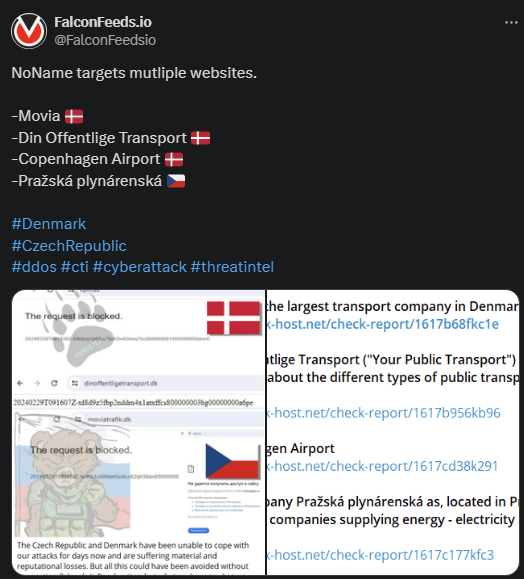
NoName Breaches Denmark and Czech Republic Again
NoName is continuing its crusade against Denmark and the Czech Republic with a series of new attacks. This time, NoName’s operations produced 4 victims, including the Copenhagen airport.
- NoName published evidence of its attacks and mocked the victims in the post
- As stated by the hackers themselves, these attacks were fueled by Denmark’s and the Czech Republic’s aid granted to Ukraine
- NoName is the most (in)famous pro-Russian cybercriminal organization that only targets those who they view as enemies of the Moscow regime
- It’s unclear how damaging the attacks have been or whether the victims have restored their systems
NoName has been on a relentless campaign against Denmark, Czech Republic, and Italy over the past several weeks. The organization has sometimes racked up to 8 victims within 24 hours.
Most of these attacks are mild inconveniences, as they are relatively easy to overcome, but that’s by design. NoName is known to value quantity over quality in most cases. They only deliver heavy blows with lasting effects when they deem it absolutely necessary.
NoName’s activity has spiked over the past 2 months, with the group attacking more targets daily than ever. This is a result of the organization’s military-like discipline and the members’ extensive knowledge and work power.
Denmark has yet to make an official statement regarding the relentless attacks, despite going on for more than a week.
Why NoName Is The Biggest DDoS Threat
That would be the gang’s ability to conduct massive DDoS operations against the US, Ukraine, Lithuania, Germany, Norway, and numerous other European states from day one. This is inconsistent with the typical DDoS actor.
Some have explained this peculiarity by speculating that NoName is actually state-funded. The theory says that the Russian government itself is either funding the group or operating it directly.
This would explain not only the group’s general MO (targeting news sites and public institutions almost exclusively) but its resourcefulness as well. According to insider leaks, NoName is very well-funded and uses the most advanced tools available.
The group’s structure also appears to be highly militarized in the sense that the members are very disciplined and work on unforgiving deadlines.
These features allow NoName to often target up to 15 institutions per day, sometimes more. Despite not causing significant damage, NoName’s operations are still extremely disruptive and concerning.
In many cases, NoName’s attacks have been known to knock the victim’s operations out for more than 3 weeks. Such attacks can cause significant financial and reputational damage.
To be noted, while NoName prefers to target public institutions, they often attack private corporations as well, so long as they deem them enemies of Russia. If you think you qualify as a potential victim, now is the time to work on your cyber defenses.
Our Mission
We believe security online security matters and its our mission to make it a safer place.

