NoName Uses Moldova as Target Pratice
The NoName hackers announced another massive DDoS operation, this time against Moldova. The reason behind the attacks is Moldova’s support for Ukraine, which was bound to attract NoName’s attention at some point.
- NoName is a pro-Russian gang with deep interests in the preservation and triumph of the Russian state
- The organization has conducted numerous operations against pretty much all of Ukraine’s allies over the past 2 years since its inception
- The hackers typically rely on DDoS botnet floods to take the victims’ websites offline
- Each post-statement attack usually explains the reason for NoName’s aggression
NoName is a fairly new cybercriminal group with deeply ingrained political and ideological ideals. The gang first came public shortly after Russia’s invasion of Ukraine at the beginning of 2022. Since then, they have carried out numerous attacks against just as many countries.
Ukraine was the first on the list, but others followed suit shortly. NoName’s goal is to push the Russian narrative and punish those who oppose the Kremlin regime. To that end, NoName employs a variety of strategies and tactics.
These include DDoS breaches, information leaks, spreading misinformation, political and ideological propaganda, and even direct threats.
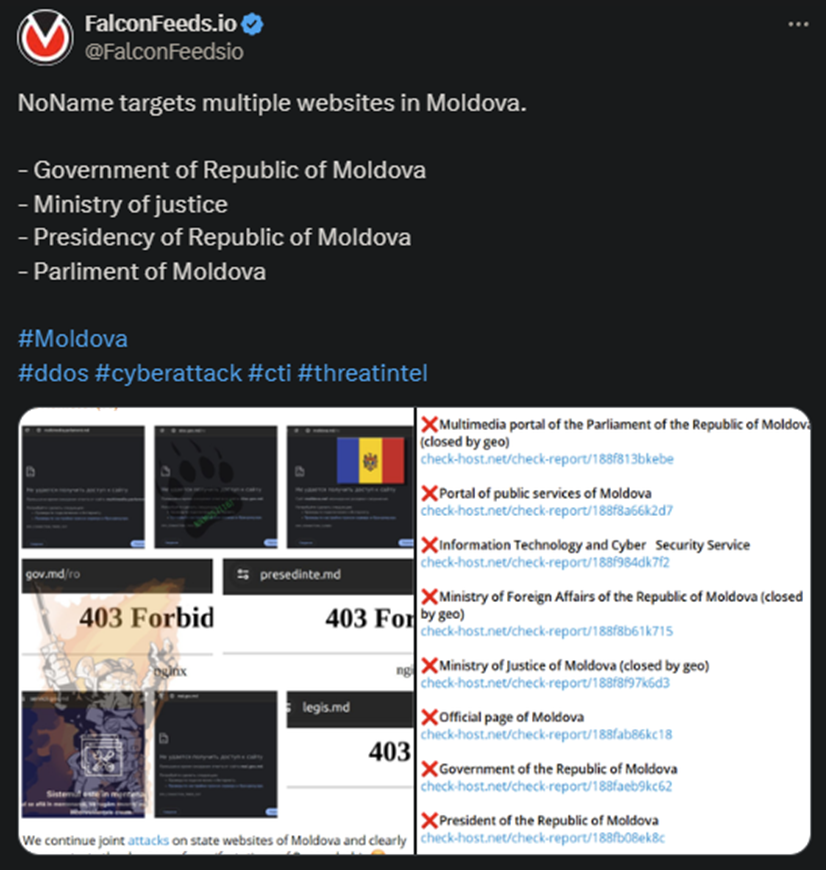
Today’s attack is the second in line, following another that also targeted several high-profile Moldavian institutions. That one was also politically driven, as the NoName hackers themselves have highlighted in the follow-up post.
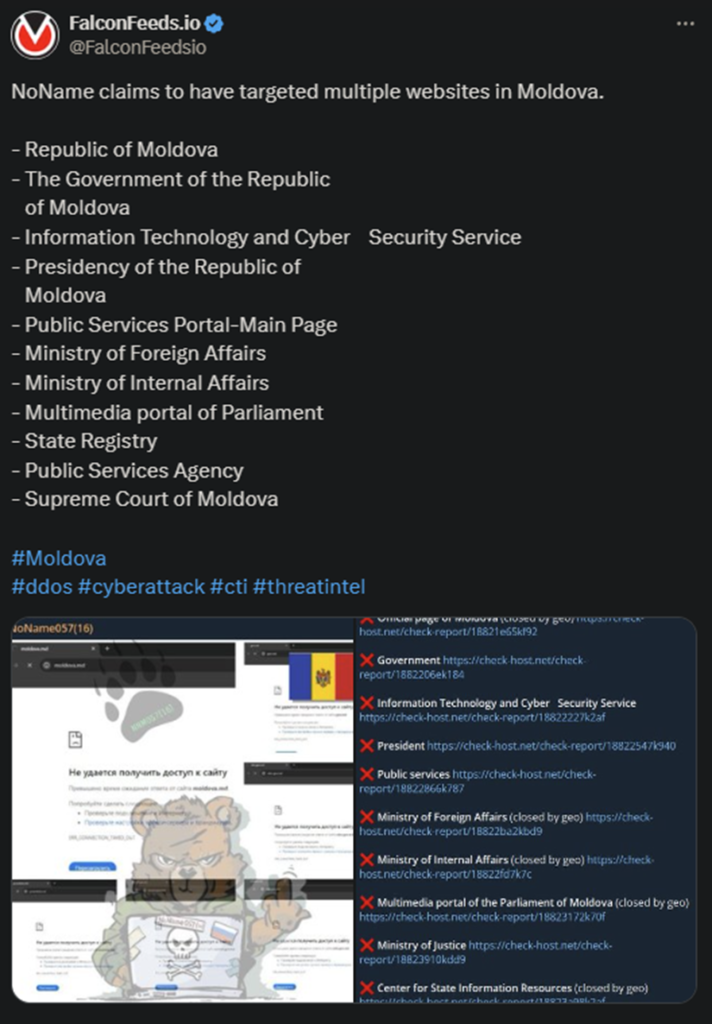
In both cases, NoName has accused the Moldavian government of being a Russophobe, which has become a standard tactic by now. While there are many politically-driven cybercriminal groups active today, NoName is the most infamous of all.
The gang currently ranks as the most active, resourceful, dangerous, and most determined organization today. The hackers operate at a global scale and they always pinpoint and infiltrate several targets per day.
How NoName Operates
Despite being relatively new in the cybercriminal sphere, NoName proved itself to be extremely resilient, versatile, and resourceful over the past 2 years. The group’s power and determination made some hint at ties between NoName and the Russian government itself.
This isn’t a far-fetched theory, as many governments use puppet cybercriminal identities to carry out cyberwarfare-related activities. This tactic is meant to preserve the concept of plausible deniability, allowing the perpetrators to hide their identities.
It’s not a new concept. But is this what NoName is doing? If it is, there isn’t any conclusive evidence in that sense. There are plenty of circumstantial ones, though. Such as NoName’s apparent power and funding, which are unusual for a newcomer.
More importantly, NoName doesn’t appear to be interested in profit-making. Their activity is strictly politically and ideologically driven. But the gang is getting good funding from somewhere.
Part of that is explained by the fact that NoName often uses affiliates to conduct more extensive operations. This allows the gang to operate globally with minimal financial investments and just as much exposure. But this tactic doesn’t explain everything.
Especially when considering that NoName conducts DDoS strikes every day, 24/7, and it always infiltrates multiple targets. So, if the gang is self-funded it’s still to be decided to what degree and where the funds are actually coming from.
Our Mission
We believe security online security matters and its our mission to make it a safer place.

