MEDUSA Ransomware Actors Hit Multiple Targets
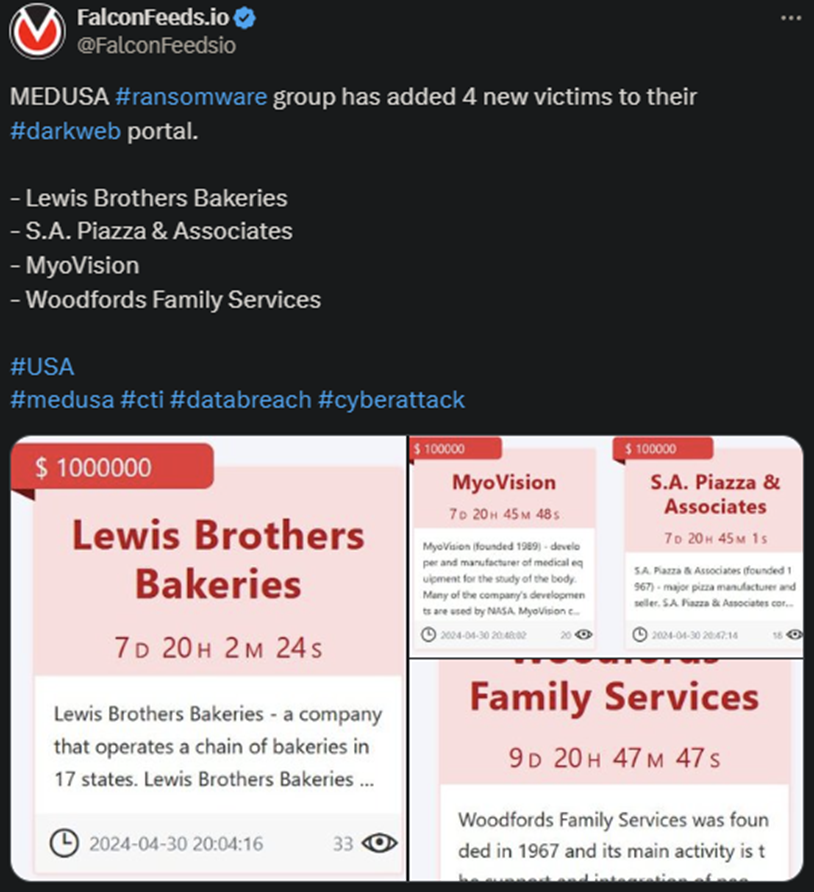
The MEDUSA ransomware gang announced another high-profile operation, during which they breached 4 targets. All of them are US-based and activate in different industries.
- According to MEDUSA’s original post, the victims have between 7 and 10 days to contact them for negotiations
- All targets are high-profile corporations, with Lewis Brothers Bakeries being the largest one, operating a chain of bakeries throughout 17 states
- MEDUSA operators use the multi-extortion strategy to submit victims into paying the ransom
- The organization also has a unique approach in the ransomware sphere by providing its victims with several payment options
MEDUSA posts news about their recent attacks on their public leak platform (the Medusa Blog), where they offer a unique set of options. Victims can ask for the deletion of the data, download the stolen data themselves, or buy time.
Everything is for a price, of course, as MEDUSA doesn’t do charity work.
The hackers also typically post the ransom publicly, which is what they did in today’s operation as well. Lewis Brothers Bakeries got it the worst, as their ransom is seemingly set at $1 million.
MEDUSA currently ranks as one of the most dangerous ransomware gangs in the world. Despite not being as active as other infamous organizations (e.g. LockBit), the gang makes up for it by targeting high-profile businesses almost exclusively.
The operators also employ a multi-extortion tactic, encrypting the victim’s files and stealing data for ransom. If the victim refuses to pay, MEDUSA will leak the data publicly. This can impact the victim’s reputation considerably.
Should You Pay MEDUSA?
The simplest answer would be no, because that incentivizes the hackers to stay in business. But the situation is more complicated than that. Some victims are simply left no choice if the data is especially sensitive.
In many cases, victims don’t necessarily pay to prevent the public data leak, but to recover it to begin with. This is usually the case with victims that cannot overcome the encryption system or they’re racing against time and need the data ASAP.
This is exactly what the MEDUSA hackers are counting on. Which is why they offer the victims the option to pay to download the data. The price tag varies depending on the victim’s revenue profile, typically between $50k and $500k.
The standard recommendation is to ignore the hackers altogether and take the hit coming with the public exposure. There are several reasons for that, but the most important one is that it will happen anyway.
As cybersecurity experts explain, paying the ransom doesn’t guarantee that the hackers won’t leak the data publicly. In most cases, they will. First, because the victim can’t verify that they’ve kept their word. They can then attribute the data leak to other sources.
Second, because doing so comes with financial incentives. The hackers can either sell the data to other entities or make it available for free, but gain reputation in exchange. The conclusion is simple: don’t negotiate with the hackers!
Our Mission
We believe security online security matters and its our mission to make it a safer place.

