NoName Hackers Hit Multiple Targets in Greece
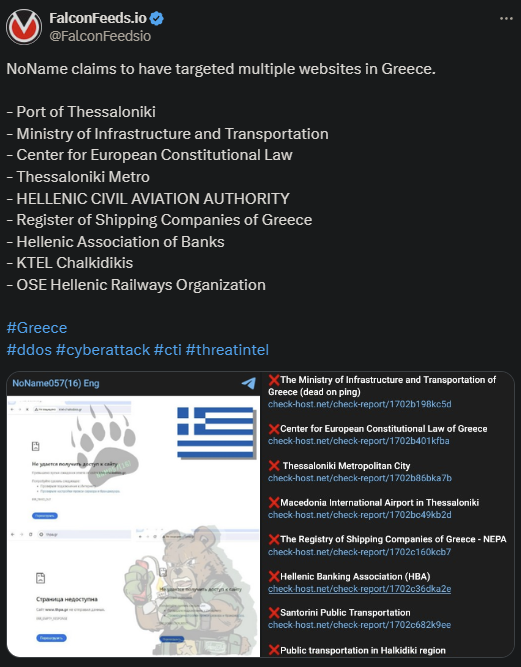
NoName targeted Greece with a new organized cyber-hacking operation, this time infiltrating 9 institutions. This is one of the largest hacking operations that NoName has launched against Greece.
- According to NoName’s original post, all of the websites affected by the attack were taken offline
- None of those targeted by NoName issued any public comment so far
- It is unclear how damaging the attacks have been and whether the hackers ended up in the possession of any stolen data
- NoName has been attacking multiple targets across the world since its inception and all of its attacks are politically and ideologically motivated
Some of the Greek targets infiltrated by NoName include the Register of Shipping Companies of Greece, the Thessaloniki Metro, the Port of Thessaloniki, and the Center for European Constitutional Law.
NoName prefers to hit governmental institutions as much as possible, because the goal is to impact the country’s government directly. It’s being doing so against Ukraine, as well as all of its Western allies since the beginning of the Ruso-Ukrainian war.
While this recent attack seems massive, with successful breaches, this isn’t an extraordinary feat for NoName. According to anonymous inside leaks, the cybercriminal gang runs an almost military-type structure in terms of discipline and organization.
The hackers have around 5 to 15 potential targets to assess and test per day to look for weaknesses and determine their viability. This, combined with the organization’s resourcefulness, explains the high daily victim count that NoName is known for.
Is NoName a Russian Puppet?
Some think as much. NoName first appeared in March of 2022, which was no coincidence. This was shortly after Russia invaded Ukraine and NoName immediately admitted its pro-Russian allegiance.
Immediately after their public post, NoName started orchestrating attacks against Ukraine. Multiple such hits were aimed at mass media trusts, trying to discredit Ukraine’s public credibility.
Interestingly, the hackers didn’t limit themselves to DDoS attacks. They also sent actual letters to mass media representatives to threaten and intimidate them. This would eventually become a common tactic for NoName, which uses multiple intimidation techniques.
DDoS attacks remain the main weapon, though, given that they can be quite debilitating and produce long-term effects. Despite that, NoName isn’t keen on inflicting lasting damages. Instead, the gang prioritizes quantity over quality.
The hackers will hit as many targets as possible to instigate panic and fear and spread their message as far as possible. NoName operates based on political and ideological ideas, so its main prerogative is to spread them as much as it can.
That being said, NoName doesn’t hit governmental institutions exclusively. They will also target private institutions, whether they have supported Ukraine or not. Any public or private institution is green-lighted, so long as it’s located in the target country.
So, is NoName a Russian puppet? While there’s a lot of circumstantial evidence pointing at that, no definitive one has been found. It does seem like NoName is a very powerful and resourceful cybercriminal ring, but that’s not enough to link it to the Russian government.
Our Mission
We believe security online security matters and its our mission to make it a safer place.

