NoName’s Spanish Trip Enters its 5th Day
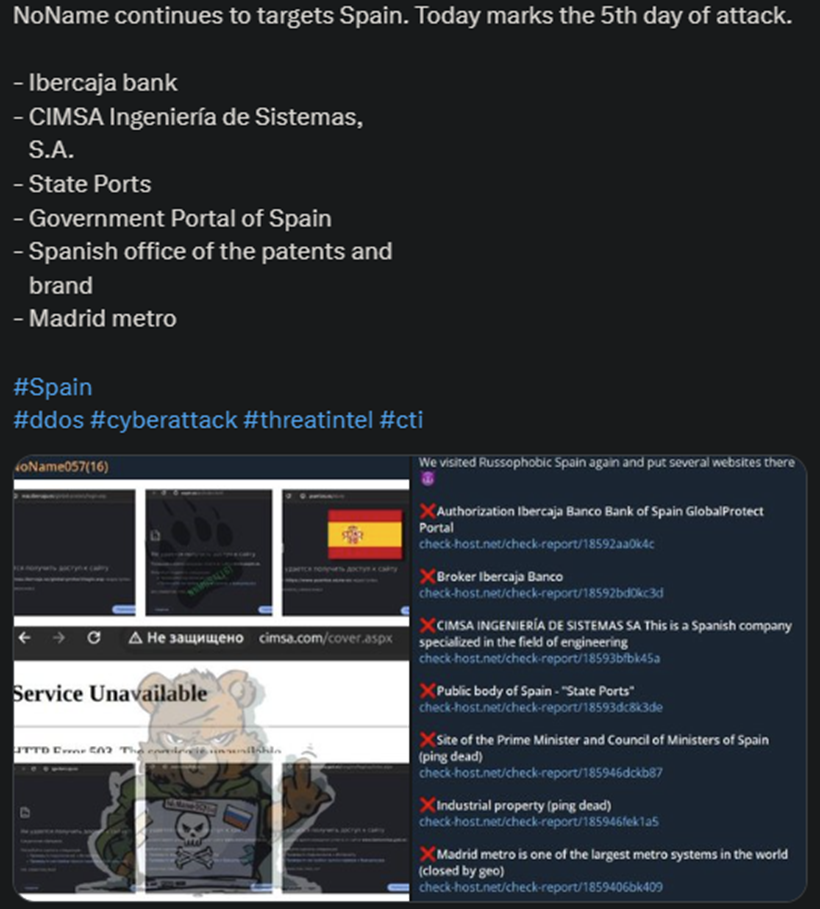
Spain finds itself under fire again after NoName targeted multiple websites today. The hackers listed 6 different victims, including the Madrid Metro, the Ibercaja Bank, and Spain’s Government Portal.
- NoName posted images with the targeted websites being taken offline as a result of the attack
- In the original post, the hackers mocked the Spanish government, calling it Russophobic and threatening with further action
- No Spanish official has commented on the attacks yet, despite this being the 5th consecutive day of NoName targeting the country
- Prior to Spain, NoName has hit multiple other governments, including Germany, France, the US, the Czech Republic, Poland, and Romania
At this time, NoName ranks as the most dangerous, active, and resourceful cybercriminal gang in the world. The hackers are openly pro-Russian and all of their operations are politically and ideologically motivated.
The group has been active since March 2022, coming public shortly after Russia’s invasion of Ukraine. Since then, the group has relied on a multitude of tactics and tools to spread its message and make an impact. Some of these include:
- DDoS attacks for disabling the target websites
- Spreading misinformation and propaganda
- Sending threatening letters and emails and mocking targets via public posts
- Leaking confidential data whenever possible
- Collaborate with other cybercriminal groups to infiltrate high-value targets, etc.
As the gang itself mentions at every opportunity it gets, the main drive behind the attacks is the attempt to silence and intimidate the victims. NoName is the most avid pro-Russian cybercriminal actor in the world, and all of its actions follow this mindset.
The hackers always target openly pro-Ukrainian entities, whether they are governmental institutions or private corporations. The most important common denominator in NoName’s attacks is whether the target has helped Ukraine or intends to in the near future.
Can NoName Be Brought Down?
There is obviously no clear answer, so long as we don’t yet have a grasp of NoName’s identity, structure, hierarchy, and code. The most glaring problem with holding NoName accountable is that the organization relies on affiliates to conduct many of its operations.
This takes the heat off of the main gang and instead spreads it across the affiliates themselves. Following those leads is always likely to end up in a dead end. Then there’s the problem of the funding and the group’s influence.
NoName appears to be very well funded and supported and relies on powerful connections in the cybercriminal world. The gang frequently builds partnerships with other malicious actors like XakNet and KillNet to conduct some of its operations.
The joint forces of the lawless entities make it very difficult for law enforcement agencies to crack any of them down. In fact, NoName appears to be so powerful, influential, and elusive that some have hinted at ties with the actual Russian government.
While this isn’t necessarily an outlandish theory, as Russia is known to rely on other cybercriminal actors when necessary, it is yet to be confirmed. What is confirmed is that NoName reputation and adaptability mean the group is most likely here to stay.
Our Mission
We believe security online security matters and its our mission to make it a safer place.

