NoName Breaches Czech Republic and Poland Again
NoName’s rampage is nowhere close to the end. The cybercriminal gang just announced another massive operation against the Czech Republic and Poland. This time, the group infiltrated 7 victims across both states.
- As NoName themselves stated, the hacking actor is on a European tour, hitting primarily anti-Russian entities
- This most recent operation recorded 7 victims, and most were transportation companies
- NoName hits targets both in the public and the private sector but prefers governmental institutions above all else
- The organization’s self-stated purpose is to push pro-Russian narratives and dismantle those that oppose them
Despite qualifying as one of the most dangerous and active cybercriminal organizations in the world, NoName’s breaches aren’t particularly devastating. It’s no secret that NoName hackers prefer quantity over quality.
Some anonymous internal leaks have shown that NoName prioritizes hitting multiple targets in a short time span. This tactic is meant to spread terror and confusion across multiple states, which will undoubtedly boost NoName’s infamous status tremendously.
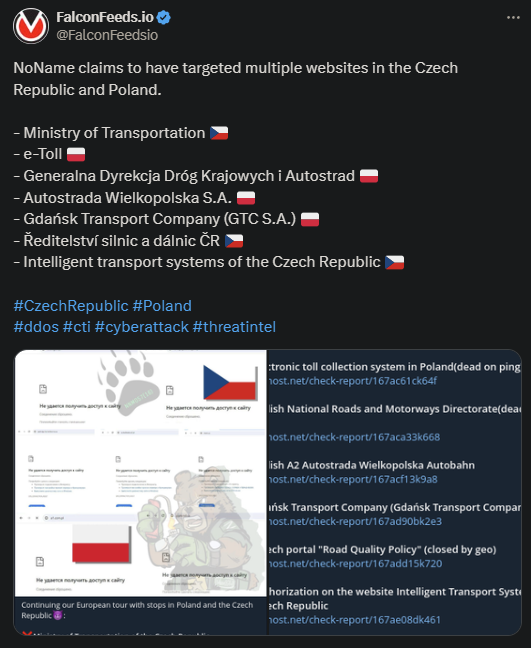
As this recent operation showed, NoName likes to attack its targets in bulk. This tactic spreads the attention of law enforcement agencies thin, which explains why NoName has been virtually untouchable so far.
The Czech Republic and Poland have been on NoName’s radar for a while now, and they’ve went through a variety of DDoS attacks over the past 2 years. That being said, NoName has an extensive list of potential targets, which is constantly expanding.
What Does NoName Want?
NoName took off in March of 2022, immediately after Russia invaded Ukraine. The organization describes itself as pro-Russian, serving the Kremlin’s political and ideological goals. Ukraine itself was NoName’s primary target for a while until others followed suit.
Since its inception, NoName has conducted hundreds of attacks on numerous states like Lithuania, Estonia, Ukraine, Poland, Germany, Italy, and France. 2023 alone recorded more than 170 attacks between January and September.
However, since then, NoName’s activity increased dramatically, with more countries vowing to support Ukraine during the ongoing war. This most recent batch of attacks falls in the same category.
Both the Czech Republic and Poland have aided Ukraine during the war and prepared long-term military and humanitarian packages. The “Europe Tour” that NoName mockingly mentioned in their original post alludes to this aspect.
It also alludes to the organization’s terror campaign against the West’s efforts to support the Ukrainian government against Russia’s aggression. And NoName isn’t all talk. The cybercriminal group has conducted hundreds of operations against Russia’s enemies.
The organization’s preferred method of attack is utilizing botnets to flood the system with requests and force a shutdown. NoName uses its trademark DDOSIA tool for that, which represents the group’s primary cyberhacking tool.
But what makes NoName truly dangerous is its military-like discipline and structure. The organization works with some of the best hackers on the market and has clear-cut goals to achieve. One of them is to secure between 5 and 15 successful breaches per day.
This explains why NoName currently ranks as the most active cybercriminal gang in the world. And why the situation isn’t likely to change anytime soon.
Our Mission
We believe security online security matters and its our mission to make it a safer place.

