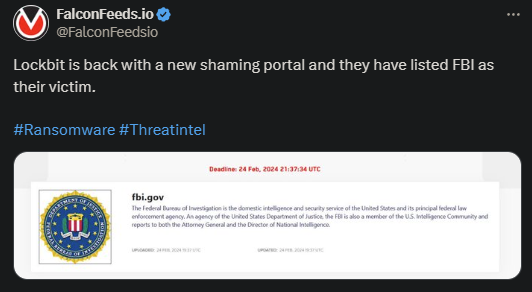
Lockbit Is Back and Attacks The FBI
In an outstanding turn of events, Lockbit announced its return, along with the release of the 3.0 version. Not only that, but the organization’s first victim was the very law enforcement agency that helped bring it down: the FBI.
- FBI conducted a joint operation with their UK counterparts to dismantle Lockbit and seize their website and assets
- The operation called Cronos allowed the FBI to infiltrate the organization and disrupt its website
- Lockbit’s website displayed the message “This Hidden Site Has Been Seized” along with additional information regarding the operation
- However, the success was short-lived because Lockbit bounced back sooner than everyone expected
The organization returned with its 3.0 version and attacked none other than the FBI itself. According to experts, this is meant to be a power play, essentially Lockbit stating that they’re not impressed or intimidated by the FBI’s actions.
This suggests the idea that Lockbit itself is more powerful and capable than initially thought. This isn’t a surprise, though, given that the infamous extortion ring has broken records in pretty much all areas.
According to the FBI statistics, Lockbit is responsible for at least 2,000 victims over the course of their lifespan and at least $120 million in ransom revenue. These are massive numbers by any metric, and they explain Lockbit’s rule in the ransomware sphere.
The recent turn of events sheds even more light on Lockbit’s ability to bounce back and explains how ransomware actors function in general. In most cases, one operation only cannot do enough to eradicate such a massive extortion ring.
Why Was Lockbit Able To Return?
As amazing as Lockbit’s return might seem, this was to be expected among those who are more versed in the field. Ransomware organizations, especially veteran ones, are extremely, if not impossible, to destroy.
While targeted and joint operations like Cronos can disrupt their activity and seize their websites, they can never eradicate them completely. The organization will simply either rebrand itself to confuse law enforcement agencies or split its assets.
Examples like RansomHouse, Hive, and the infamous Russian REvil showcase that very point. While these groups no longer exist in their previous form, they have not exactly disappeared either. Instead, they’ve relocated their assets.
These extortion rings have spread their manpower, systems, and tools to other groups shortly after being taken down. This allows them to continue their work anonymously until the FBI’s radar starts beeping again.
This is exactly what happened to Lockbit recently, with the exception that the group didn’t feel the need to rebrand themselves or take time to reorganize. Instead, they bounced back and immediately went to work.
It is unclear how extensive the attack on the FBI has been, but it is presumed that it wasn’t meant to inflict any meaningful damage. Instead, it was meant to make a statement.
As of now, Lockbit appears to be still active and conducting business as usual. Several new victims have been announced on the group’s public platform, so it’s interesting to observe how the situation will unfold going forward.
Our Mission
We believe security online security matters and its our mission to make it a safer place.

