Lockbit Targets Two More In The US
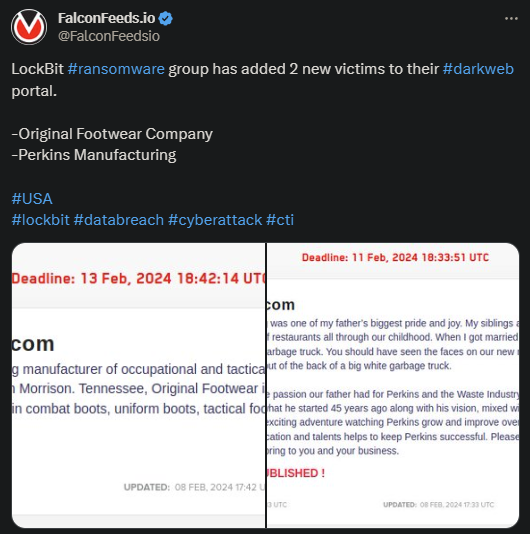
Lockbit infected two US targets recently, Original Footwear Company and Perkins Manufacturing. The attack was purely financially motivated, as is the case with Lockbit’s ransomware attacks.
- According to Lockbit’s original post, Perkins Manufacturing refused to negotiate the ransom
- The company’s stolen files will be leaked publicly on 11th of February
- As shown in the same post, Original Footwear Company either didn’t finalize its negotiations with Lockbit, or they did and accepted to pay
- So far, Lockbit didn’t threaten to publish Original’s leaked documents
It’s unclear how much data was Lockbit able to steal from its victims, but it is presumed to be in the hundreds of GB. This is almost always the case with all Lockbit attacks, as the group never settles for low margins.
As statistics show, Lockbit has increased its activity recently, with several ransomware operations occurring every week. The organization may conduct several attacks a day, hitting multiple targets during more extensive operations.
Lockbit’s attacks are often quite damaging due to the group’s tactics, the tools they’re using, and the double-extortion method. Lockbit always encrypts the victim’s system and clones and steals as much data as it can.
The negotiations then need to resolve the decryption key and figure out a proper ransom for the attacker to delete the stolen data. Naturally, paying the ransom doesn’t guarantee anything, as cyberthreat experts warn time and time again.
Why Lockbit Is So Feared
Lockbit’s aura has grown significantly over time as the organization grew to be one of the most successful and resourceful in the world. Today, Lockbit holds the most number of victims, with over 1,700 stacked over a timespan of 3 years, up to 2023.
The total amount of ransom gains climbed over $91 million within the same period and things don’t appear to slow down. But what makes Lockbit so fearsome and successful?
Several things contribute to Lockbit’s success, including its excellent structure and management. Lockbit appears to have an impenetrable profile, as almost nothing is known about its structure, members, or hierarcy.
Then it’s the fact that Lockbit is always upgrading its systems and tactics, which they have been doing since the very beginning. Lockbit 3.0 uses the trademark Stealbit to automate the exfiltration process, allowing the attacker to steal more data than ever.
This gives Lockbit a lot of leverage during negotiations.
We also need to mention Lockbit’s influence and general tactics. Lockbit usually attacks alone, but that’s not always the case. In some situations, the ransomware actor may form alliances with other cybercriminal groups to increase their influence.
Then we need to discuss the organization’s tactics. Lockbit relies on affiliates, collaborates with other ransomware actors, and even recruits moles from within the very companies they’re targeting. All these tactics make Lockbit extremely effective at its job.
And we can’t forget the data encryption system that, in many situations, is almost impossible to circumvent. This explains why many victims are willing to pay the ransom than lose everything.
While Lockbit’s future is uncertain, there’s no denying that the cybercriminal ring is doing just fine today.
Our Mission
We believe security online security matters and its our mission to make it a safer place.

