NoName Hackers Keep Pounding Ukraine Infrastructure
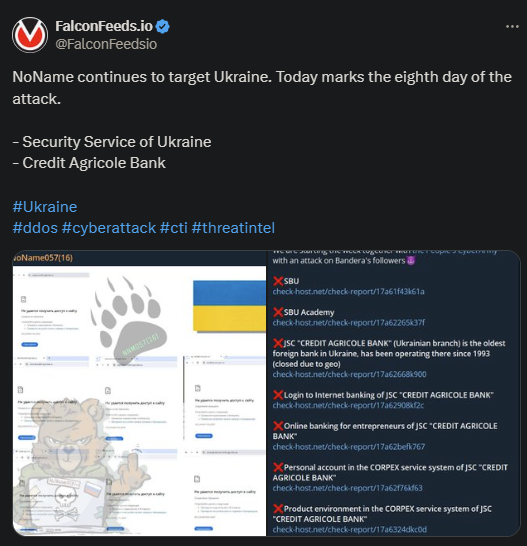
NoName has entered day 8 of attacking Ukraine’s infrastructure and it shows no signs of stopping. The hackers posted another public statement, mocking Ukraine’s cyber-defenses and showcasing several more victims.
- Some of the infrastructure branches hit by the hackers include the Ukrainian Security Service, the SBU Academy, and the Credit Agricole Bank
- NoName is the most active anti-Ukrainian cybercriminal gang, active since the beginning of Russia’s invasion
- The cybercriminal organization makes political and ideological demands with the purpose of intimidating Ukraine’s supporters
- The group is known to prioritize governmental institutions but has also hit private corporations that provided aid to Ukraine in any capacity
It’s unclear how damaging this last operation has been to the Ukrainian infrastructure, and nobody on the Ukrainian side has commented on the event. Cyberattacks have become the norm since February 2022, when the Russian invasion began.
This isn’t a new tactic for the Russian government either, as Russia has been practicing cyber warfare since the concept first emerged. That being said, NoName isn’t associated with the Russian government, despite many claiming otherwise.
NoName’s reputation has spread like wildfire since March 2022, when the hackers made their first public appearance. NoName’s goal has been clear from the beginning: target anyone who opposes the Russian government or supports the Ukrainian one.
The pro-Russian gang has hit numerous targets since, some multiple times in a row. The same goes for these recent attacks, which are part of a week-long campaign that, so far, has resulted in dozens of victims.
How the NoName Group Operates
NoName relies on numerous tactics to make its message known. The most prevalent one is the DDoS attack where the hackers use bot armies to flood the target website with access requests. The site cannot process the sheer number of requests.
So, it will shut down. This tactic alone can cause serious damage and take the victim’s operations out for days or even weeks. This has happened in several cases.
Other noteworthy strategies include threatening the victims, extorting them in case the hackers get their hands on classified documents, and even sending intimidation letters. It’s safe to say that NoName doesn’t leave any stone unturned in terms of attack strategies.
But NoName’s reputation doesn’t come from their creativity, but their resourcefulness and work power as well. NoName is among the few, if not the only, organizations that produce several victims per day, every day.
This has been going on for more than 2 years, ever since the Ruso-Ukrainian war began. According to unverified sources, NoName operators are demanded to hit between 5 and 15 targets per day. The more they breach, the better.
The cybercriminal gang is always active and typically hits the same target multiple times in a row. Especially if the gang considers the target in question of special interest. This has been the case with several states like the Czech Republic, Poland, and Ukraine now.
It’s important to reiterate that NoName hackers also target private corporations if they show anti-Russian sentiments or support Ukraine in the ongoing war. Especially if they have influence, a large platform, and a considerable amount of power.
Our Mission
We believe security online security matters and its our mission to make it a safer place.

