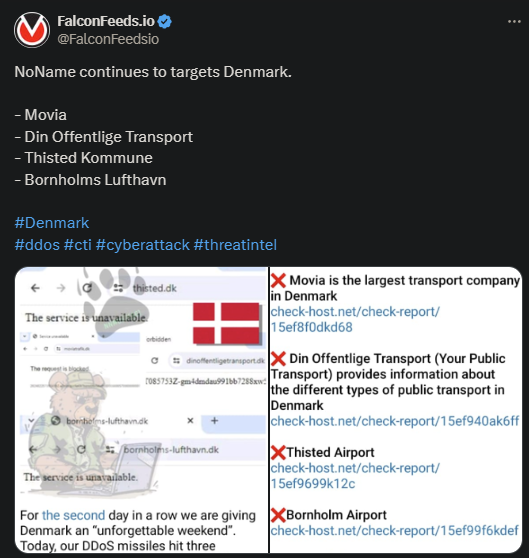
NoName Targets 4 New Victims
NoName announced the names of 4 new victims recently, all from Denmark. These are part of a growing list of Danish hits during NoName’s relentless Danish campaign. The cybercriminal ring aimed to make another political statement with these recent breaches.
- NoName is a self-proclaimed pro-Russian cybercriminal organization with a scary reputation
- The organization uses intimidation tactics and cyberattacks to make political and ideological statements
- The recent DDoS attack struck at 4 different targets on Danish soil: 2 airports and 2 transportation entities, one private and one public
- NoName’s self-stated goal is to punish Denmark for its continuous support of Ukraine in the ongoing conflict
According to recent statistics, Denmark provided Ukraine with over 565 million euros in military support during 2022. Furthermore, the Danish government devised a 5-year long plan for the 2023-2028 window, during which they plan to supply an additional 1.8 billion.
Needless to say, this didn’t sit well with NoName, which explains the recent string of attacks. As the group’s attack pattern showed, they primarily target states and private corporations that they deem to be enemies of the Russian state.
These recent attacks appear to have followed the same NoName pattern – mild but effective. The pro-Russian organization isn’t interested in inflicting too much damage, at least not regularly. Instead, they resort to fast and mild attacks meant to cause panic.
NoName is known for its strategic hits, only pouring resources where it matters. The organization is clearly capable of inflicting serious damage, as they have in some cases. But they prefer to use a more conservative approach in general.
How NoName Operates
NoName prefers to hit in bulk, multiple targets at once, even though the breaches may not cause significant financial or structural losses. The group has been operating this way since its inception in March of 2022, shortly after Russia’s invasion of Ukraine.
The cybercriminal ring stood out thanks to its aggressive tactics, impressive resourcefulness, and military-like discipline. Anonymous insiders and former affiliates gave us a glimpse into NoName’s machinery, and their discipline and tactics are impressive.
This military-like coordination and structure allows NoName to keep the cyberhacking machine operating at full capacity. The organization’s history tells a scary tale about its potential and attitude toward its perceived enemies:
- NoName sent threatening letters to Ukrainian media officials back in 2022 to intimidate and control the public narrative
- The group conducted relentless and massive cybernetic attacks against Ukraine’s infrastructure since the beginning of the war
- They have attacked most of Ukraine’s allies multiple times, with some of the most damaging ones being against the US
- They hit Finland shortly after the country joined NATO on the 4th of April, 2023
To be noted, NoName also tends to collaborate with other cybercriminal groups to conduct even more destructive and invasive attacks. Some of these groups are Killnet and XakNet, 2 other pro-Russian cybercriminal rings.
More importantly, NoName appears to be extremely resourceful and evasive, which explains why law enforcement agencies have been unable to crack it so far.
Our Mission
We believe security online security matters and its our mission to make it a safer place.

