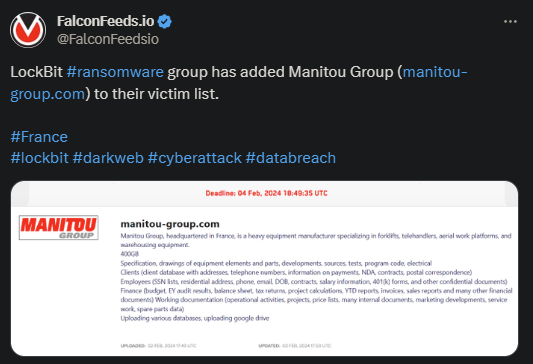
Lockbit Targets French Manitou Group
Lockbit attacked Manitou Group recently and posted evidence of the attack on their leak website. Lockbit is known for its aggression, hardcore negotiation tactics, and ruthlessness, so it’s presumed that the victim will have a difficult time.
- Manitou Group is an equipment manufacturer, specializing in forklifts, warehousing equipment, and aerial work platforms
- Lockbit managed to encrypt and steal over 400 GB of confidential data, which is considerable even by Lockbit’s standards
- The leaked documents feature information regarding contracts, client database, financial records, audit results, and much more
- Manitou Group has a negotiation deadline until February the 4th to reach a consensus regarding the ransom payment
Lockbit has been highly active recently, with multiple attacks taking place several times per week. This is in tone with the recent increasing trend of ransomware attacks and Lockbit is riding the wave.
Ransomware attacks are known to cause damages of tens of millions of dollars, both in ransom payments and financial and reputational damages. Lockbit ranks among the most aggressive ransomware actors with brutal negotiation tactics.
The group is unlikely to show empathy or understanding, which makes it a highly feared name in the ransomware sphere. Despite its inflexible negotiation tactics and relatively high ransoms, Lockbit is still very successful and profitable.
According to a recent investigation, the organization stacked up to $90 million over the course of 3 years, between 2020 and 2023. This is staggering profit in a business where most victims refuse to pay the ransom and prefer to have their documents leaked.
How Lockbit Operates and How To Avoid Ransomware Attacks
Lockbit first appeared on the public radar in 2019 with the .abcd file extension. The ransomware actor laid low for a while, presumably improving its systems, tactics, and procedures. Then, in 2021, Lockbit 2.0 was released.
It’s at that point that Lockbit began to show its true power, targeting both private and public institutions. Victims appeared all over the world and ransoms increased in value exponentially. In one case, Lockbit demanded $10 million as ransom.
A month later, in October of 2022, Lockbit hit Pendragon LLC and asked for $60 million in exchange for deleting the stolen data. These high ransom demands, paired with Lockbit’s extremely sophisticated code and MO, explains quite well the org’s profitability.
But this isn’t the only reason why Lockbit is so feared. The infamous ransomware actor is also extremely active, with close to 2,000 victims to date. It’s also well-known that Lockbit often cooperates with other ransomware groups to boost its reach.
This allows the organization to execute joint attacks and target high-profile institutions. Given the group’s high level of activity, global reach, and veteran status, the fact that it hasn’t been targeted by law enforcement organizations yet is astounding.
When it comes to dealing with ransomware attacks, experts have 2 overarching recommendations: don’t pay the ransom and work with a specialist to improve your security. Paying the ransom doesn’t guarantee that the hackers will delete the data.
Or that they will provide you with the decryption key.
Our Mission
We believe security online security matters and its our mission to make it a safer place.

