Lockbit Takes a Trip to Australia
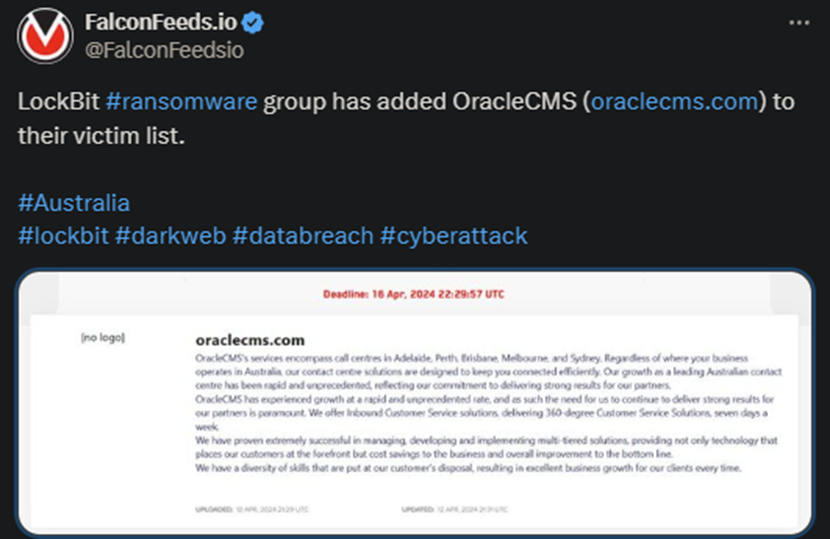
Lockbit hackers have announced a new target, this time in Australia. The victim is OracleCMS that specializes in Inbound Customer Service solutions. The hackers haven’t posted any details regarding the outcome of the operation.
- Lockbit is currently the most infamous, powerful, and dangerous ransomware gang in the world
- The organization was targeted by the FBI in February 2024, working in conjunction with other law enforcement agencies
- The Cronos operation managed to disable Lockbit’s website but only for several days, after which the organization was up and running again
- Lockbit has a reputation for conducting indiscriminate operations and hitting multiple industries all over the world
Ransomware attacks are particularly debilitating and destructive and can cause a lot more than just financial damage. Most ransomware actors, including Lockbit, resort to the double-extortion method.
This means that they will both steal valuable data and encrypt the victim’s system in the process. This forces the victim to negotiate for both the deletion of the data and the decryption key so they can resume their business.
Needless to say, the hackers will provide the decryption key in pretty much all cases. If they didn’t do that, nobody would ever pay the ransom, so they need to give something as a gesture of goodwill.
The problem comes with the second half, as most ransomware organizations won’t actually delete the stolen data. They say they will, but there’s no way for the victim to verify that. And, as data shows, most cybercriminal groups reuse the data to their own benefit.
This means either keeping it to themselves for later use or selling or sharing it with other ransomware groups. This explains why most targets who’ve been hit once will experience recurrent breaches over months or even years.
That’s because they’ve been tagged as “good payers.”
How to Deal with Lockbit?
Lockbit is a very resourceful and competent cybercriminal group. The organization works with some of the best in the business, which explains its high success rate. Lockbit doesn’t necessarily have a higher pay rate, but it does have a higher breach rate than most.
The Cronos operation allowed the FBI full access to the group’s internal structure and code. According to those involved in the operation, Lockbit had amassed around 2,000 victims since the beginning and racked up to $121 million from paid ransoms.
The FBI also unveiled that Lockbit has almost completed its 4.0 version, which they will undeniably release soon. It’s also important to mention that Lockbit is very active and is constantly scanning for potential victims.
While the hackers don’t necessarily go for high-value targets, they do follow the money, wherever that may lead them. So long as the operation is safe for them, allows them to cover their tracks, and comes with massive potential gains, the light is always green for go.
Regarding this last operation, Lockbit gave the victims 4 days to contact them for negotiations. It’s unclear what the victim will decide, but most refuse negotiations, which is exactly what cybersecurity experts advise anyway.
Our Mission
We believe security online security matters and its our mission to make it a safer place.

