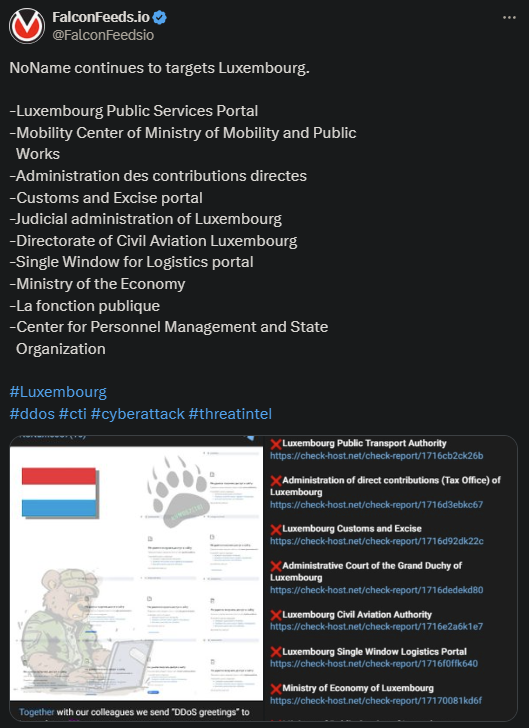
NoName Ravages Luxembourg
NoName continues its rampage against Luxembourg, this time hitting no less than 10 targets. Some of these include Luxembourg’s Public Service Postal, the Customs and Excise Portal, and the Ministry of the Economy.
- All of NoName’s targets are high-value institutions, making this a potentially devastating operation
- The aftermath of the string of attacks is unknown as of now, so it’s unclear how the targeted institutions have responded
- NoName has focused its entire attention on Luxembourg over the past few days, conducting several DDoS operations against it
- The underlying reason is Luxembourg’s open pro-Ukrainian stance, which NoName has been criticized in the past
And it’s not just Luxembourg that NoName has punished for helping Ukraine. The NoName hackers have attacked most of Ukraine’s allies since the beginning of the war, some multiple times over short spans of time.
The cybercriminal ring is self-proclaimed pro-Russian with invested pro-Russian interests and ideals. They have sworn to defend Russia from attackers and even punish those who hold any anti-Russian position.
It’s been that way since March of 2022 when NoName first came public.
NoName made a reputation for itself out of promoting pro-Russian politics and ideals. The group emerged right after Russia’s invasion of Ukraine at the end of February 2022 and pledged allegiance to the Moscow regime immediately.
Their first public post painted NoName as a determined cybercriminal ring with a well-defined goal and impressive tactics. The gang proved very resourceful from the get-go, as they were able to hit multiple targets across the globe simultaneously.
However, NoName often achieved this feat by collaborating with other hacker groups like XakNet and Killnet, which also pushed pro-Russian propaganda. This shows that NoName is well-connected and resourceful, which contributed to its reputation.
How NoName Operates
While there is no clear data on NoName’s internal structure and MOs, there are some anonymous leaks that claim to shed some light on that. Unnamed whistleblowers claim that NoName has a very rigid, almost military-like discipline and schedule.
The hackers are constantly on the prowl, scanning for potential targets, devising operations, and assessing vulnerabilities. The same sources pointed out that NoName hackers are required to target at least 5-15 targets each day.
This explains why the group has been so active and why it always posts multiple targets daily. As records show, the organization prioritizes state-owned companies and public institutions over private corporations.
That’s because NoName’s goal is to attack the target state and send a clear message. The recent attacks aimed at Luxembourg are meant to intimidate the government and cause financial and informational losses.
NoName has claimed that they will do the same to any state supporting Ukraine directly and indirectly, and they often hit the same target multiple times.
On a more interesting note, NoName hasn’t been targeted by the FBI or any other major law enforcement agency since its inception. This suggests that the organization may be state-funded, which provides it with significant resources and power.
Many have linked NoName to the Russian government, but the allegations haven’t been confirmed yet.
Our Mission
We believe security online security matters and its our mission to make it a safer place.

