MEDUSA Ransomware Attacks US Target
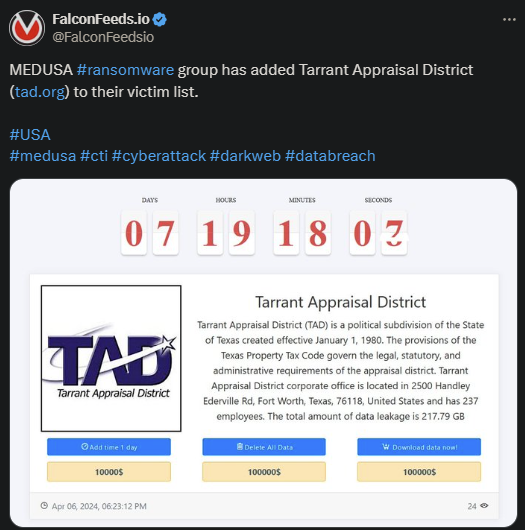
MEDUSA ransomware gang announced another victim on US soil: Tarrant Appraisal District. This is a political subdivision of the State of Texas. It’s unclear how damaging the attack has been or whether the victim has decided to negotiate.
- MEDUSA is often mistaken for the defunct MedusaLocker, but there’s no connection between the 2 apart from the name similarity
- The hackers use the double-extortion technique, encrypting the victim’s system and stealing sensitive data
- Unlike other ransomware actors, MEDUSA operators also provide the victim with several options to recover their data
- Ransomware attacks are on an upward trend in terms of frequency and severity compared to 2022
MEDUSA posted about the attack on its public platform, informing the victim that they have approximately 8 days at their disposal to contact its operators. If the negotiations aren’t completed within that timeframe, the hackers will publish the stolen data publicly.
According to the OP, MEDUSA hackers were able to secure close to 220 GB of sensitive data. The victim has several options at its disposal in addition to completing the negotiations.
This includes extending the period for 1 day at a time in exchange of $10,000, request the deletion of the data for $100,000, or download the data for $100,000.
Unlike most ransomware actors, MEDUSA appears to be very transparent and straightforward, publishing a lot of information in their posts. They post the value of the ransom, information about the victim, their revenue, payment options, etc.
This shows both the gang’s confidence and their unwillingness to negotiate the value of the ransom. MEDUSA operators usually demand low ransoms, based on the victim’s payment capabilities, but will rarely (if ever) agree to a lower sum.
How Dangerous is MEDUSA?
MEDUSA first appeared in July, 2022 but grew exponentially over the next year and a half. Today, MEDUSA ranks as an adaptable, resourceful, and advanced ransomware gang with impressive tactics and a scary profile.
According to recent data, MEDUSA prioritizes several industries during its operations. These include high technology, education, manufacturing, and healthcare. Real estate, governmental institutions, and pharmaceutical companies rank last.
The organization also sticks to the US as their primary hunting grounds, but also conducts operations across the UK, France, Italy, Spain, Canada, and numerous other countries. In terms of actual strategy, MEDUSA keeps things simple.
The hackers will use phishing emails to lure unsuspecting victims and breach their systems. They will then encrypt the victim’s system, disable the defensive programs, and steal the target data. The more data is stolen, the higher the ransom will be.
Cybersecurity professionals warn against paying the ransom, though, or even negotiating with MEDUSA representatives. That’s because nothing good can come out of it. Being willing to negotiate will show the hackers that you are vulnerable and willing to pay.
This effectively paints a target on your company for future breaches. Not only that but paying for the deletion of the data doesn’t guarantee that the hackers will actually delete it. In fact, records show that most ransomware groups won’t.
Instead, they will either keep it for later use or sell it to other cybercriminal gangs.
Our Mission
We believe security online security matters and its our mission to make it a safer place.

