NoName Reaches 3rd Day of Rampage Against Spain
World-renown cybercriminal organization, NoName, targets Spain for the 3rd day in a row. This time, the organization hit 7 victims in an unprecedented DDoS operation.
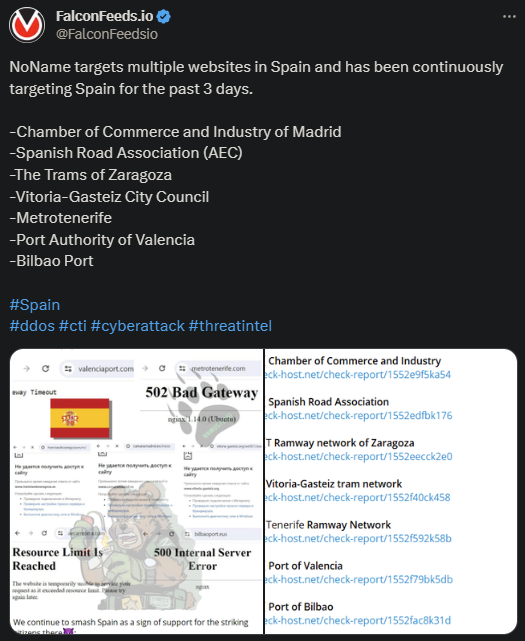
- Most of the victims were public institutions, such as the Port Authority of Valencia, the Bilbao Port, and the Spanish Road Association
- Neither of the victims have released a public statement to comment on the recent events
- According to the initial posts by NoName, the victims’ websites were forced offline by the malware attacks
- NoName justified the attacks by stating their support for the rail workers’ strike
Spain’s social unrest has drawn a lot of eyes recently and NoName is but one of the entities that have decided to act in this sense. NoName has made a name for itself in the political sphere, as the group always showcases political or ideological motives.
The recent string of attacks shows the group’s extreme capabilities, as NoName managed to infiltrate 7 targets in a rapid succession. This suggests the idea that NoName had outside help, as it typically is the case.
The group is known to join forces with other cybercriminal organizations to expand their reach and potential.
Today, NoName ranks as the most feared cybercriminal group for its ruthlessness, resourcefulness, and willingness to attack all targets it deems worthy. They always exploit the victim’s vulnerabilities and always have a detailed plan of attack.
You Should Know This About NoName
The organization was born in March of 2022, immediately after Russia invaded Ukraine. They immediately pledged allegiance to the Russian government and declared war against all those who opposed Putin and his political system.
Which means they have no shortage of targets.
The first attacks began immediately after the group declared itself publicly and aimed at Ukraine’s media outlets. Shortly after, NoName began targeting Ukraine’s allies, including the US, sometimes conducting several attacks per day.
Private investigation entities have looked into NoName and determined that:
- The organization is clearly well-funded and resourceful with some painting NoName as “Putin’s puppet”
- The group often conducts as many as 15 attacks per day
- They often collaborate with other pro-Russian entities like Killnet and Cyber Army of Russia
Moreover, NoName appears to be extremely methodical, with an almost army-like discipline, one which no other cybercriminal group displays. This may explain, at least in part, the group’s success.
Another aspect that contributes to NoName’s success is the group’s determination to improve its systems and tactics constantly. The recent mass attack against Spain showed evidence that DDoSIA was used.
This is NoName’s trademark malware tool that they’ve devised specifically so that they can infiltrate more well-defended targets. Another important trait of NoName’s profile is its educational endeavors.
As seen on its Telegram channel with over 52,000 subscribers, NoName constantly educates its followers on industry jargon and different DDoS attack methods and tools. It’s unclear why they do that. Some suggest this may be part of a recruitment scheme.
Despite its long string of attacks and ferocious activity level, not much is known about NoName’s identity, structure, or members.
Our Mission
We believe security online security matters and its our mission to make it a safer place.

