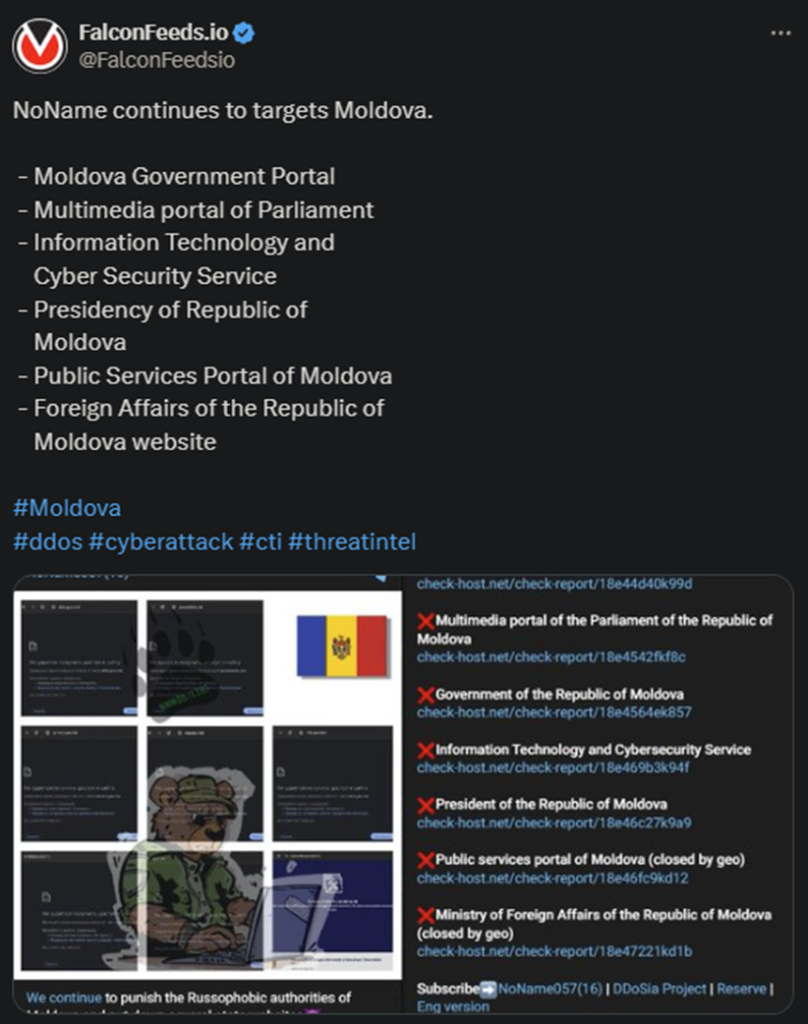
NoName Returns to Moldova
NoName hackers announced another massive operation on Moldovan soil. The hackers managed to produce multiple victims again, targeting high-profile institutions. These include Moldova Governmental Portal, the Multimedia Portal, and the Presidency website.
- NoName is a pro-Russian cybercriminal entity that’s deeply invested in protecting Moscow’s goals
- The NoName hackers have used a multitude of tactics to discredit Russia’s enemies, which there’s no shortage of in today’s climate
- This recent operation is part of a weeks-long crusade that saw NoName targeting multiple governmental institutions in Moldova
- The attacks are seemingly motivated by Moldova’s willingness to support Ukraine in the ongoing war
NoName justified its operation as a way to “punish the Russophobic authorities of Moldova.” This is a standard tactic for the gang, as NoName relies on multiple strategies to impact the reputation of its victims.
The cybercriminal climate has evolved dramatically over the past 2 years, since the beginning of the Ruso-Ukrainian war. NoName is currently the most vocal and active pro-Russian supporter. The gang came public in February of 2022.
Since the beginning of the war, NoName stated its intentions clearly: the protection of the Russian state and the destruction of its enemies. To that end, the hackers have employed a multitude of tactics. These include:
- DDoS attacks via their trademark DDOSIA tool (bot flooding)
- Spreading misinformation
- Pushing propaganda to gain fake political points
- Sending direct threats to mass-media representatives and governmental figures
- Mocking and threatening potential targets to intimidate them
- Working with affiliates and other cybercriminal gangs
- Stealing data
NoName targets governmental institutions primarily and they prioritize those that actively support the Ukrainian government. This refers to military and humanitarian aid, as well as preparing aid packages and funds for future assistance.
How Did Moldova Respond?
The news about NoName’s relentless DDoS operations have circulated in the local and international media. This is primarily due to their intensity and aggressive recurrence. As it stands so far, it doesn’t seem that Moldova has any radical plan moving forward.
As NoName has stated in one of their previous attacks, the local cybersecurity experts have already attempted to shield the target websites from the hackers. With no success, apparently, as the targets were breached anyway.
But how damaging are NoName’s attacks? Fortunately, not very damaging. As the hackers have admitted themselves, the goal is to send a message, not necessarily to inflict damages. Which is why they resort to standard DDoS bot attacks.
These overwhelm the target website with requests, mimicking more visitors and clicks that the server could handle. This often causes the website to crash and render the victim’s services unavailable. Which isn’t a big deal in most cases.
But it can be in others if the victim is a public service provider in charge of public systems. These include health, transportation, and emergency response. Overall, though, NoName’s attacks are little more than a temporary discomfort.
It doesn’t appear that the situation will change anytime soon either. NoName currently runs rampant, often targeting multiple targets across the globe simultaneously. The gang’s domination and resourcefulness have led to the theory of a state-funded org.
Nothing has been confirmed, but one can’t help to wonder.
Our Mission
We believe security online security matters and its our mission to make it a safer place.

