NoName Goes on a Rampage in Latvia
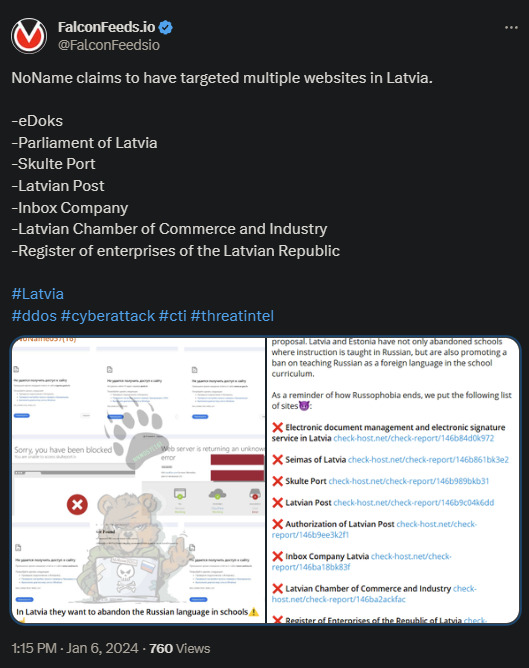
NoName reaches Latvia and manages to infiltrate 7 targets in a rapid succession, including the Parliament of Latvia and the Register of Enterprises of the Latvian Republic. This is consistent with the group’s infamous aggressiveness.
- The attack seems highly coordinated and premeditated
- The initial theories suggest the existence of multiple attackers, as NoName is known to often join forces with other cybercriminal organizations
- As stated by NoName itself, the attacks were ideologically motivated, which is why the main targets were public institutions
- In their letter, NoName accused Latvia of harboring anti-Russian sentiments and wanting to eliminate the Russian language from schools
Neither of the victims involved in the attack made any public statements. The outcome of the attacks and the financial or logistical damages that followed are still uncertain.
NoName is known for its aggression, complex MO, and tendency to collaborate with other hacktivist entities like Killnet and Xaknet. This allows the group to target high-profile institutions, including in the public sector.
According to its own statements, NoName is not financially motivated. Instead, its goal is to push pro-Russian propaganda and attack those who stand against Putin’s regime. This recent attack wasn’t the only one where Latvia was the target.
The Latvian government was attacked in 2022 as well, when NoName froze the online train ticket sell system. This forced the company to stop selling tickets on site and online until the issue was fixed.
Who Is NoName?
NoName is a pro-Russian cybercriminal group that was founded in March of 2022, at the beginning of the Ukraine-Russia war. The organization immediately declared war on all anti-Russian governments and entities and got to work within the same month.
Ukraine was the first to be hit, more precisely the Zaxid and Facty UA media organizations. Many Ukrainian media employees also received threatening letters from NoName directly, asking them to cease their activity.
Since then, the group expanded its sphere of influence and began hitting targets worldwide. NoName now uses its own DDoS tool called DDOSIA, which functions based on flooding the target network with requests.
Despite the group’s high activity and defiant public presence, not much is known about its structure or the identity of those involved. NoName even has a Telegram channel where it posts threats, highlights targets, and posts evidence of the recent attacks.
Their goal is to push pro-Russian propaganda and silence the opposition by any means necessary.
Our Mission
We believe security online security matters and its our mission to make it a safer place.

