PLAY Ransomware Attacks Televerde Next
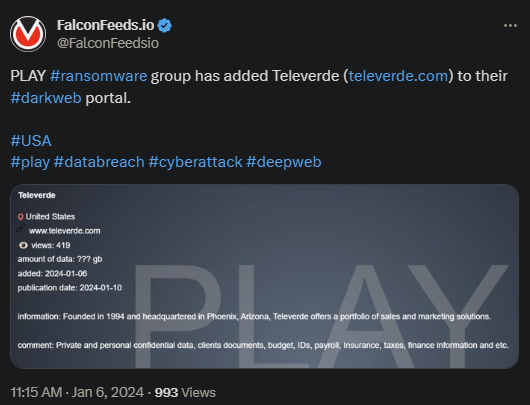
PLAY (also known as Playcrypt) attacked and breached Televerde recently, a marketing-centered US service provider. The attack resulted in a massive data leak.
- The attack on Televerde caused an important information leak, including confidential data about clients, internal documents, financial spreadsheets, payrolls, insurance details, etc.
- The company didn’t comment publicly about the attack, so not much is known about the aftermath
- PLAY has been active since June of 2022 and has primarily targeted US-based governmental agencies and private institutions
- Many of the attacks subsequently spread to Europe and even Australia more recently
The true identity of PLAY remains hidden, although both the FBI and CSA (Cybersecurity Advisory) went online quite fast. The organization showcases impressive internal secrecy, so the accumulation of data about its structure has been very difficult.
Unlike many other ransomware groups, PLAY never states its ransom demand in the initial letter. Instead, it provides contact info, leading the victim to their Tor network.
Ever since its inception in June of 2022, PLAY has been almost uncharacteristically aggressive, attacking a number of high-profile institutions. The group attacks pretty much indiscriminately, targeting both the public and the private sector.
Despite its high activity and predilection towards targeting high-profile victims, the law enforcement isn’t closer to breaking the organization. On the good side of things, it is reported that the FBI is cranking up its efforts considerably in this sense.
Who Is PLAY and How Does It Operate?
PLAY initially began operating in the US, but quickly spread its area of interest on other continents as well. The organization has been very active, with FBI reporting upwards of 300 victims by October of 2023.
The total profits in ransom money is unknown. The group itself appears to be withdrawn and not so vocal about its activity. It will post evidence of its latest attack(s), but not more than that.
This has led professionals to theorize that PLAY is strictly interested in financial gains. There haven’t been confirmed any type of political or ideological affiliations so far.
The group’s MO is multi-faceted, with PLAY employing several tools to infiltrate, exploit, clone, exfiltrate, and encrypt the victim’s data. The attack may also paralyze the system and the target’s operations, causing financial damages along the way.
At this moment, the best method of protection is to the standard system upgrade, as well as using multi-factor authentication, and keeping the software up to date.
Our Mission
We believe security online security matters and its our mission to make it a safer place.

