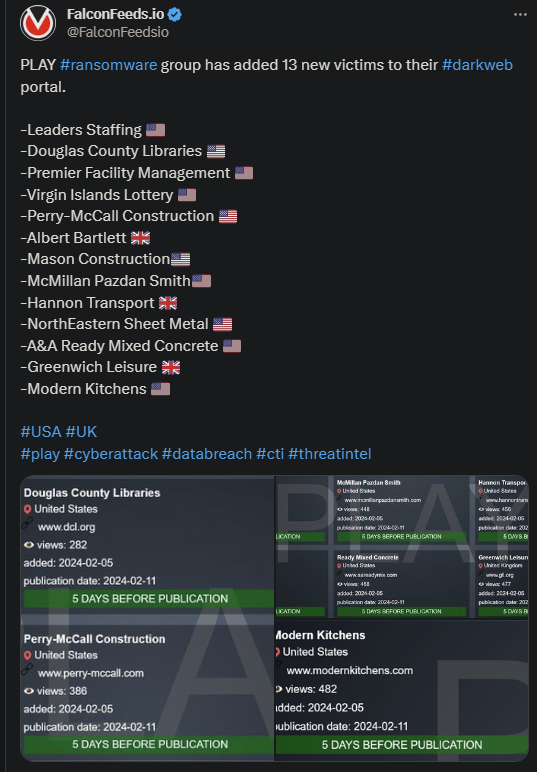
PLAY Ransomware Attacks Multiple in UK and USA
PLAY ransomware confirmed the staggering ransomware operation that took place earlier this week. The actor infiltrated 13 victims in an unprecedented attack operation spanning across 2 continents.
- Those affected are 3 UK-based corporations and 10 US-based ones from different industries
- Some of those targeted by the (in)famous ransomware actor operate in constructions, education, kitchen appliances, and transportation
- PLAY gave the victims time until 11th of February to contact them and discuss the ransom
- There is no information regarding how many victims have decided to negotiate with the cybercriminals, if any
While PLAY is a newcomer in the ransomware sphere, the actor has made a name for itself faster than anyone expected. The FBI reported approximately 300 victims over the span of little over a year, which is a staggering rate by any standards.
For reference, Lockbit, which currently ranks as the #1 ransomware organization, has amassed under 2,000 victims over the course of 5 years. PLAY seems to follow the same tactic of targeting victims in mass to increase the chance of successful payments.
PLAY sticks to the tried-and-tested double-extortion method, encrypting the victim’s files, paralyzing its operations, and stealing essential data from its systems. The attacker will then use the stolen data as leverage to demand a specific ransom.
The value of the ransom varies depending on the victim’s payment capabilities. It’s important to note that PLAY isn’t one to concede ground during negotiations. Their brutal and blunt negotiation tactics force many victims to cease communication.
That being said, some accept to pay the ransom despite the considerable financial loss, just so they can prevent the data from being publicly leaked. This is despite the experts warning that paying the ransom doesn’t guarantee that.
Where Did PLAY Come From?
PLAY first hit the public sphere in June of 2022 and, by October of 2023, the group managed to infect hundreds of public and private institutions. The method of attack varies slightly, but it always comes down to exploiting known vulnerabilities.
The group was deemed so active, aggressive, and adaptable, that the FBI and CSA (Cybersecurity Advisory) came online almost immediately. They investigated the organization over the span of more than a year and reached some interesting conclusions.
On the one hand, PLAY doesn’t leave any details in their ransom notes, aside from the basic information that the victim needs to contact them. The negotiations then take place in private. More importantly, PLAY guarantees utmost secrecy to victims.
They won’t disclose the result of the negotiations, how high the ransom was, or the amount that was agreed upon. Everything remains between the attacker and the victim, which is an interesting twist.
At this point, PLAY ranks as one of the most intimidating ransomware actors because of their attack and negotiation tactics and their impressive reach. The organization appears to be highly resourceful, capable of hitting multiple targets at once.
According to investigation sources, PLAY finally reached Australian soil, with its first victim being observed in April of 2023.
Our Mission
We believe security online security matters and its our mission to make it a safer place.

