LockBit Attacks Israel and Peru
The infamous LockBit attacked Peru and Israel in daring hits that made huge waves in the media. Especially in Peru, since the cyberattack targeted the very National Police department, leading to loss of critical confidential data.
- The Israel hit targeted PRONAT industries, a world-renown manufacturer of parts for electronic devices
- LockBit is a ransomware cyber actor that clones, encrypts, and downloads the victim’s data, holding it ransom until the payment is made
- LockBit ranks as the most aggressive and popular ransomware actor, being responsible for over 1,000 attacks over the past 12 months
- The next in line is BlackCat with just under 400 attacks, which highlights LockBit’s amazing effectiveness and aggression
The attacks come in a troubled time, especially for Israel, as the country is dealing with the ongoing conflict. The fact that LockBit took on the Peruvian Police is evidence that the threat actor is becoming more aggressive with time.
Until recently, LockBit preferred to stick to attacking private companies, rather than state-owned ones.
The information about the two attacks was published by LockBit itself shortly after the events took place. In both cases, the attacker claimed that it had managed to steal, download, and encrypt all of the data it had access to.
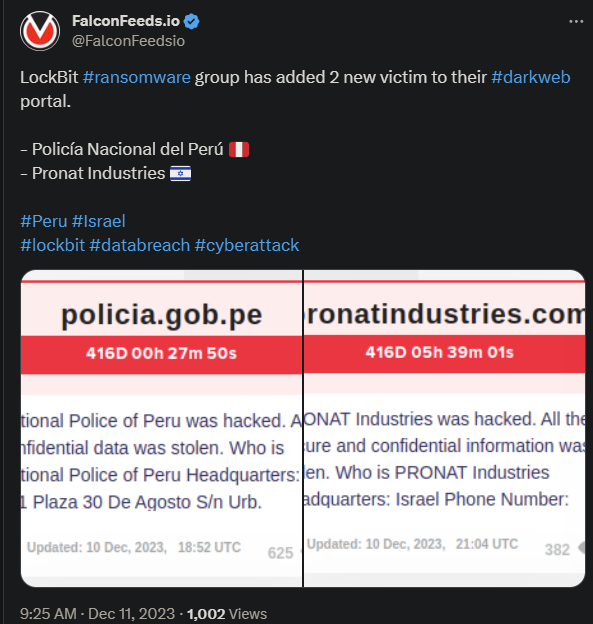
This wasn’t confirmed yet, but the attacks seems to be real. Knowing how LockBit operates, the possibility that the victims lost important data is more than likely.
Who is LockBit and How Does It Operate?
LockBit first emerged into the public sphere in 2019, making it one of the most enduring cyberthreat actors on the market. Especially when considering how active LockBit has been since its inception.
It took several months for LockBit to begin operating normally and one year later, in September 2020, the organization announced its own public website.
This is where the group would later post evidence of its attacks and publish the victim’s data in case the latter refused to pay the ransom.
One of the things that makes LockBit so dangerous and difficult to bypass is the continuous upgrade process, allowing the product to adapt to the newly enforced security systems.
LockBit has registered several variants, including .abcd (the original encryption), LockBit 1.0, LockBit 2.0, and so on.
More importantly, LockBit operates as a profit-sharing org. Instead of using its own manpower, it relies on “mercenaries,” cybercriminals who operate as affiliates. These will use LockBit to perform attacks and share the loot with their employer.
Our Mission
We believe security online security matters and its our mission to make it a safer place.

