NoName Targets Spain For 5th Day In A Row
Another day, another gruesome operation with NoName’s label on it. The (in)famous cybercriminal ring attacked Spain once more, this time producing six victims.
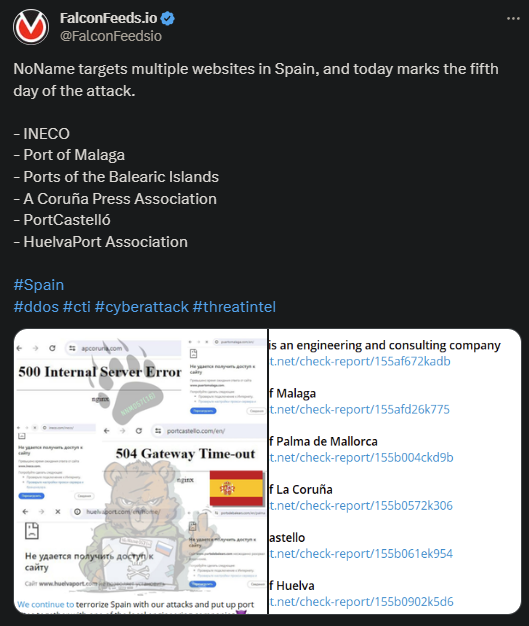
- NoName focused on the country’s ports this time, targeting Port of Malaga, Ports of Balearic Islands, and the Huelva Port Association, among others
- None of the victims have come fort with a public statement regarding the attacks
- According to the available data, all six restored their systems relatively soon after the event
- NoName marked this as the 5th day of coordinated attacks against Spain
As is typically the case with NoName operations, this too was politically motivated. NoName declared war against Spain and sees itself as pushing a crusade against the Spanish government. The cybercriminal ring has stated its support for the protesters.
Unlike many of its previous attacks, NoName doesn’t go for full damages this time. As they have declared themselves, the hackers plan to disrupt as many public and private organizations as possible. It doesn’t matter for how long or how damaging the attacks are.
This ongoing malware campaign aimed at Spain carries all the normal NoName marks. All of the attacks take place in bulk and they are usually very short-lived. They are not meant to produce a lot of damage, but to disrupt the victim’s normal operational flow.
The goal is to produce discomfort and keep the targets on their toes. It’s even better if the attacks force the victim to redirect funds towards their defenses, instead of using them elsewhere. Such as supporting Ukraine, among other things.
What You Need To Know About NoName
It’s no secret that NoName displays pro-Russian political sentiments, along with other high-profile cybercriminal rings. Killnet and Cyber Army of Russia are two of the most prominent ones.
NoName initially hit the public sphere in 2022, shortly after Russia invaded the sovereign state, Ukraine. The group immediately pledged allegiance to the Moscow regime and declared war to all of its enemies. Starting with Ukraine, of course.
The first attacks were aimed at Ukraine’s mass media, hoping to disrupt the flow of information and influence the narrative. NoName representatives have been very clear: they’re determined to eliminate Russia’s enemies by all means necessary.
The standard method of attack is almost identical in all cases. NoName never uses too many resources to conduct its operations. Rather, it relies on clean and targeted tactics to conduct small operations designed to cause discomfort and instill fear.
A more extensive investigation determined that NoName usually handpicks 5 to 15 viable targets and conduct reconnaissance jobs to find their most visible vulnerabilities. This level of preparation and logistics suggests an almost military-style level of discipline.
Once the targets have been highlighted, the group will conduct the attack and immediately take credit for it. The goal is to push their narrative as soon as possible and set an example for the world to see.
Many have suggested that NoName is actually funded by the Russian government, but no clear evidence have transpired in this sense.
Our Mission
We believe security online security matters and its our mission to make it a safer place.

