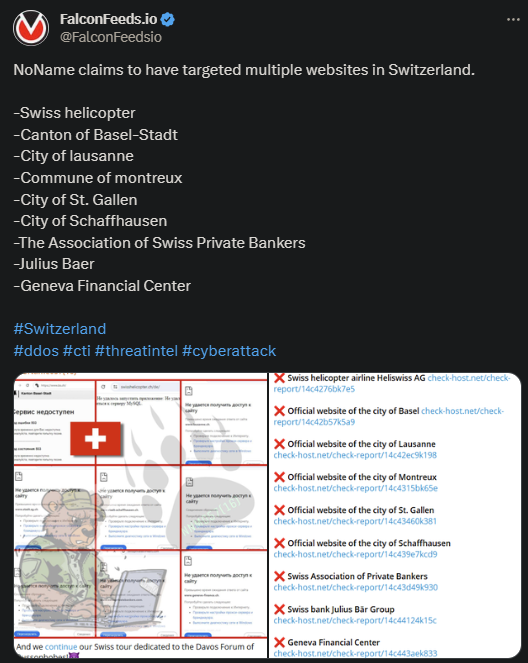
NoName Hits Multiple Targets in Switzerland Again
The infamous Russian hacktivist organization NoName has hit Switzerland again, after it had just hit multiple public and private companies a couple of days ago. This time, the hacking operation created no less than 9 victims.
- NoName is a popular Russian DDoS group set to attack all those who they deem a danger to Russia
- This includes companies from the public and the private sector indiscriminately
- The recent attack involved several offensive operations against City of Lausanne, Geneva Financial Center, City of St. Gallen, and many others
- The aftermath is unclear, but it is presumed that most of the victims restored their systems
NoName is famous for its aggression and innovative capabilities. The organization appears to be heavily financed by Russian sponsors, but it is unclear whether the Russian government itself is involved.
The group is also extremely powerful, using intricate and high-end tools and hacking programs to circumvent even the most potent defensive systems. NoName-related attacks sometimes paralyze their target’s systems for days or even weeks.
The recent rampage was supposedly an answer to anti-Russian sentiments permeating the Swiss community, especially the Davos forum. The same reason was invoked during the first wave of attacks that occurred several days back.
As a result of the attacks, the victims’ website and operations were frozen. Despite NoName not being driven by financial motives, its attacks always inflict drastic financial losses to its victims.
What Are NoName’s Motives?
NoName first became public in March of 2022, at the start of Russia’s invasion of Ukraine. The organization swore to fight against all those who oppose Russia and Putin’s regime and intensified its cyberattacks shortly after their initial post.
The first target was Ukraine, quickly followed by its Eastern and Western allies. The group also doesn’t rely on cyberattacks alone to push their pro-Russian campaign. Several Ukrainian officials have reported receiving threatening letters as well.
NoName’s attacks intensified over time in frequency and brutality, as well as in the number of victims per attack. This suggests that the organization has improved its capabilities and tools considerably since its first hit.
It also suggests that the cyber-threat actor has serious financial backing, with some suggesting that the Russian government itself may be at helm. NoName has a dedicated Telegram channel where it posts recent attacks, threats, and mock targets.
NoName uses several hacking tools, including the trademark DDOSIA, which they use to flood the sites with network requests.
Our Mission
We believe security online security matters and its our mission to make it a safer place.

