PLAY Ransomware Breaches 8 Targets Across the US and New Mexico
PLAY ransomware attacked and breached 8 targets within the US and Mexico. The companies being breached belong to different sectors like construction, food, and mortgage services. None have made any public comments about the incident.
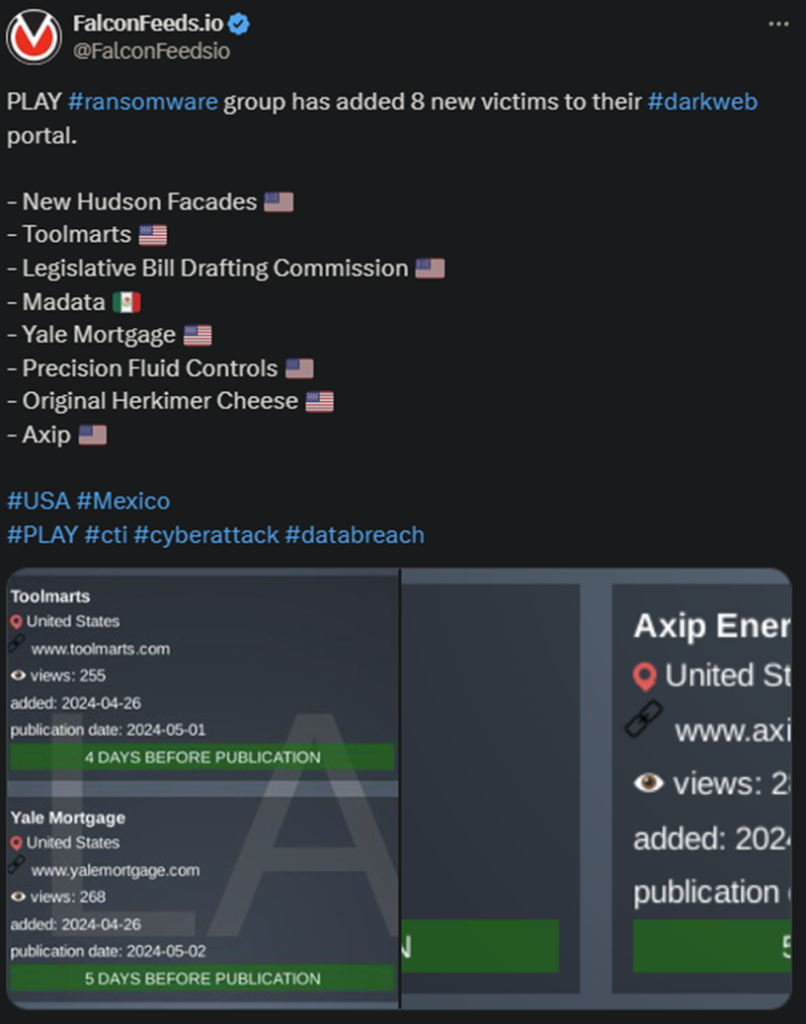
- The PLAY hackers have posted the evidence of the attacks on their leak TOR website
- According to the notes, the victims got 5 days to contact the hackers for negotiations
- It’s unclear if any have decided to follow suit or they simply chose to ignore the operators
- PLAY first went public in June of 2022 and stuck to Latin America (primarily Brazil) for their first year
This recent attack is rather atypical, as PLAY doesn’t usually breach multiple targets at once. The gang prefers to stick to 1-2 victims per operation to minimize their impact and fly under the radar. But everyone, in a while, decides to go big.
While the PLAY gang has been active since mid-2022, they haven’t hit the headlines as often as other ransomware gangs. That’s mainly because of the PLAY actors prioritizing stealth and efficiency. The hackers breach in, steal the data, and cover their tracks on the way out.
In many cases, the victims don’t even realize that they’ve been hit until they notice the ransomware note. Naturally, this changed once the cybercriminal gang adopted the multi-extortion tactic.
The double-extortion practice is easy to apply and effective. The hackers get into the victim’s system, steal the target data, and encrypt the files. This renders the victim’s system inaccessible, forcing the victim to contact the hackers if nothing else works.
The double-extortion practice also boosts the value of the ransom-to-be-paid. Most victims refuse to pay, but many still do. Not necessarily to get the decryption key but rather to prevent the stolen data from leaking on the Dark Web.
How to Protect Yourself from PLAY?
The PLAY gang prefers to prioritize small and medium-value targets. That’s because high-value targets usually come with a lot of heat and gangs like PLAY prefer to fly under the radar of law enforcement agencies.
So, what should you do if you get targeted by PLAY or any other ransomware gang? The bad news is that there is no clear-cut solution. Prevention is obviously the best go-to method, but if that fails, your options are limited.
The only advice you’ll get from cybersecurity experts is to adopt the no-negotiation policy. Never communicate with the hackers, never agree to compromises, and never pay the ransom. Nothing good will come out of it.
Those who pay do it to prevent the stolen data from leaking publicly, but records show that most ransomware actors will leak it anyway. Simply because the victim has no way of verifying it.
This will lead to even more security breaches in the future, due to other cybercriminal actors using the data for their own benefit. The best strategy is to ignore call-outs to negotiations and take the reputational hit, which will happen anyway.
Our Mission
We believe security online security matters and its our mission to make it a safer place.

