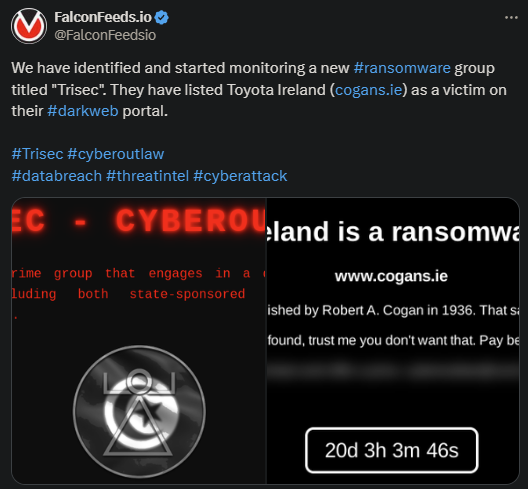
Novel Trisec Ransomware Hits Toyota Ireland
Newcomer Trisec ransomware announces massive operation. The victim is Toyota Ireland, the Cogans dealership.
- There isn’t much information about the attack, as the victim has refused to comment publicly on the event
- Trisec gave Toyota Ireland more than 20 days as a deadline for negotiations, which is highly atypical
- This suggests that the cybercriminal group is very confident in its systems and tactics
- Not much is known about Trisec, as this is a very new ransomware actor
As stated by Trisec themselves, this organization appears to be both privately and state-funded. They also appear to function as a mercenary group, both performing self-driven attacks and offering their services for sale.
Since the group is so new, investigation entities have yet to disclose anything meaningful about its operations, structure, members, or systems. However, initial observations point to the organization being very resourceful and dangerous.
It’s unclear at this moment the number of victims that Trisec produced before hitting the public stage or when the group actually took shape.
Should You Fear Trisec?
You most definitely should. If you’ve been keeping track of how the ransomware market operates, you know that there’s no such thing as a completely new ransomware actor. You will see a new name pop out occasionally, but that’s by no means a new group.
Instead, ransomware actors always reformat their structure and rebrand themselves the moment things get too hot. CISA and the FBI always crack down on cybercriminal organizations, especially the more active and aggressive ones.
Such was the case with Hive, Evil, Conti, and numerous others that now rank as defunct. But those who are keeping a close eye on the market know that ransomware groups never die out. They simply redistribute their manpower, resources, and systems.
This allows them to rebrand themselves as new entities with a different name and signature. The goal is to lose some of the heat and create confusion among law enforcement agencies, even if for a limited amount of time.
This may very well be the case with Trisec, although no clear data is available at this moment. But the actor’s impressive tactics, resources, and the ease with which it has penetrated such a high-value target do give that impression.
According to the latest FBI statistics, ransomware attacks are on a growing trend at the moment. It’s unclear what is driving this tendency, but small, medium, and high-end ransomware actors have increased their activity considerably over the past few months.
Experts advise taking extra precautions if you qualify as a noteworthy target for either ransomware or DDoS attacks. You may need to consult a cybersecurity expert to set up multiple defense layers.
More versatile ransomware actors tend to use multiple attack methods and exploit any system vulnerability they may find. And it’s not just about your infrastructure; the human component is also critical in this sense.
You need to educate your employees to recognize potential phishing attempts and learn when and how to repel them.
Our Mission
We believe security online security matters and its our mission to make it a safer place.

