Massive Data Leaks Recorded At Top American Universities
An unknown cybercriminal actor posted evidence of major data leaks from 4 high-end US universities.
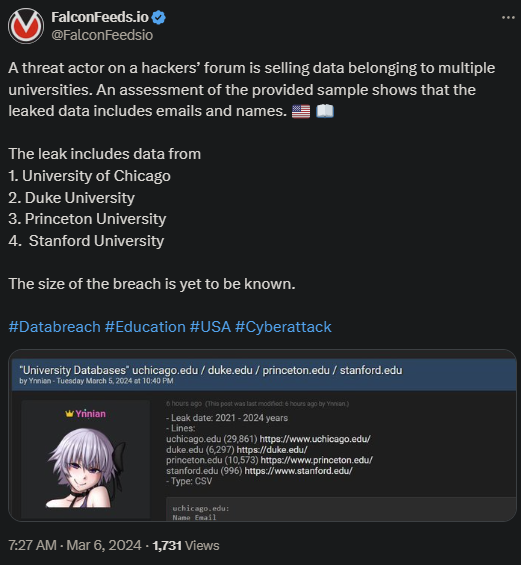
- The OP’s name is simply Ynnian, and it’s unclear if this is an individual or a cybercriminal ring using an alter-ego
- It’s also unclear whether the leak was linked to a DDoS or a ransomware attack
- The 4 universities mentioned in the original post are Princeton, Stanford, Duke, and University of Chicago
- The original post also showed that the leaked data spreads across 4 years, between 2021 and 2024
An interesting aspect to note is that OP didn’t post the leaked documents in their entirety. Instead, they only leaked a sample containing detailed information about emails, names, students, financial reports, and other sectors.
This may suggest that this is a ransomware operation, as this is typically how ransomware leaks work. The hackers will first threaten the victim by posting the data publicly. If the victim doesn’t budge, they will first publish a sample of the data.
If that doesn’t work either, they will eventually leak the entire batch.
This appears to be the likeliest explanation, given that the post was opened on a hackers’ forum. As for why the original culprits would hide their identities, that’s rather self-explanatory. Especially when considering the FBI’s activity lately.
The notorious US-based law enforcement agency has conducted several high-profile operations to dissolve notorious ransomware and DDoS organizations. The first one on the menu was Lockbit after the FBI seized their website.
The operation called Cronos failed several days later, though, with Lockbit announcing its return in full.
The most recent one appears to have brought down the infamous ALPHV ransomware, although more information is necessary to confirm the event. Operations like these explain quite well why cybercriminal rings have everything to gain from hiding their identities.
How Do Ransomware Groups Operate?
The term “ransomware” has flooded the public conscience lately, given the numerous cybercriminal operations taking place. Ransomware groups fit several categories depending on their organization, structure, MOs, and preferred victims.
Some focus on low-to-medium-value targets to ensure an easier breach. Others focus only on high-value targets to maximize profits and run away with as much valuable data as possible. The general MOs also vary dramatically.
Most ransomware actors rely on standard phishing methods, but others can even infiltrate legitimate software and platforms to deceive unsuspecting clients. It all depends on the group’s knowledge, resources, and interests.
However, the extortion part works pretty much the same with all ransomware actors. The victims receive a ransomware note which contains the hackers’ contact details. The victim is guided to a TOR platform where negotiations are supposed to take place.
Long story short, you either pay the ransom, or the hackers will publish the stolen data online. This can have a cascading effect, with other hackers picking up the data and using it to expose additional vulnerabilities to use in future attacks.
That being said, cybersecurity experts advise against negotiating with the hackers anyway. Doing so only incentivizes them to continue their activity and even expand their operations with time.
Our Mission
We believe security online security matters and its our mission to make it a safer place.

