MEDUSA Ransomware Infected 93-Year-Old Company
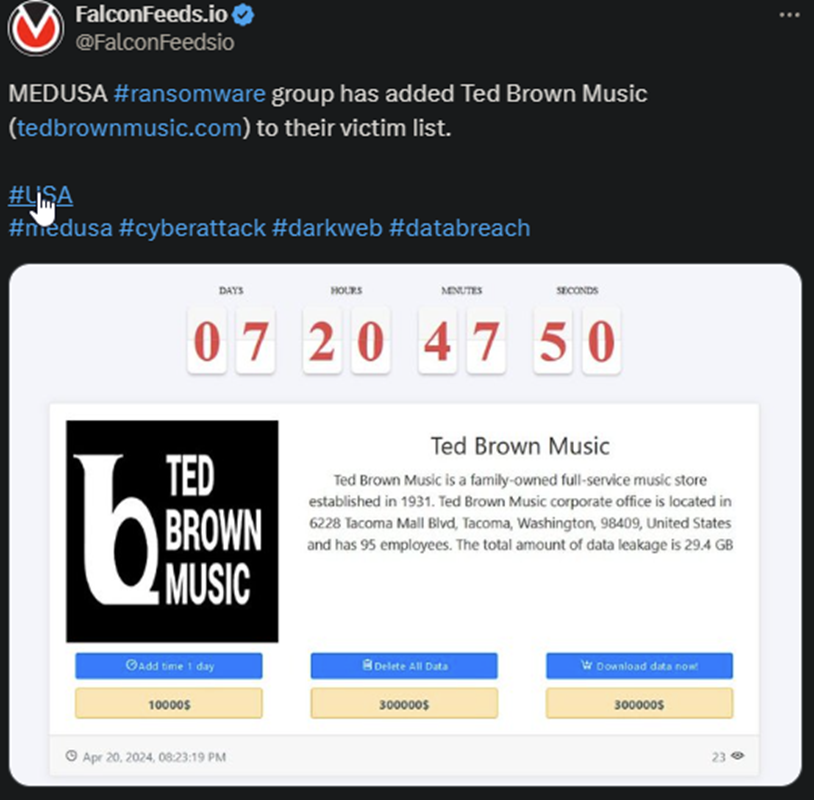
MEDUSA operators announced that they had just breached Ted Brown Music, a US-based music store with almost a century of existence. According to the original post, the company has 95 employees and is a family-owned and operated business.
- The total amount of the leaked data is allegedly around 29.4 GB, but hackers haven’t disclosed the content of it
- Ted Brown Music hasn’t commented on the incident, so it’s unclear if they’ve decided to negotiate or ignore the hackers
- MEDUSA is known to demand high ransoms and employ a ruthless encryption tool
- Ransomware attacks are on an upward trend after falling dramatically in intensity over the past 5 years
MEDUSA’s tactics and MOs have changed gradually over time, along with the gang’s activity levels. The now-infamous ransomware actor first hit the public sphere in 2022, but it only gained global notoriety a year later.
The hackers advertise their software as a RaaS (Ransomware-as-a-service), allowing them to rely on affiliates and third-party entities to carry out some of the attacks. This tactic brings in profits with minimal risks and almost no effort.
MEDUSA operates based on a multi-extortion strategy, which is an upgrade from their simple extortion practices during their first few months of activity. The double-extortion method refers to the hackers both employing an encryption tool and stealing data.
The victim is then forced to negotiate for both, which naturally increases the value of the ransom. But how effective is MEDUSA, and should you be worried?
Why MEDUSA Ransomware is a Global Concern
In short, yes, you should be worried about it. The MEDUSA gang took its time to develop its code, tactics, and strategy accordingly, so that, today:
- They employ high-end stealth and diversion tactics
- They target and breach even high-value targets with top security
- They use legitimate software for malicious purposes
- They are notoriously difficult to track and flag accordingly
Another interesting feature that most ransomware actors don’t have is the multi-payment option. MEDUSA’s victims have several payment options at their disposal, in case they want to:
- Extend the time limit by a day
- Download the stolen data
- Ask for the deletion of the data
The 1-day extension is typically $10,000, but the value of the other 2 options varies, depending on the victim’s profile. These can range from $10,000 to $500,000 or more.
More importantly, the MEDUSA hackers don’t necessarily target high-profile institutions. Instead, they go for high-value ones that pack serious revenue. The hackers always follow the money, which is a reason for concern for everybody, regardless of their status.
If you believe you fit the profile of a potential victim, you need to act sooner rather than later. Nothing beats prevention in terms of safety, especially when we’re talking about a ransomware gang as effective and versatile as MEDUSA.
The problem is that boosting your cyber defenses optimally on your own is, at best, unlikely. Which is why it’s typically recommended to rely on cybersecurity experts for that.
Also, make sure you educate your staff, and yourself, with respect to the potential dangers coming with using even legitimate software and platforms.
Our Mission
We believe security online security matters and its our mission to make it a safer place.

