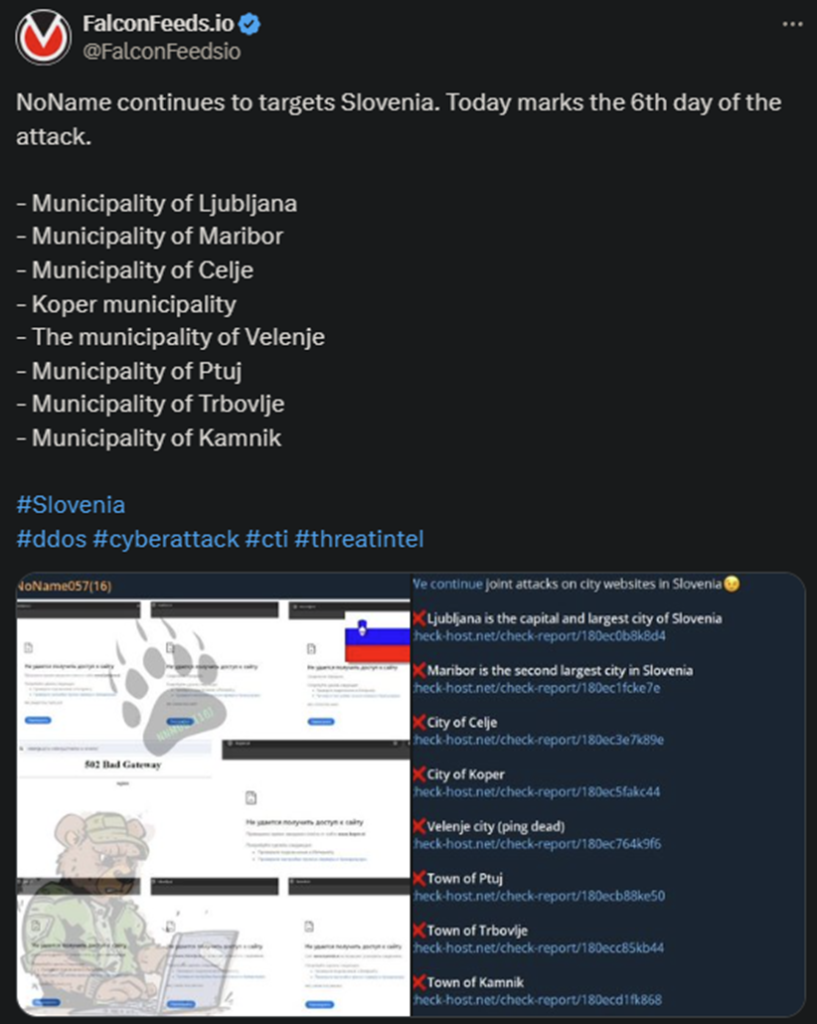
NoName Continues its Slovenian Offensive
NoName has now entered its 6th day of attacking Slovenia’s infrastructure. The hackers are responsible for breaching no less than 8 targets, all being public institutions. Some of these are the Municipality of Maribor, the Municipality of Ljubljana, and Koper Municipality.
- The NoName gang has been on an almost week-long crusade against Slovenia, targeting the public sector daily
- In most cases, the attacks have been limited to standard DDoS breaches, which took down the victims’ websites
- Slovenian representatives haven’t commented on the incident yet, but they have addressed previous attacks
- Slovenia has attracted NoName’s attention ever since Natasa Pirc Musar, the president, reinforced the country’s support for Ukraine
Cyber-breaches are standard attack MOs in wartime, whether the targeted nations are directly involved in the conflict or not. NoName has been targeting both Ukraine’s infrastructure and that of its allies.
The goal is to spread fear and panic and create enough damage to discourage Ukraine’s allies from supporting it. It not always work, but NoName’s operations do have a visible and quantifiable impact. Especially when the gang joins forces with other actors.
NoName has often joined forces with other cybercriminal rings and affiliates to make an even larger impact. This tactic also allows NoName to hit multiple targets at once with minimal effort.
But what does this most recent operation say about NoName? It says that the gang is extremely unpleased with Slovenia’s support of Ukraine. There’s no denying that Ukraine has a lot of supporters all over the world, which means NoName has its hands full.
Slovenia isn’t the first to endure NoName’s wrath over the course of multiple days and even weeks. The same happened with the Czech Republic, Germany, France, and Poland, to name a few.
How to Defend Against NoName?
Unfortunately, there isn’t much you can do in this sense. But you also don’t need to worry too much if you’re not a heavy player at a global scale and support Ukraine at the same time. NoName only conducts politically and ideologically driven operations.
If you are, your best course of action is to prepare to mitigate the damages once the breach has occurred. NoName is a very competent organization, working with highly-knowledgeable professionals. If they want something, they will eventually get it.
The good news is that NoName’s attacks aren’t particularly debilitating. Most victims can resume their activity shortly after with relative ease, because NoName’s goal isn’t to cause a lot of damage. Instead, it’s to send a message.
As the group itself states with every new attack it conducts, they aim to protect Russia’s image and integrity. To achieve this goal, the hackers will use all of the tools at their disposal. These include misinformation, propaganda, intimidation, blackmail, and DDoS attacks.
If you believe you qualify as a potential target, your best course of action is prevention. Collaborate with actual cybersecurity experts to probe your defenses and identity and fix any potential vulnerabilities. If specialists can detect them, NoName can too.
Our Mission
We believe security online security matters and its our mission to make it a safer place.

