NoName Returns to Moldova Once Again
NoName continues its Moldovan crusade, this time producing no less than 10 breaches. Some of the websites affected include Republic of Moldova, the State Registry, the Presidency of Moldova (again), and the Government itself.
- News about NoName’s attacks on Moldova has been running in the country for over a week
- The hackers motivated their attacks with the same argument: the Moldovan government displays Russophobic behavior
- In reality, NoName’s motivation is linked to Moldova’s involvement in the Ruso-Ukrainian war to the detriment of the Moscow regime
- NoName has been attacking all of Ukraine’s allies and supporters since March of 2022, shortly after Russia’s invasion started
The Ruso-Ukrainian war has been proven to be the ideal landscape for a multitude of pro-Russian cybercriminal gangs. Out of all of them, NoName appears to be the most powerful, active, and determined. It’s also among the few that show no interest in financial gains.
Instead, NoName is strictly interested in pushing political and ideological goals. The hackers always conduct extensive cybercriminal operations, sometimes lasting weeks, against each target. The attacks on Moldova have been lasting for more than a week.
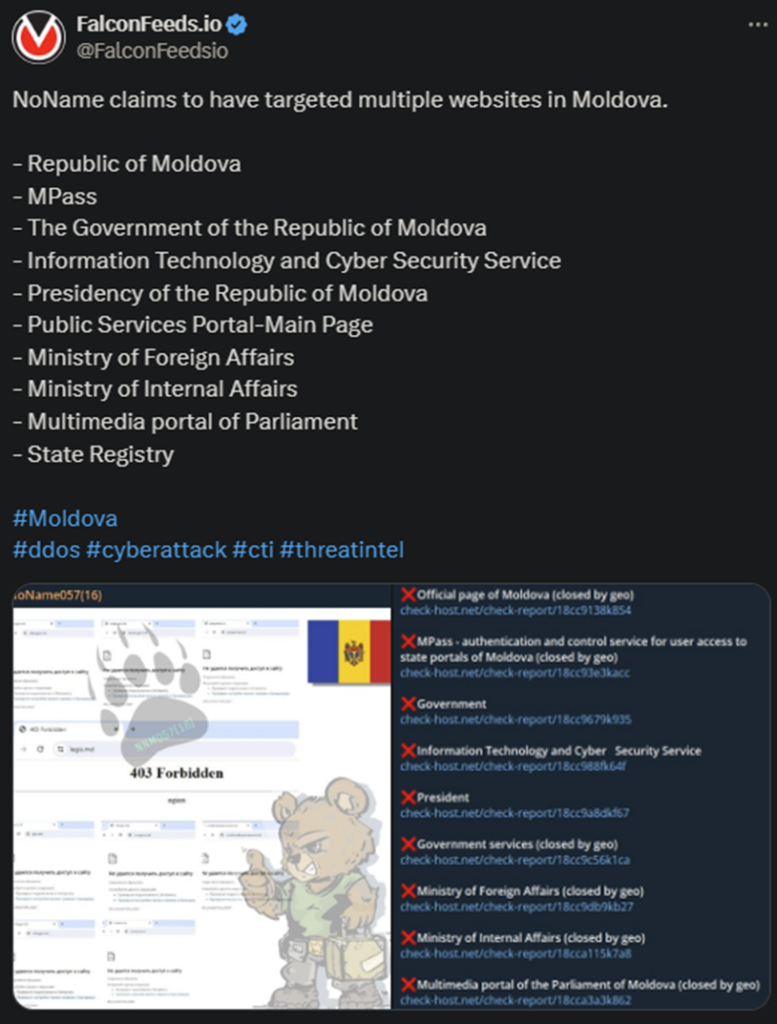
This massive attack comes just one day after another, just as devastating and intense. In that case, NoName also targeted Moldova’s public infrastructure.
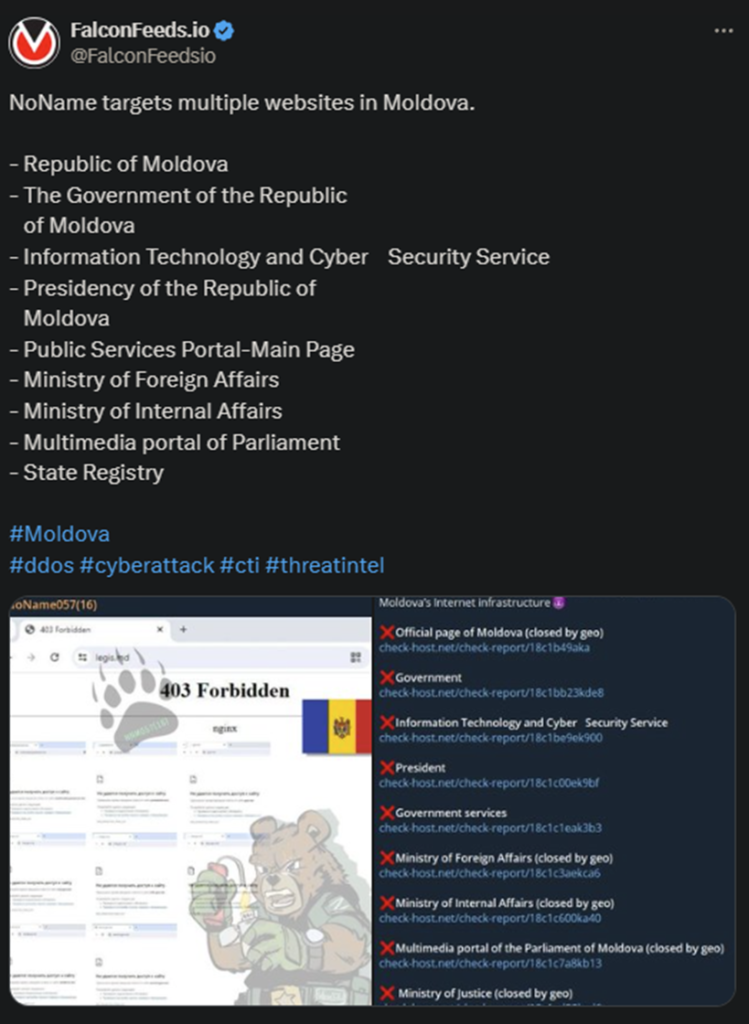
The gang’s typical MO consists of targeted DDoS attacks, causing armies of bots to overwhelm the target system. This usually causes the website to go offline, sometimes for days, depending on the severity of the attack.
While this is a fairly standard attack method, it can be quite devastating in some cases. Especially when the hackers target the public sector, which can have cascading effects the more the targeted services stay offline.
What Does NoName Want?
NoName first emerged publicly in March of 2022 and took off shortly after. The group was already extremely capable and advanced with state-of-the art tools and tactics. The gang pledged allegiance to the Russian government since day one.
The typical MO was using DDoS missiles to disable the victim’s online services. This is quite an effective tactic, as it requires low resources but can pack a powerful punch. But that’s not the only tactic they’re using.
The hackers are quite versatile and employ a variety of tools to intimidate and disable their victims. These include spreading propaganda and disinformation, stealing data, sending threatening letters, and blackmailing and extorting their victims.
In many cases, the hackers spread false information about their victims in an attempt to discredit their image and tarnish their reputation. The ultimate goal is to impact the victim’s ability to oppose the Russian regime. Or support the Ukrainian cause.
Understandably, NoName’s attacks have targeted primarily those nations invested actively in Ukraine’s success in the ongoing war. The hackers have prioritized those sending military and humanitarian aid or who’ve promised future aid packages.
These include Poland, the Czech Republic, Germany, Canada, France, the US, and Romania. It’s unclear how the Moldovan government will respond, but they have attempted to shield their institutions from NoName’s long arm of crime.
With little success so far.
Our Mission
We believe security online security matters and its our mission to make it a safer place.

