LockBit Doubles Down with 33 More Breaches
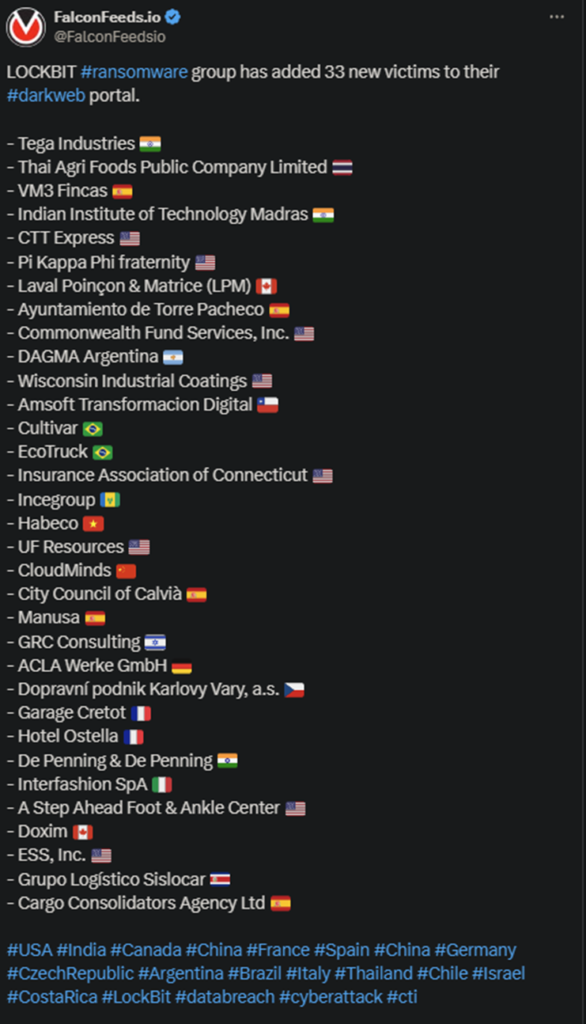
After 2 days of unparalleled attacks, LockBit doubles down with yet another high-profile operation. The victim-count on this occasion: 33. Just like previous attacks, today’s operation also took place across several countries, targeting multiple high-value businesses.
- LockBit has been on a rampage lately, infiltrating large names across multiple industries
- Some of the most prominent targets include DAGMA Argentina, Commonwealth Fund Services from the US, and the Indian Institute of Technology Madras
- The hackers announced the operation on their leak website, providing a short summary for each victim
- There’s no word on how the victims have decided to approach the situation, but it is presumed that at least some will pay the ransom
LockBit has quite a scary record when it comes to the approximate number of hits and their ransom-driven gains. According to a recent FBI report, LockBit had around 2,000 victims and over $112 million in ransom gains in February 2024.
That’s when the Cronos operation took place, which aimed to seize LockBit’s assets and dismantle the organization. That didn’t go well. Not only did the operation fail, and LockBit regained access to its assets within days, but they attacked the FBI itself shortly after.
The gang then resumed their activity as if nothing happened. This is even more interesting, given that most cybercriminal gangs visited by the FBI tend to lay low for a while. Many rebrand themselves or even dissolve, spreading their resources and manpower.
Not LockBit. The FBI also announced that Operation Cronos revealed evidence of a new LockBit version in the making. The 4.0 version was reportedly in advanced stages of development back in February. For now, LockBit is still using the 3.0 version.
How to Deal with a LockBit Attack?
LockBit is quite unpredictable and adaptable so, if the hackers have you in their sight, they will most likely breach through. There are some things you can do to mitigate the risk of a ransomware breach, but no prevention method is perfect.
This is why so many high-profile institutions and businesses with great cyber-defenses fall victim every day. The typical defense involves a mix of competent prevention and education.
Both you and your employees need to be able to detect and avoid traps with ease to begin with. But what if, despite all your efforts, you get breached nonetheless.
At that point, you have 2 options at your disposal: negotiate and pay the ransom or not. The latter appears to be the most pertinent one, but things aren’t as easy as they seem. If they were, we wouldn’t see high-profile organizations paying any ransoms. Which we do.
But why? Paying the ransom puts you on the hackers’ list, making it more likely that you will be breached again in the future. So, why would anyone pay? Well, for one, because of the legal fallout.
Companies that get breached and lose their clients’ data are liable for any damages that may come out of that. It’s only natural that they will try to mitigate that problem by either paying the ransom, not report the breach, or both. In most cases, both.
Ultimately, though, the decision to pay or not to pay comes down to each victim’s assessment of the situation. There’s no universal answer to it.
Our Mission
We believe security online security matters and its our mission to make it a safer place.

