18 Biggest Ransomware Attacks in 2023
In this article, I’ll walk you through some of the biggest ransomware attacks in 2023. But before that, let me paint you a picture of just how serious ransomware is in 2023.
According to Statista, there were 154.93 million ransomware attacks worldwide in Q4 2022 and 493.32 million for the whole year, with the estimated cost of cybercrime in 2022 being a jaw-dropping $7.08 trillion.
Around 68.42% of all cyberattacks worldwide in 2022 were ransomware. That means one thing – around $4.84 trillion global financial losses attributed to cyberattacks in 2022 come from ransomware.
So, the average ransomware attack in 2022 netted around $9,811 in losses to its victim. Of course, a large portion of those ransomware attacks netted no profits because the victims would not pay.
Less than half of victims paid the ransoms in Q4 2022 (37% of all victims). That figure has since dropped to 34% in Q2 2023.
Alright, you get the picture.
Now, here’s a summary of the 18 biggest ransomware attacks in 2023:
| Affected | Ransom Requested / Paid |
| 1. Royal Mail | $80 million |
| 2. US Marshals Service | Not made public |
| 3. Minneapolis Public Schools | $1 million |
| 4. Lehigh Valley Health Network | $5 million |
| 5. Capita | Not made public |
| 6. Managed Care of North America (MCNA) Dental | $10 million |
| 7. City of Dallas | Not made public |
| 8. MOVEit | Not made public |
| 9. St. Margaret’s Health (SMH) | Not made public |
| 10. HWL Ebsworth | $4.6 million |
| 11. TSMC (Kinmax) | $70 million |
| 12. Barts Health NHS Trust | Not made public |
| 13. Tampa General Hospital | Not made public |
| 14. Prospect Medical Holdings | $1,298,340 million in Bitcoin (50 Bitcoins) |
| 15. CloudNordic & AzeroCloud | $157,000 in Bitcoin (6 Bitcoins) |
| 16. MGM Resorts & Caesars Entertainment | MGM Resorts has not paid, while Caesars Entertainment paid around $15 million |
| 16. KNP Logistics | Not made public |
| 16. Johnson Controls International | $51 million |
All of these ransomware attacks involved some measure of social engineering, which you can read more about in my guide.
Below, I’ll go into more detail about each attack and explain how it happened, whether it was successful, and the aftermath.
Let’s start!
Royal Mail

https://en.wikipedia.org/wiki/Royal_Mail
- When: January 2023
- What: LockBit group hacked into the UK’s postal services, encrypted all the files, and blocked all international shipments
- How: Ransomware attack carried out through unclear means
While it’s unclear how LockBit managed to breach the Royal Mail’s servers, the details of what happened afterward are crystal-clear.
In January, the Royal Mail announced that their international shipments were not working anymore. Immediately, negotiations began between LockBit and a Royal Mail negotiator.
LockBit kept making aggressive demands and, eventually, sent a ransom worth $80 million two weeks after the negotiations started.
The hacker insisted that this payment was a lot less than what the ICO (Information Commissioner’s Office) would fine them company if the data breach became public.
However, Royal Mail refused to pay the absurd sum of money, after which LockBit released the files on the Dark Web, claiming that the “Royal Mail need [sic] new negotiator”.
The nature of the files that went public is unclear and all we know is that they were crucial the Royal Mail’s international operations.
Six weeks after the ransomware attack, the Royal Mail announced that their international shipping services were restored.
US Marshals Service

https://en.wikipedia.org/wiki/United_States_Marshals_Service
- When: February 2023
- What: Ransomware attack that resulted in the theft of employees’ personally identifiable information, returns from legal processes, administrative information, and personally identifiable information about the subjects of USMS investigations as well as third parties
- How: Unclear how the hackers perpetrated the ransomware attack
In February 2023, the US Marshals Service announced that it had become the victim of a ransomware attack. The attackers, who are still unknown, had stolen sensitive data.
The incident was limited to a single computer system that contained records about the target of ongoing investigations, internal processes, and employee PII.
However, the hackers did not access any information about the individuals who are in the Federal Witness Protection Program.
The hackers never made any demand, which means that they had no financial motivations. Or perhaps the US Marshals Service never made the ransom public.
By May, the US Marshals Service had still not recovered fully from the attack, and they still hadn’t employed the new system which promised more security.
Minneapolis Public Schools

https://www.mplsschoolsvoices.news/posts/minneapolis-public-schools-has-significant-number-of-vacancies-two-weeks-before-school
- When: February 2023
- What: Ransomware attack that held hostage and then published over 300,000 confidential school documents that describe abusive parents, student sexual assaults, suicide attempts, psychiatric hospitalizations, and truancy
- How: Unclear how the hackers perpetrated the ransomware attack
On February 2023, several Minneapolis public schools reported a massive ransomware attack that ended in the theft of confidential student documents (more than 300,000).
These documents contained highly sensitive information about the private lives of students, including information on sexual assaults, abusive parents, suicide attempts, and more.
The hackers, identified as Medusa, demanded a $1 million ransom to unencrypt the files and give up on the attack. However, the public schools refused to pay this much money.
So, the hackers released all the documents publicly a month later on Facebook, Twitter, Telegram, as well as the Dark Web.
Among the exposed data, there were also discrimination complaints, social security numbers, medical records, and contact information of school employees.
The Minneapolis schools also failed in notifying the parents of the affected students even months after the attack.
Lehigh Valley Health Network

https://www.thevalleyledger.com/?p=117496
- When: February 2023
- What: ALPHV ransomware group leaked passports, medical questionnaires, nude images of breast cancer patients, Social Security Numbers, driver’s license numbers, lab results, and other medical information after the health network refused to pay the ransom
- How: The hackers managed to infiltrate the network by exploiting vulnerabilities in a physician practice in Lackawanna County
On February 6th, 2023, the Lehigh Valley Health Network detected unauthorized activities on its IT network. The BlackCat ransomware group had managed to infiltrate its systems by exploiting a vulnerability in one of its practices in Lackawanna County.
While we don’t know the exact value of the ransom demanded by BlackCat, we do know that LVHN refused to pay it.
As a result, the confidential information was exposed on the hackers’ data leak site, which included:
- Nude pictures of the patients
- Passports
- Medical questionnaires
- Social Security Numbers
- Lab results
- Medical treatment and diagnosis information
- Driver’s license numbers
A lawsuit was opened against the health operator after it allowed this confidential data to go public. Apparently, the health network had violated 9 HIPAA regulations and failed to implement the appropriate measures that would protect patient data.
Capita

https://www.securityandpolicing.co.uk/exhibitors/exhibitors-list-2023/capita/
- When: March 2023
- What: Customer, supplier, and colleague data could have been stolen by the Black Basta ransomware group
- How: Unclear how Black Basta managed to infiltrate the company’s systems but they likely exploited a vulnerability
In March 2023, Capita, the British outsourcing company, reported a data breach by ransomware group Black Basta. The associated costs will run up to $25 million, which are mainly composed of data recovery and remediation fees, as well as investments into their cybersecurity system.
While the size of the data breach is unclear (around 4% of the company’s server estate), Capita has stated that their customer, supplier, and colleague data may have been exposed and stolen by the attackers.
It’s possible that Capita has negotiated with the attackers or paid a ransom because at some point, their public listing has disappeared.
On the hackers’ leak site, they claimed that they had stolen passport scans, bank account details, physical addresses, and other sensitive information from Capita.
However, they’ve taken down the leak post after a while, which could mean that Capita has paid the ransom or reached another understanding with the hackers.
In its latest update posted on the 20th of April, Capita states that it has restored most of its client-end systems and that the data breach was averted successfully.
They did admit that, due to unauthorized access, the threat actors could access 4% of their server estate and that they stole colleague, customer, and supplier data.
Managed Care of North America (MCNA) Dental

www.prnewswire.com/news-releases/mcna-dental-announces-successful-reprocurement-of-texas-medicaid-contract-300977858.html
- When: March 2023
- What: Around 700GB (8.9 million patients) of sensitive patient data was at stake, with the LockBit group threatening to publish it unless the company paid $10 million in ransom. The data included PII, insurance claims, bills, health insurance information, and teeth and brace documentation
- How: LockBit exploited unclear vulnerabilities to infiltrate the MCNA Dental systems
On the 6th of March, 2023, the company reported unauthorized activity on its internal network. Later on, they revealed that the threat actors accessed sensitive information dated February 26th – March 7th, and copied it.
The data included:
- Patient names
- Addresses
- Dates of birth
- Phone numbers
- Email addresses
- Driver’s license numbers
- ID numbers
- Social security numbers
- Health plan information
- Medicaid-Medicare ID numbers
- Insurance company information
- Information on insurance claims
- Information on treatment and bills
All in all, over 8.9 million people were affected in the data breach. The LockBit ransomware group took responsibility for the attack and published the data dump on their leak site after MCNA Dental refused to pay the $10 million ransom demand.
It’s safe to say that LockBit put the data up for sale on the dark web, and now the personal and health data of over 8.9 million people is out there, bought by the highest bidder.
City of Dallas

https://spectrumlocalnews.com/tx/dallas-fort-worth/news/2022/08/11/city-of-dallas-logo-marks-50th-anniversary
- When: May 2023
- What: Ransomware attack that left several of the city’s critical systems malfunctioning and confidential data of over 26,000 people was affected by the Royal hacker group
- How: Unclear attack specifics
In early May, the city of Dallas became the target of a ransomware attack by the Royal threat group.
The data of over 26,000 people was affected during the attack, according to the city’s officials during a report in August.
Some of the data included names, addresses, medical data, and other personal information accessed from the government servers.
During the attack, many of the city’s critical systems were not operational, including:
- The Dallas Police Department
- The 311 Customer Service
- The Dallas City Courts
- The Dallas Water Utilities
- The Code Compliance Services
- The Dallas Animal Services
- The City’s Secretary Office and Development Services
The hackers also left a ransom note behind where they discussed the ransom required to not publish the confidential data online.
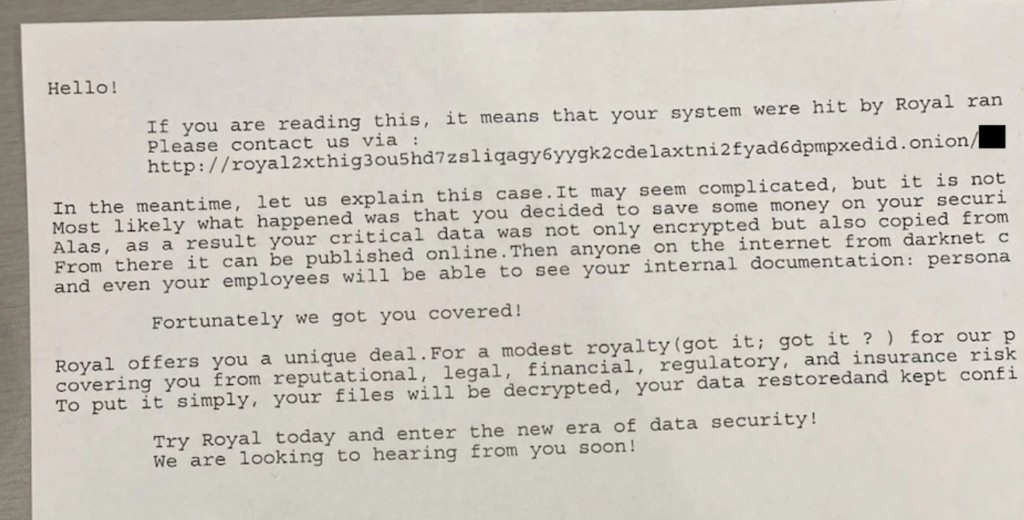
https://securityintelligence.com/news/lessons-learned-from-the-dallas-ransomware-attack/
Early on, the City of Dallas posted an Informational Notice about the data breach, where they claimed that they could not comment on the origin of the attack but that the attack method was ransomware.
The city eventually quarantined all city-related devices and contained the virus with the help of third-party security vendors for which the city paid around $8.6 million.
MOVEit

https://www.malwarebytes.com/blog/news/2023/07/moveit-transfer-fixes-three-new-vulnerabilities
- When: May 2023
- What: Data stolen from over 2,600 public, government, and business organizations all over the world through MOVEit’s systems, affecting more than 77 million people
- How: Zero-day vulnerability used to access MOVEit’s systems with the purpose of data theft
In May, the enterprise file transfer tool MOVEit reported that it became the victim of a particularly troublesome ransomware attack from the Clop hacker group.
The hackers used a zero-day vulnerability dubbed CVE-2023-34362 to gain access to thousands of clients of MOVEit. Even though a patch soon came out, not everyone was aware of it or installed it.
Clop provided a deadline (June 14th) for all the affected companies to contact them, and on that day, they named 13 of the affected companies were named, with many more in the following days.
They threatened to publicize the stolen data by June 21st if the victims refused negotiations but they changed their mind and recently stated that they’d deleted all the data stolen because they had “no interest to expose such information”.
At the time of writing this article, it is estimated that the MOVEit data breach affected over 2,600 organizations and more than 77 million people.
St. Margaret’s Health (SMH)
https://aboutsmh.org/diagnostic-services/
- When: February 2023
- What: Crippling ransomware attack that led to the shutdown of the IT network, electronic medical systems, email systems, and other web operations. Eventually, the hospital closed after 120 years of service (partially because of unexpected COVID-19 expenses and other factors)
- How: Unclear how the ransomware got inside the hospital’s systems
In February 2023, St. Margaret’s Health announced a ransomware attack that crippled its email systems, IT network, electronic medical records portal, and other web operations.
The hospital could not collect payments from insurers for any services it rendered, effectively crippling it entirely.
According to the VP of Quality and Community Services Linda Burt, the attack lasted over four months, forcing employees to resort to pen and paper for day-to-day operations.
Some of the operations took almost a year to become fully operational after the hospital slowly recovered from the cyberattack.
As of June 16th, 2023, both St. Margaret’s Health and Spring Valley hospitals in Peru will be closing their doors, in part due to the ransomware attack in 2021.
To our knowledge, these are the first organizations forced to close operations who attribute one of the reasons to a cyberattack.
HWL Ebsworth

https://www.lawyersweekly.com.au/companies/22682-hwl-ebsworth
- When: June 2023
- What: 4TB of data stolen, out of which 1.4TB was made public. It included financial information, local and remote company credentials, and customer documentation
- How: BlackCat ransomware group accessed HWL’s servers through unclear means, though it’s clear that the attack type was ransomware
In June 2023, the law firm HWL Ebsworth was attacked by the BlackCat ransomware group. They accessed the company’s servers in Melbourne, Australia, and stole 4TB of data from them.
The data included customer documentation, internal company data, insurance agreements, identification details, credit card information, loans data, and local and remote company credentials.
The hackers demanded a AUD5 million ransom but HWL Ebsworth refused to pay it. As a result, some of the stolen data was exposed online (around 1.4TB of it).
At least 60 departs of government agencies were caught in the middle after the law firm was hacked. Their data was in the data dump stolen by BlackCat.
Around 2.5 million documents were stolen during the attack, and about 1 million were published on the dark web, waiting to be sold.
TSMC (Kinmax)

https://en.wikipedia.org/wiki/TSMC
- When: June 2023
- What: Stolen data of a TSMC IT supplier related to the configuration guidance for customers and the system installation
- How: Unclear how LockBit got into Kinmax’s systems
According to the news, Taiwan Semiconductor Manufacturing Company (TSMC) became the victim of a ransomware attack on June 20th, 2023.
The intruders had managed to infiltrate their systems and exfiltrate data related to the configuration guidance for customers and the system installation.
LockBit took responsibility for the data breach and demanded $70 million in ransom payment to not go public with the data.
“In the case of payment refusal, also will be published points of entry into the network and passwords and logins company”, the hackers said on their data leak site.
There’s a catch, though. TSMC claimed that it was not them who were hacked but one of their IT hardware suppliers, Kinmax. And the latter actually confirmed this later on.
TSMC terminated its work relationship with Kinmax immediately after news of the attack went public. They’ve reported that their systems have not been affected following the attack on Kinmax, and that their security systems are intact.
Barts Health NHS Trust

https://en.wikipedia.org/wiki/Barts_Health_NHS_Trust
- When: June 2023
- What: 70TB of sensitive healthcare data stolen, including employe identification documents, internal emails, passports, driver licenses, and other data
- How: Unclear how the BlackCat ransomware group got their hands on the Barts Health data
In June 2023, the ALPHV/BlackCat ransomware group claimed on their data leak site that they’d obtained 70TB of confidential data belonging to the Barts Health NHS Trust.
The healthcare conglomerate has under its supervision over 2.5 million people, so the data breach was pretty sizeable.
The hacker group claimed that NHS would have three days to begin the negotiations before the data would be published.
As of July, the data still hasn’t been published and we don’t have further information about this.
Barts Health could have paid the ransom since we haven’t heard about any data dump and BlackCat hasn’t made other public statements about the data breach.
What’s more, this is the second data breach that involves NHS data. During the first one, the UK’s University of Manchester was attacked and the hackers managed to access an NHS dataset containing information about 1.1 million patients.
Tampa General Hospital

https://business.tampabaylgbtchamber.org/member-directory/Details/tampa-general-hospital-2015640
- When: July 2023
- What: Theft of personal health information of 1.2 million patients
- How: A ransomware attack failed against the Tampa General Hospital but the hackers still managed to steal health data of over a million patients
In July 2023, the Tampa General Hospital became the target of a ransomware attack that resulted in a lawsuit being opened against it.
The hackers stole medical data of over 1.2 million patients and the hospital didn’t notify the victims until months after the attack.
According to official sources, the hospital noticed the data breach on May 31st and then started an internal investigation to see what’s wrong. They then reported this even to the FBI for assistance with the investigation.
Among the stolen data, there were:
- Names
- Addresses
- Dates of birth
- Phone numbers
- Social security numbers
- Medical record numbers
- Account numbers
- Health insurance information
- Dates of service
The sensitive nature of the information makes the data breach even more serious, with the plaintiffs arguing that “this lawsuit will not only secure justice and accountability for the patients whose privacy and peace of mind have been irrevocably violated, but also will spur Tampa General Hospital to take additional steps to protect their patients’ privacy in a manner appropriate for the current climate of cyber-attacks.”
The hospital did manage to prevent a full-fledged attack and mitigate a large portion of the damage.
Prospect Medical Holdings

https://www.bankinfosecurity.com/hospital-attacks-a-22741
- When: August 2023
- What: Theft of 500,000 social security numbers, patient records, and corporate documents
- How: Unclear how the attackers managed to breach Prospect Medical’s security systems
On August 2023, Prospect Medical Holdings employees saw a ransom note on their computers once they got to work.
The hackers, later identified as Rhysidia, explained that they’d stolen 500,000 Social Security numbers, patient records, and corporate documents. No information about a ransom is available at this point.
We also don’t know if Prospect Medical Holdings has paid the ransom but if the hackers had publicized the information, it’d have been all over the news.
It is also estimated that over 24,000 employees of Prospect Medical Holdings may have become the victims of the cyberattack.
Given Prospect Medical’s extensive network of partners, many other hospitals like the Southern California Hospital and the Eastern Connecticut Health Network have reported problems with their operations because of this cyberattack.
Even months after the attack, Prospect Medical Holdings is still facing financial issues but thankfully, all of its affiliates have restored their services completely.
CloudNordic & AzeroCloud

- When: August 2023
- What: Massive loss of customer data
- How: Some of the servers used by both companies had already been infected by malware before being moved to another data center and connected to the companies’ internal network
On August 2023, the Danish cloud companies CloudNordic and AzeroCloud became the victims of a dual ransomware attack.
Based on official statements, there was a massive loss of customer data that led the CEO of both companies to state that he wouldn’t expect them to have any customers left in the aftermath of this attack.
The hackers, unidentified as of yet, have demanded six Bitcoins in ransom (around $157,000) to restore the stolen data. However, the companies decided not to pay the criminals’ ransom.
They’ve released a public statement saying that they couldn’t pay it nor do they have any intentions to try and meet the hackers’ demands.
Both companies were hit hard, with all their servers being wiped of all customer data, and it’s still unknown whether or not they’ll recover.
MGM Resorts & Caesars Entertainment
- When: August-September 2023
- What: Downtime costs, financial losses ($100 million for MGM Resorts), 6TB of data lost (Caesars)
- How: It is believed that voice-phishing was used to trick the IT support or the call center workers at these companies to bypass the multifactor authentication
Around the middle of August, the casino entertainment company Caesars Entertainment was attacked by a social-engineering attack.
Initially, this attack involved the theft of personal data from the members of its customer rewards program.
One of the company’s IT support vendors was used in a supply-chain attack to gain access to Caesars Entertainment’s systems, and the data breach occurred on the 28th of August but they only discovered it on the 7th of September.
While Caesars did not offer any official numbers of affected customers, the filing with the Maine attorney general’s office indicates 41,397 Maine residents who were affected.
The stolen data included social security numbers and divers license numbers, with no evidence of any banking or financial data being part of the data dump.
Eventually, Caesars paid $15 million to the Scattered Spider ransomware group to avoid the public exposure of its customers’ data by the hackers.
In the same period, the MGM Resorts casino company reported a data breach later attributed to the same hacker group responsible for the attack on Caesars.
It’s unclear whether MGM Resorts paid the ransom but they officially stated that the data breach would lead to a $100 million financial hit. This is likely because of the lower room occupancy, and the impact on the company’s entertainment and gaming operations.
The two data breaches were among the biggest ones this year!
KNP Logistics

https://www.facebook.com/KNPLogisticsGroup/
- When: June 2023
- What: Key systems and processes affected, which crippled the company’s financial situation, eventually leading to insolvency
- How: Unclear how the hacker group infiltrated KNP Logistics’ systems
In June 2023, one of the largest logistics companies in the UK, KNP Logistics Group, was hit by a ransomware that crippled their operations.
The attack affected their key systems and processes, exposing financial information, and leading the company on the brink of financial disaster.
Their reputation suffered significantly because of the cyberattack, which ultimately affected their ability to secure funding and investments.
In September, the company had to declare insolvency after laying off 730 employees, though it’s not all because of the data breach. Even before that event, the company was in a perilous financial situation.
The hacker group who attacked KNP Logistics is Akira, known for being associated with the Conti ransomware group. They use similar tactics, like string obfuscation, file encryption, and double extortion strategies to trick their victims into paying the ransom.
It’s safe to say that the company did not pay any ransom to Akira but despite this, the reputation damage was too much for the company to endure.
Johnson Controls International

https://en.wikipedia.org/wiki/Johnson_Controls
- When: September 2023
- What: Encrypted company devices, performance impact on company operations, theft of 27TB of corporate data, ransom of $51 million
- How: Supply-chain attack that first breached the company’s Asia offices and the infiltrated other offices through the internal network
In September 2023, the multinational conglomerate Johnson Controls was attacked by the Dark Angels ransomware group.
They managed to compromise their network, leaking critical data, encrypting essential files, and deleting the company’s backups.
In the ransom note, the group demanded $51 million to provide the decryption and delete all the stolen data. It’s estimated that Dark Angel stole 27TB of corporate data from Johnson Controls.
They also encrypted their VMware ESXi servers, which were integral to the company’s operations.
Johnson Controls did not pay the ransom as far as we know, so there’s no telling what the hackers will do with the stolen data. It’s estimated that the data dump also contains sensitive Department of Homeland Security data.
Conclusion
2023 was a particularly troublesome year for ransomware attacks. Countless companies around the world have suffered at the hands of RaaS groups.
Two of the companies on this list have either had to disband or file for insolvency partly because of the ransomware attacks targeting them.
It’s beyond clear that the current cybersecurity standards are no longer enough. Between social engineering and zero-day vulnerabilities, hackers are having a field day in today’s cyber-ecosystem, and it’s the companies that suffer the most.
Sources
Statista – Number of Ransomware Attacks Worldwide from 1st Quarter 2020 to 4th Quarter 2022
Statista – Estimated cost of cybercrime worldwide 2017-2028
Statista – Distribution of Detected Cyberattacks Worldwide in 2022, by Type
Privacy Affairs – The Art of Cyber Deception: Social Engineering in Cybersecurity
The Guardian – ‘All We Have Had Is Losses’: Royal Mail Dismisses ‘Absurd’ $80m Ransom Demand
Edition CNN – US Marshals Service Still Recovering from February Ransomware Attack Affecting System Used by Fugitive Hunters
Cybernews – Medusa Claims Minneapolis Public Schools as Victim
Bitdefender – BlackCat Hackers Denied Ransom in Attack on Leigh Valley Health Network
Capita – Update on Cyber Incident
Bitdefender – Capita Says Hackers May Have Snagged Customer and Employee Data in Recent Cyberattack
Sangfor – Ransomware Attack in Healthcare: MCNA Dental Data Breach Affects 8.9M Patients
Ken Paxton Attorney General of Texas – Data Security Breach Reports
GovTech – Dallas Approves $8.6M in Ransomware Response Payments
NVD NIST – CVE-2023-34362 Detail
Emsisoft – Unpacking the MOVEit Breach: Statistics and Analysis
Healthcare Finance News – A Cyberattack Is Partly to Blame for St. Margaret’s Health Closing All Operations
The Guardian – HWL Ebsworth Hack: 65 Australian Government Agencies Affected by Cyber-Attack
Bitdefender – TSMC Refuses to Pay $70 Million Ransom After Lockbit Falsely Claims Its Affiliates Hacker the Giant Chipmaker
The Register – Barts NHS Hack Leaves Folks on Tenterhooks Over Extortion
Health News Florida – Class-Action Lawsuit Filed Against Tampa General Hospital Over Recent Data Breach
CT Mirror – Prospect Medical Cyberattack Exposes 24,000 Workers’ Private Info
Tech Monitor – Devastating Ransomware Attack Hits Danish Cloud Hosting Companies CloudNordic and AzeroCloud
Maine Government – Data Breach Notifications 1
Maine Government – Data Breach Notifications 2
The Record – UK Logistics Firm Blames Ransomware Attack for Insolvency, 630 Redundancies
Information Week – Cyberattack Disrupts Operations at Johnson Controls International

