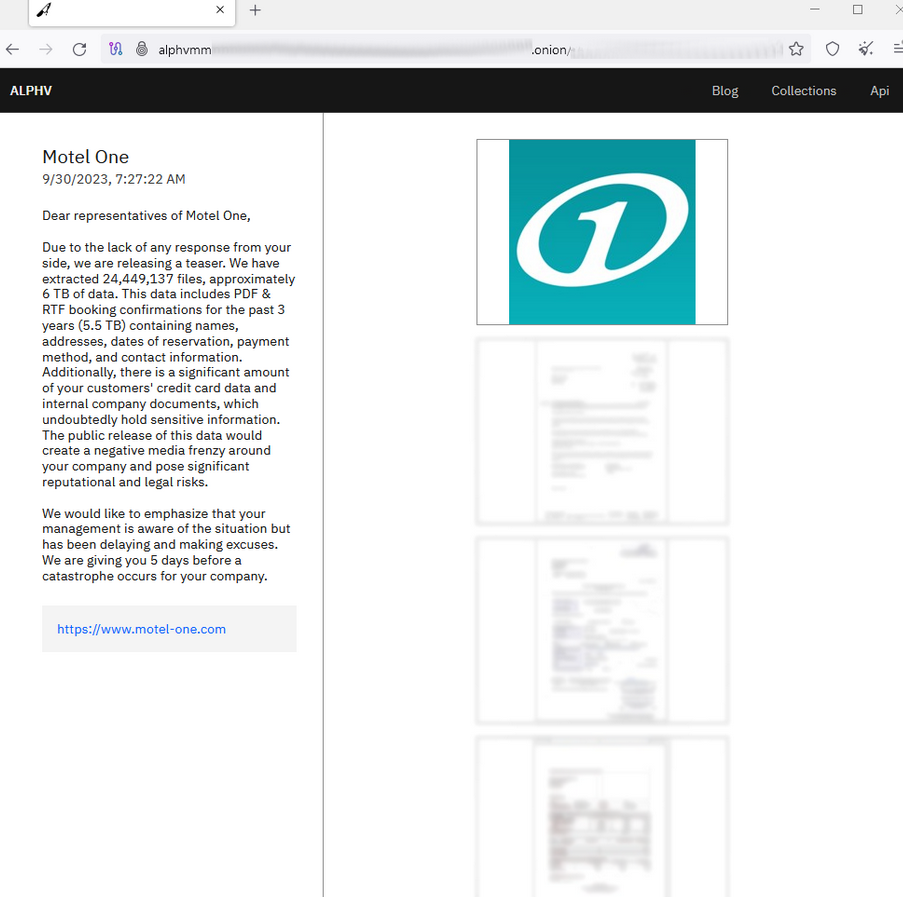
In October 2023, the German hotel group Motel One was attacked by the ALPHV/BlackCat ransomware group. Motel One is among the biggest hotel chains in Europe, so the data breach was proportionately large – 24.4 million files according to the hacker group.
Initially, Motel One stated on its website that the hackers had only stolen “address data from costumers – including 150 credit card details.”
They’ve also said that “Thanks to extensive measures, the impact was kept to a relative minimum. The business operation of one of Europe’s largest hotel groups was never at risk.”
However, ALPHV claims differently – a total of 6 TB stolen, amounting to 24.4 million files containing customer data.
The BlackCat announcement reads the following – “[The stolen data] include PDF & RTF booking confirmations for the past 3 years containing names, addresses, dates of reservation, payment method, and contact information.”
https://www.bleepingcomputer.com/news/security/motel-one-discloses-data-breach-following-ransomware-attack/
The hackers also claim to have a “significant amount of your customers’ credit card data and internal company documents.”
There haven’t been any further news or statements by the company. We could assume that Motel One chose to pay the ransom to avoid the public debacle of a full-fledged data breach.
JD Sports

https://en.wikipedia.org/wiki/JD_Sports
- When: January 2023
- What: Personal information of 10 million customers has been leaked
- How: Unclear how the hackers got the data
In January 2023, fashion retailer JD Sports said that there’s been a data breach where the personal data of 10 million customers has been leaked.
The data included names, phone numbers, billing and delivery addresses, order details, as well as the four digits of the victim’s payment cards.
Passwords and full payment data were not breached, according to the company. However, this much data is enough to launch phishing attacks.
The exposed data is from customers who ordered from JD Sports between November 2018 and October 2020, with purchases from brands like Millets, Scots, Blacks, Size?, and Millets Sports being most affected.
Neil Greenhalgh, the company’s Chief Financial Officer, said that “We are advising them [customers] to be vigilant about potential scam emails, calls and texts and providing details on how to report these.”
The company has begun working with a cybersecurity company to investigate the data breach and so far, we have no further details.
Pôle emploi

https://fr.wikipedia.org/wiki/P%C3%B4le_emploi
- When: April 2023
- What: 10 million records exposed
- How: Part of the MOVEit data breach
The French unemployment agency, Pôle emploi, has experienced a data breach in April 2023 that was associated with the MOVEit data breach in May 2023.
The exposed information included full names and social security numbers. Thankfully, email addresses, banking data, and passwords have not been exposed.
6 million of the affected individuals have registered in the unemployment centers by February 2022 and the other 4 million have registered in the last 12 months before the attack.
Pôle emploi has created a dedicated phone support line where they offer assistance to the concerns of the affected victims and provide more information about the incident.
The company has also clarified that the data breach has not affected its financial aid program or the online platform. So, job seekers can safely access their online portal using their passwords.
The MOVEit data breach is estimated to have affected over 1,000 organizations and over 77 million people. But the full extent of the data breach has not been determined yet.
Elevel

- When: January 24th, 2023
- What: 7 million data entries leaked, a total of 1.1 TB of data
- How: Unclear how the data was leaked
On January 24th, Cybernews discovered a data breach comprised of 1.1 TB of data that was attributed to Elevel – a Russian electrical engineering company.
The company has multiple wholesale stores as well as an e-commerce business. And the data leak contained 7 million data entries spread over two years. The data included names, surnames, email addresses, phone numbers, and delivery addresses of the customers.
https://cybernews.com/privacy/russian-e-commerce-giant-data-leak/
https://cybernews.com/privacy/russian-e-commerce-giant-data-leak/[/caption]
Cybernews stated that “If left exposed, threat actors could download and clone the cluster’s data and use for nefarious purposes, including phishing attacks, as they possess sufficient PII (Personally Identifiable Information) and the make their scam seem legitimate.”
The data dump also contained the clients’ login credentials (including passwords) in URL encoding. This is a very weak encryption standard according to most experts, so we can assume that this poses quite a risk to the exposed Elevel customers.
The good thing is that the data leak was officially “plugged“, according to Cybernews. There’s no more risk of bad actors getting their hands on Elevel customers’ private data.
Kadaster

https://validatagroup.com/nl/en/screening-software/partners/data-partners/kadaster/
- When: August 2023
- What: 6.5 million data records compromised
- How: Insufficient identity verification protocols imposed by the company led to the data records being effectively accessible to anyone
On August 2023, it was revealed that the Land Registry and Mapping Agency Kadaster from the Netherlands suffered a data breach that compromised over 6.5 million data records.
According to RTN Nieuws, anyone could create an account with Kadaster as long as they entered an account number and the details of any company that was registered in the Chamber of Commerce.
Kadaster would not verify the registrant’s identity and applications would be approved within a day. This means that anyone could effectively create an account with Kadaster and browse through all the registry addresses.
The Dutch DPA said that “This leak posed a great danger to threatened journalists, activists and politicians. But also anyone who has to deal with an angry, stalking ex. Someone could suddenly show up on the doorstep to threaten them, or worse. We therefore immediately instructed the Land Registry to close this leak.”
The bank said that the hackers could try to initiate unauthorized direct debits in the account holders’ names but they could not control their accounts using the compromised data.
Shadow

https://techgameworld.com/shadow-review-a-gaming-pc-in-one-hand/
- When: October 2023
- What: Over 530,000 exposed customer data, according to the hackers
- How: Advanced social engineering attack against a company employee
Two months ago, in October, the French cloud computing service provider Shadow became the victim of a social engineering attack that compromised over 530,000 customer records.
The company’s CEO, Eric Sèle, notified the customers as soon as they discovered the data breach.
Here’s what he said – “At the end of September, we were the victim of a social engineering attack targeting one of our employees. This highly sophisticated attack began on the Discord platform with the downloading of malware under cover of a game on the Steam platform, proposed by an acquaintance of our employee, himself a victim of the same attack.”
The data contained:
- Full names
- Email addresses
- Billing addresses
- Dates of birth
- Credit card expiry dates
The hackers claimed that they’d put the data up for sale if Shadow would not negotiate with them. According to TechCrunch, many of the stolen records contain private home addresses of Shadow customers, and others contain private API keys.
According to the company, no passwords were compromised, which is something at least. They’re also advising customers to be way of suspicious emails and to enable 2FA on their accounts.
Unidentified Limerick-based IT Services Company

- When: October 2023
- What: Over 512,000 drivers’ licenses and debit card detail receipts of Irish motorists compromised
- How: An error in the data controller’s systems
In October 2023, an unidentified IT services company based in Limerick suffered a data breach where the personal data of 512,000 motorists was compromised.
The motorists had their vehicles towed by the authorities, which were using a Limerick-based IT services firm to keep track of the data.
However, the firm experienced a data breach and all the data until 2017 was compromised. Apparently, breach was caused by a software error within the company’s systems.
Cybersecurity researcher Jeremiah Fowler notified the Gardaí about the data breach, claiming that he had found an unencrypted and publicly-accessible online database with driving licenses, spreadsheets, and vehicle registration information.
Fowler further stated that he was able to access receipts with debit card details, incident summary reports, and drivers’ licenses through the data dump.

https://www.independent.ie/irish-news/thousands-of-drivers-have-sensitive-data-exposed-to-hackers-in-major-it-breach/a1379036136.html
It’s still unclear whether or not any bad actors managed to get their hands on the data and if the motorists will be in any danger.
The Irish DPA had also started investigating the data breach when it was announced. It’s also unclear who received a fine for the data breach, the Gardaí or the IT services company
Swiss Emigrants

- When: July 2023
- What: Over 425,000 personal data records of Swiss emigrants were compromised and put up for sale on the dark web
- How: Ransomware attack against CH Media and NZZ Publishing Group, two Swiss publishing houses
In July of this year, 425,000 personal data records of Swiss emigrants were compromised in a data breach on the Swiss Review, after two publishing houses became the target of ransomware attacks.
All the Swiss emigrants had been added to the journal’s sender list by default, and when the leak took place, their data was also compromised.
Eventually, cybersecurity experts discovered that the hacker had put the data up for sale on the dark web, though we don’t know if anyone bought the datasets or not.
The hacker exploited a single vulnerability to compromise the Swiss Review and two other associated publishing houses. And even the foreign ministry said that they don’t know exactly how much data was stolen.
Further identified as “Play“, the hacker group has Russian ties, and they’d asked for a ransom from the two publishing houses before publishing the data.
However, the two publishing houses refused to pay the ransom, as many companies often do. Fortunately, other than addresses, there was no other personal data included in the data leak.
Deutsche Bank AG

https://www.lsta.org/members/deutsche-bank-ag/
- When: July 2023
- What: Personal data of bank clients
- How: Part of the MOVEit data breach that impacted hundreds of companies across the world
The MOVEit data breach continues to make victims as Deutsche Bank AG, one of the largest financial institutions in the world, was breached.
The bank stated that “Deutsche Bank’s systems were not affected by the incident at our service provider at any time.” It’s also unclear how many clients have had their personal data leaked. All the victims received notifications from the bank, though.
While the hackers could not obtain unauthorized access to the victims’ bank accounts using the stolen data, they might try to initiate unauthorized direct debits.
As a response to this, the bank has extended the period for unauthorized direct debit returns to 13 months. This will give its customers enough time to identify, report, and be compensated for any unauthorized transactions.
Only the bank’s account switching service had been affected by the leak, but some reports suggested that the victims’ payment card data might have also been compromised.
Vodafone Italy

https://en.wikipedia.org/wiki/Vodafone_Italy
- When: November 2023
- What: Subscription details, contact details, and identity documents with sensitive data
- How: Unclear how the data breach took place
The Italian subsidiary of Vodafone was hacked in November 2023 after its Portuguese counterpart had suffered the same fate in February 2022.
This time, we don’t know the extent of the data breach but it has been confirmed that the stolen data contains subscription details, contact details, and identity documents with sensitive data.
No passwords or other network traffic data have been compromised, which is relieving to know. The company notified its customers immediately and asked them to stay aware of potential phishing attacks and other scams.
This attack on Vodafone Italia might be connected to a post by hacker group KelvinSecurity in September 2022 where they claimed that they were holding hostage 295,000 files (310GB) stolen from Vodafone Italia.
However, the company took notice of the announcement at the time, investigated it, and concluded that there had been no unauthorized access on its systems.
We also know that Vodafone has been a constant target of the GDPR because of its repeated breaches of privacy and data protection policies.
Orange

https://en.wikipedia.org/wiki/Orange_S.A.
- When: November 2023
- What: Subscription details, contact details, and identity documents with sensitive data
- How: Ransomware attack to one of Orange’s suppliers, a debt collection service
In November 2023, Orange announced that one of its suppliers, a debt collection service, had been hacked. As a result, a “limited number of clients” of Orange had their personal data compromised. They did not mention how many customers were affected but that they had alerted all of them.
The data stolen included:
- Full name
- Postal addresses
- Telephone number
- Email address
- DNI/NIE number
- Nationality
- Date of birth
- IBAN code of some clients
The National Institute of Cybersecurity sent an alert to all affected customers, saying that “If you have received the communique from the affected company, we advise you to be especially cautious over the next few months with emails, messages or calls from which you cannot confirm their origin or sender, especially messages requesting banking information or credentials. These messages could be fraudulent.”
Several other Spanish telecom companies have been in the crosshairs of hackers recently, including Telefonica and Vodafone. We still don’t know what the hacker will decide to do with these data records but they haven’t been put up for sale as of yet.
Orange hasn’t made any announcements regarding a ransom but this doesn’t mean there hasn’t been any. Companies like to keep silent about these things, for obvious reasons.
Kadaster

https://validatagroup.com/nl/en/screening-software/partners/data-partners/kadaster/
- When: November 2023
- What: Residential addresses exposed for a month
- How: Human error
Kadaster had its second data breach of the year in November 2023, after human error had led to the exposure of protected residential addresses for almost a month.
The organization managing real estate says that the data leak took place after a system update, which made the hidden addresses visible for almost a month.
The registrants had specifically asked to keep their residential addresses hidden for various reasons. Kadaster said that “Obviously, we find this incident very annoying” in an email to one of the victims.
We still d0n’t have a specific number of victims affected by this data breach and also no information about any bad actors getting their hands on the data.
It’s quite possible that the data may have been discovered by threat actors. Fortunately, the harm that they can do with only a residential address is limited and wouldn’t pose much of a risk to the victims.
Kadaster did not mention what actions they took to mitigate the system error that caused the data breach but we can safely assume it’s not a risk anymore.
24 Hours of Le Mans Virtual

https://us.motorsport.com/gaming/news/24-hours-of-le-mans-virtual-continues-to-attract-champions-from-around-the-world-for-the-final-roun/10417170/
https://us.motorsport.com/gaming/news/24-hours-of-le-mans-virtual-continues-to-attract-champions-from-around-the-world-for-the-final-roun/10417170/[/caption]
- When: January 2023
- What: DDoS attacks on the servers, which disrupted the competition
- How: DDoS attacks
In January 2023, the 24 Hours of Le Mans Virtual edition took place, with big names such as Max Verstappen and Romain Grosjean participating on behalf of their teams.
Several DDoS attacks shut down the servers several times, suspending the race and putting Verstappen at a massive disadvantage by dropping from 1st place all the way to 17. He eventually quit the race in frustration and said that “This is the last time I am ever participating […] Honestly, it’s a joke, you can’t even call this an event. Clown show.”
It is quite frustrating that the drivers prepared for this event for 5 months, and then something like this happens that destroys all your hard work.
While they first suspected that there was a technical failure causing all this, the race organizers began suspecting foul play afterward – a security breach. Most likely a DDoS, though, and not a data breach.
As far as we know, there has been no data theft or unauthorized access to sensitive information of any kind, so this wasn’t your typical cyberattack.
The organizers took the necessary actions to increase their security and restart the race, which finished without other incidents.
Air France & KLM

https://skift.com/2020/02/20/air-france-klms-324-million-in-fuel-savings-likely-to-offset-coronavirus-outbreak-costs/
- When: January 9th, 2023
- What: Customer data compromised
- How: Unclear
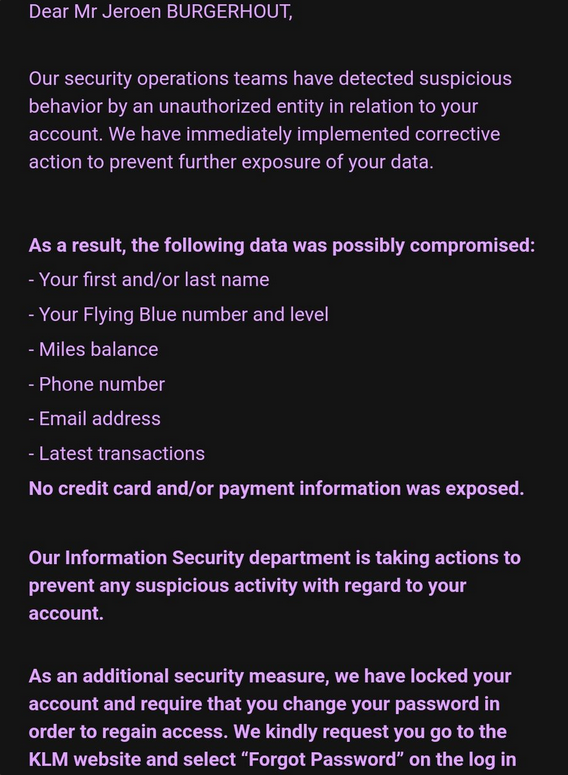
On January 9th, 2023, Air France-KLM Loyalty Blue customers received a notification that some of their personal data had been leaked as part of a data breach.
The data included:
- Names
- Email addresses
- Phone numbers
- Most recent purchases
- Flying Blue information (accumulated mile balance)
- Flying blue number and level
https://twitter.com/BurgerhoutJ/status/1611427713629175808
https://twitter.com/BurgerhoutJ/status/1611427713629175808[/caption]
The company immediately assured customers that their sensitive information, such as credit card information, was still safe and that it was not compromised. Still, they did recommend customers to change their passwords.
This doesn’t sound like they stopped the data breach on time, though. Plus, some of their customers are complaining on X (Twitter) that their password policies are quite poor, with limited characters and special characters.
The company might have to update their security policies and take a more proactive approach. They still haven’t released any new information about the origin of the attack or if the data has been put up for sale on the Dark Web.
However, we may see the aftermath of this data breach in a few months, as is often the case with these attacks. Hacker groups don’t necessarily publish or sell the data immediately.
Norton LifeLock

https://www.nortonlifelock.com/us/en/newsroom/digital-asset-gallery/logos/
- When: January 2023
- What: Attempted unauthorized access to users’ accounts
- How: Credential stuffing attack using credentials bought from the Dark Web
In January 2023, NortonLifeLock disclosed an attempted data breach from a threat actor. The hacker had tried a credential stuffing attack against many NortonLifeLock customers.
Essentially, they’d tried to log into their accounts using credentials bought from the Dark Web. Fortunately, they did not manage to gain access to any accounts, as per Norton’s statements.
Here’s what they said – “Our systems were not compromised. However, we strongly believe than an unauthorized third party knows and has utilized your username and password for your account.”
They also mentioned that the hacker made a large volume of (failed) login attempts but that none of them met with success. Credential stuffing is usually not very accurate or effective but sometimes, the hacker finds a particularly unaware user who hasn’t changed their login credentials after being exposed.
The data compromised includes names, phone numbers, and mailing addresses. It’s also possible that the attackers gained access to the users’ private vault data in their Norton Password Manager.
The extent of the damage inflicted by the threat actors is still unclear but Gen Digital, NortonLifeLock’s parent company, said that they’d closed the vulnerability on time.
Norwegian Government
https://www.norden.org/en/information/norwegian-flag
- When: July 2023
- What: Unusual network traffic that impacted 12 ministries and temporarily disrupted mobile and email services
- How: Exploitation of an unknown vulnerability in the software of one of the government’s suppliers
In July 2023, the Norwegian government became the victim of a cyberattack that appeared to be a DDoS attack at first. There was unusual network traffic that impacted over 12 ministries and made their mobile services (including email) inaccessible.
The government believes the attacker is a Russian state-sponsored threat actor and that it might be tied to the attacker that DDoS’ed the government last year.
Erik Hope, the director of the Norwegian ministries’ security and service organization, stated that the cyberattack was unusual in the amount of traffic it manipulated.
The attacker exploited an known vulnerability (zero-day) in the software of one of the government’s suppliers. He further said that “it is too early to say anything about who is behind it and the scale of the attack. Our investigations and the police’s investigation will be able to provide more answers.”
With the Ukraine-Russia war in the background and Norway being a NATO member who’s offered support to Ukraine, it would be no surprise that Russia-sponsored hackers launched attacks against it.
Italian Banks

https://upload.wikimedia.org/wikipedia/commons/thumb/a/ac/Printable_Flag_of_Italy.svg/1500px-Printable_Flag_of_Italy.svg.png
- When: August 2023
- What: Disruption of service at least five Italian banks
- How: DDoS attacks by pro-Russia group NoName057(16) against several Italian banks
In August 2023, several Italian banks became the victims of a DDoS campaign against them by threat actor NoName056(16). The hacker group has known Russian ties and they’ve previously stated their motivations for these attacks.
Here’s what they said on their Telegram channel – “The worship of the Ukronazi idol continues in the Russophobic countries of the West… And we once again remind the Russophobic Italian authorities that such actions will not remain without our attention.”
Some of the targeted banks include BPER Banca, Intesa Sanpaolo, Monte dei Paschi di Siena, Banco Popolare di Sondrio, and FinecoBank. Their services were disrupted for over 8 hours as the DDoS attack ravaged their servers.
This particular hacker group has attacked several NATO member countries since the Ukraine-Russia war has started. They’ve targeted Lithuania, France, Germany, Bulgaria, Poland, Denmark, Spain, and many other countries.
On the upside, it seems the hackers didn’t steal any data, instead using pure harassment to make a point and serve their ideological purposes.
Conclusion
2023 hasn’t been a good year for Europe. In total, over 3.97 billion personal data records were breached from various companies and state institutions across Europe.
The Ukraine-Russia is fueling many of these cyberattacks but typically, it’s profit that drives these threat actors. Data is one of the most valuable commodities in the 21st century. We know it and the hackers know it
Cybersecurity and online awareness have never been more important to our livelihoods than in 2023. It’s no longer an option to secure our online presence. We either do it or we suffer at the hands of cyber-terrorists.
Stick with PrivacyAffairs to remain up-to-date with the comings and goings of cybercrime and cybersecurity, and you’ll have taken your first step toward true digital independence!
Sources
Statista – How Much of a Threat Do You Consider Cyber Attacks to Be to Your Organization?
Statista – Average Cost of All Cyber Attacks to European and North American Firms from 2018 to 2023, by Size
Statista – Average Costs of All Cyber Attacks in the United States and Europe from 2021 to 2023, by Country
CyberNews – DarkBeam Leaks Billions of Email and Password Combinations
Twitter – Andrea Draghetti Post About Luxottica Leak
Electoral Commission UK – Electoral Commission Subject to Cyber-Attack
BleepingComputer – Motel One Discloses Data Breach Following Ransomware Attack
The Guardian – JD Sports Hy by Cyber-Attack that Leaked 10M Customers’ Data
Pole Emploi – Un prestataire de Pôle emploi victime d’un acte de cyber-malveillance
CyberNews – Russian e-Commerce Giant Exposed Buyers’ Delivery Addresses
BleepingComputer – Deutsche Bank Confirms Provider Breach Exposed Customer Data
Tech Crunch – Shadow Silent on Data Breach as Hacked Data Appears Genuine
Independent – Thousands of Drivers Have Sensitive Data Exposed to Hackers in Major IT Breach
Swiss Info – Data Leak Affects 425,000 Swiss Abroad
BleepingComputer – Vodafone Italy Discloses Data Breach After Reseller Hacked
Murcia Today – Cyberattack on Orange in Span Exposes Sensitive Customer Data
BitDefender – Hackers Disrupt 24 Hours of Le Mans Virtual eSports Event
Twitter – KLM Customer Post About the Data Breach
HIPAA Journal – NortonLifeLock Warns Customers About Potential Password Manager Breach
BleepingComputer – Norwegian Government IT Systems Hacked Using Zero-Day Flaw
CyberNews – NoName Hacker Group Targets Italy’s Top Tier Banks

