NoName Turns Its Gaze Toward Poland
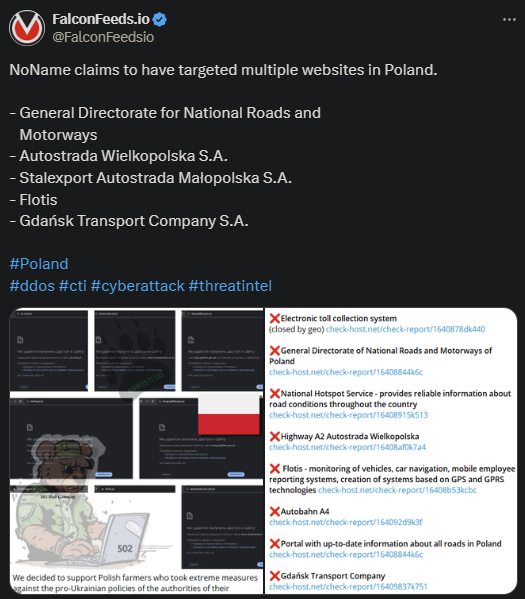
NoName announced its support for the anti-Ukrainian protests taking place in Poland recently. To make that clear, they attacked 5 Polish targets and published the evidence on their website.
- NoName stated that they support the Polish farmers who protest against the country’s pro-Ukrainian leanings
- This isn’t the first time NoName has hit Poland under this pretext
- Italy, Canada, Denmark, Switzerland, and Ukraine itself have also found themselves at the losing end of NoName’s wrath
- The pro-Russian cybercriminal organization has conducted over 1,500 DDoS attacks between March of 2022 and today
It’s unclear how damaging these recent DDoS attacks have been, but the victims’ websites went down as a result. Some have recovered in the meantime, but others have not. Autostrada A2 Wielkopolska was still down at the time of writing this article.
NoName has been on an absolute rampage lately, with prolonged DDoS campaigns against various states. The longest and most destructive one so far has been against Denmark. NoName conducted dozens of hacking operations against the Danish government.
Whether they will do the same with Poland remains to be seen.
NoName’s main drive is its loyalty to the Russian government. As the organization itself declares with each attack, its goal is to protect Russia’s interests and attack those who threaten them.
Unlike other DDoS organizations, the effects of NoName’s cybercriminal incursions aren’t limited to the websites. Instead, NoName aims to produce real-world effects and paralyze the target’s brick-and-stone operations as well.
This has been the case in numerous DDoS operations, including against several Canadian airports, leading to hours of delays at multiple border checkpoints. A similar thing happened during one attack on a Latvian train company.
As a result of the attack, the company could no longer produce and sell tickets until the situation was remedied.
How NoName Operates
NoName is very aggressive, but tactical and sophisticated at the same time. The organization has a multi-layered philosophy, using DDoS breaches, extortion, and threats as part of its intimidation tactic.
These strategies have become apparent ever since the beginning, along with NoName’s first operations against Ukraine. NoName emerged right after Russia invaded Ukraine, with many stating that the group appears to be state-funded.
A number of Ukrainian mass-media representatives have received threatening letters from NoName during that time. The group’s goal was to silence the opposition and influence the public narrative regarding Russia’s actions and goals.
Since then, the cybercriminal actor has been involved in over 1,500 DDoS attacks, all orchestrated by pro-Russian hackers.
In terms of actual MO, NoName seeks to minimize the costs and maximize the effects. So, they generally access free or low-cost web services to deploy their botnets and flood the targeted servers. These attacks are cost-effective, fast, and almost unpreventable.
That being said, there are ways to mitigate NoName’s tools and strategies. Working with cybersecurity professionals to boost your defenses is critical if you qualify as a potential victim.
NoName has been known to prioritize public institutions, but it often hits targets in the private sector as well if that aligns with its interests.
Our Mission
We believe security online security matters and its our mission to make it a safer place.

