Ultimate Guide To SOC 2 – All You Need to Know
Cybersecurity is one of the prime interests of all organizations, including third-party service organizations or vendors.
As a service provider, having standard security controls is vital for establishing trust and confidence with your clients.
SOC 2 provides an essential framework that you can use to prove that you take information security as one of your top priorities by demonstrating you have implemented necessary security policies.
Also, if you are outsourcing critical business operations to SOC 2 compliant third parties, your data within them is guaranteed to be secured.
SOC which stands for System and Organization Controls (SOC), has been developed by the American Institute of Certified Public Accountants (AICPA). They provide a suite of control reports as:
- SOC 1
- SOC 2
- SOC 3
- SOC for cybersecurity
- SOC for supply Chain
SOC 2 is what focuses on internal controls related to cybersecurity of the services provided by service organizations within the following five Trust Service Categories or Trust Services Criteria (TSC).
- Security
- Reliability
- Confidentiality
- Privacy
- Processing Integrity
- Availability
A SOC 2 report provides information regarding the effectiveness of controls within these criteria and how they integrate with controls at the user entity.
SOC 2 report is an outcome of the SOC 2 audit which is carried out by an independent, licensed CPA under Statement on Standard for Attestation Engagements (SSAE) No18: Attestation Standard.
It introduces SOC 2, a framework developed by the American Institute of Certified Public Accountants (AICPA) to oversee internal controls in cybersecurity, based on five Trust Service Principles: Security, Availability, Processing Integrity, Confidentiality, and Privacy.
The article further delves into the two types of SOC 2 reports: Type I, which evaluates the design of internal controls at a specific point in time, and Type II, which assesses both the design and operational effectiveness of these controls over a period.
Entities such as data centers, cloud storage services, and healthcare organizations frequently need to comply with SOC 2 standards, with audits performed by a licensed CPA.
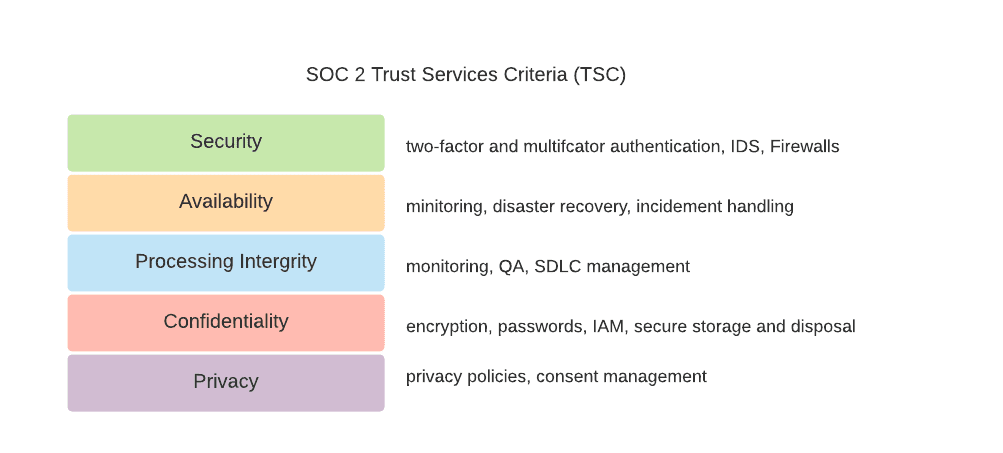
SOC 2 Trust Services Criteria (TSC) and Related Controls
To become SOC 2 compliant, your organization needs to satisfy the TSCs defined by AICPA.
Depending on what kind of client information you have and how they are processed, you need to choose what criteria to include in the SOC 2 report. Let’s learn more about the focus points related to each of these criteria.
Security
Organizations that satisfy this criterion can protect information and systems from unauthorized access, disclosure, and system damages that affect their availability, integrity, confidentiality, and privacy.
Security focuses on the protection of:
- Information during its collection, creation, processing, transmission, usage, and storage.
- Systems that use electronic data to store, process, and transfer information.
Controls over security criteria help detect and rectify system failures, unauthorized removal of information or system resources, software misuse, incorrect data processing, and improper use of, alteration, destruction, or disclosure of information.
Availability
Availability focuses on the accessibility of information used by your organization’s systems and the products or services you provide to your customers.
If your organization meets this criterion, your information and systems are always available for operation and can meet its objectives anytime. It addresses if the systems include controls to support accessibility for operation, monitoring, and maintenance.
However, it doesn’t address the functionality and usability of the system.
Processing Integrity
The Processing Integrity principle is the criteria to check if the system achieves its intended purpose and functions properly without errors, delays, omissions, and unauthorized or accidental manipulations.
It focuses on the completeness, validity, accuracy, timeliness, and authorization of system processing. If you are doing data processing or transactions on behalf of your customers, you need to include this criterion as part of your audit.
Confidentiality
Your company may be storing data classified as confidential information, which is restricted, disclosed, and allowed to be used only for certain people. For example:
- Business plans
- Internal business reports
- Intellectual property
- Financial Information
- Legal documents
Besides, there can be laws, regulations, and Non-Disclosure Agreements (NDA) with your clients to keep these data confidential. The confidentiality policy addresses your company’s ability to protect such information throughout its life cycle from collection and creation to removal from your control.
This sensitive information can be in the form of physical documents or digital documents. Therefore, controls need to be applied considering their nature.
Privacy
All sensitive and Personally Identifiable Information (PII) data such as social security number, name, address, sexuality, and race need to be protected from unauthorized access to meet this criterion.
Their collection, use, disclosure, and disposal need to be done according to Generally Accepted Privacy Principles (GAPP) of AICPA and the organization.
Privacy controls only apply to personal information. At the same time, confidentiality applies to various types of sensitive information.
Examples of TSC Related Controls
| Trust Services Criteria (TSC) | Controls |
| Security |
|
| Availability |
|
| Processing Integrity |
|
| Confidentiality |
|
| Privacy |
|
Who Needs the SOC 2 Certification?
If your organization falls under the following categories, you may require this compliance at any time.
- Data Centers
- Managed IT service providers (MSP)
- Cloud storage and cloud computing providers
- Software-as-a-Service (SaaS) companies
- Medical and Insurance claims processing companies
- Banking and Financial Services
- Accounting and Auditing firms
- Customer Relationship Management (CRM) services
- Retail Services
- Data Analytics companies
- Human Resources
- Document Processing services
- Health care organizations
Since the report contains information about the internal security control of a company, it will not be accessible to everyone. It can be used by persons linked with the service organization under a Non-Disclosure Agreement. Examples of users of a SOC 2 report include:
- Service organization management
- Business partners
- Customers of the system
- Prospective customers evaluating potential vendors
- Regulatory bodies
What are the Types of SOC 2 Reports?
Usually, the service organization management prepares a description of its system using AICPA SOC 2 description criteria.
Also, they include the design and suitability of internal controls related to one more of the TSCs they chose to be relevant and their effectiveness in operation.
After that, service organization management hires the certified CPA to examine and provide a SOC 2 report on their view of management’s claims. There are two types of SOC 2 reports.
SOC 2 Type I Report
In this report, the auditor examines and evaluates the following at a specific time.
- The design of internal controls of the service organization
- Suitability and the effectiveness of the control design and implementation
This report does not evaluate the operating effectiveness of the controls. It is rather the auditor’s opinion about the service organization management’s description of the system and the suitability of the design of controls.
This report is generally the first step of getting SOC 2 compliance for a company. Typically, it can take 2-4 weeks to generate this report.
SOC 2 Type II Report
This report provides a more comprehensive look at the design of the service organization’s controls specified in the Type 1 report. Type II report includes both Types I criteria and the operating effectiveness of the service organization controls.
Usually, it can take six months to up to one year to examine, prepare and provide this report.
What is Included in a SOC 2 Report
Overall, a SOC 2 report will include the following statements:
1. From the service organization’s management
- A description of the service organization’s system, including the service types, system components, boundaries, and controls.
- An assertion whether the description in 1 is prepared according to the SOC 2 description criteria.
- An assertion whether controls described in 1 are designed and operating effectively.
2. From the auditor
- Opinion about the service organization’s managements’ description
- Opinions about the controls that have been described in the management’s assertion evaluated within the TSCs.
- A detailed description of the tests of controls and results
Generally, a SOC 2 report is valid for twelve months since the report was issued. The cost of a SOC 2 depends on several factors such as:
- The scope and the TSCs selected
- Size of the company
- The costs of any training
- The complexity of the systems and controls
- Number of sites to visit
Which SOC 2 Report is Suitable for Your Organization?
Whether you are a service provider or a receiver, SOC 2 Type II report is what provides the best assurance that your organization complies with the TSCs. However, SOC 2 Type I report itself is useful in some scenarios.
Type I report is suitable when a SOC 2 report is required immediately by a customer or any business partner. If you are getting this assertion for the first time or your organization is a startup, it is suitable to get a SOC 2 Type I report first before proceeding with the Type I report.
SOC 2 Type I is also suitable for smaller companies with minimum sensitive data and do not require strict security policies. In addition, sometimes, you may just compare potential service organizations for your next business venture. Then SOC I report will be ideal for you to request from the potential vendors.
Who Can Perform a SOC 2 Audit?
A SOC 2 audit can only be performed by an independent and licensed Certified Public Accountant (CPA).
Specifically, the CPA must have received the required training and possess the technical expertise and knowledge in information security. The SOC 2 auditor should always be updated with the changes for the TSCs done by AICPA and comply with the standard rules.
Since AICPA regulates this audit, non-CPAs cannot perform or partner with CPAs to perform the audit.
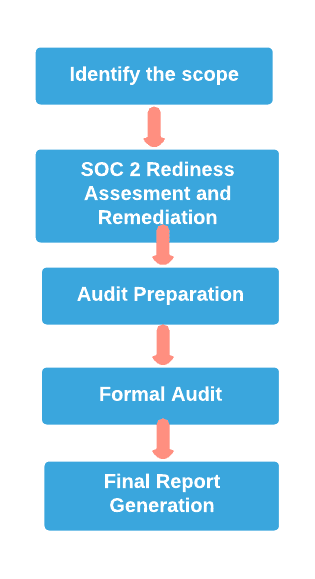
What Steps Should You Follow for the SOC 2 Certification Process?
Identify the scope
The first step in getting SOC 2 certified is establishing the scope and priorities for the evaluation. It is a form of a planning phase, a very critical step most companies tend to overlook. In this phase, you need to:
1. Identify auditors – Identify and contact the certified and experienced auditors who have built a reputation for proper SOC 2 audits.
2. Define the system description – Write a description of your system to the auditor. For example, describe its components, boundaries, and controls if the company provides a payroll processing service to clients. The length of the description may vary depending on the complexity of your system. This description will later be included in the SOC 2 report.
3. Identify Trust Service Criteria you should include in the report.
Typically, this phase can last several weeks depending on the facts such as your organization’s preparedness, available information, experience with the process, etc.
Readiness Assessment and Remediation
Before taking the actual audit, organizations may want to identify the gaps and risks associated with the existing internal controls using a SOC 2 readiness assessment.
This phase is optional if you have a thorough understanding of the system controls in place and are confident about the success of the examination. Several SOC 2 consultancy services can assist you with those who are ideally experts in this field.
This assessment will provide a detailed description of what controls would meet the auditors’ expectations, what controls are not enough to be SOC 2 compliant, and a set of guidance to remediate the identified gaps.
If you have this understanding before the formal audit, you can immediately take the required corrective steps rather than waiting till the final report.
Prepare for the audit
After the scoping and the readiness assessment phases, you can start preparing your formal audit. Usually, in this phase, the auditor explains the examination process in detail and requests a list of documents, also called Information Request List (IRL), and evidence for the formal audit.
You must prepare and ready whatever documentation they may ask you for during the phase. You are also allowed to take assistance from audit assisting companies to collect these documents. You can get their necessary support during the formal audit because they know what exactly the auditors need.
Formal audit
After completing all the preparations, you can begin the formal SOC 2 audit. The auditor will collect all the evidence and conduct the necessary tests to identify whether the internal controls comply with the chosen SOC 2 TSCs. Usually, the auditor visits the organization for this process. Sometimes, they will work remotely or use a combination of both working methods.
During this process, you may have to answer any questions about the controls in place. Sometimes, the auditor may be required to interview certain employees of the organization.
In addition, they may request additional documentation to support as evidence which will require a significant amount of time to prepare. Therefore, you must ensure you are well-prepared for the formal audit to save additional costs and time.
Final Report Generation
Once the auditor has collected all the evidence and completed the required tests, they will begin drafting the report. After the draft is complete, you will get the opportunity to review the draft and provide suggestions and comments.
The auditor will incorporate the required changes to the draft based on your feedback and finalize the report. Finally, you will receive this final report as a soft copy, but some auditors may also provide a hard copy.
Top Policies to Establish for SOC 2 Compliance
Use the following 12 policies as a checklist to see how well you are prepared for the audit. Again some of these policies may not apply to your organization based on what type of client data you have and what kind of processing you do with them.
| Policy | Contents |
| Information Security (IS) Policy | Controls to protect data from unauthorized access and disclosure from unauthorized users. |
| Access Control Policy | Restrict access to high-security systems for authorized users by defining role-based access control policies. |
| Password Policy | Enforce the users to create strong and secure passwords according to the defined format, set expiration times and send reminders via emails and securely store the password in an encrypted format. |
| Change Management Policy | Define how changes to the system should be requested, reviewed, approved, or deferred that minimizes the impacts to data and systems. |
| Risk Assessment and Mitigation Policy | Specify risk identification and management approaches, periodic risk assessment strategies, mitigation plan, and roles and responsibilities of different parties in risk management. |
| Logging and Monitoring Policy | Define the approaches for logging user activities and monitoring them. |
| Data Classification Policy | Identify and establish classification definitions for sensitive, protected, and public data and default data classification |
| Incident Response Policy | Roles and responsibilities of members of the incident response team in the event of a security incident or data breach and authorized tasks |
| Information, Software and System Backup Policy | How frequent the data and system backups should be taken, how long they are retained and storage of backups | Acceptable Use Policy | Appropriate and inappropriate activities when using internal resources and rights and responsibilities when using them. | Business Continuity and Disaster Recovery Plan (BCDR) | A plan to continue business operations when the business is affected by a disaster to minimize the outages and impact to the users. | Vendor Management Policy | Define the responsible parties for vendor management, due diligence, and contract management. |
How Can Organizations Accelerate the SOC 2 Certification Process?
1. Delegate tasks
As part of the SOC 2 certification audit, you may need to gather many documents. Consider this teamwork and delegate this workload to responsible parties as much as possible.
For example, assign the company’s incident response team to provide incident response plans and evidence for the mandatory training. You can also consider getting the help of an external service that can do these tasks on behalf of these teams.
2. Store all the required documents in a centralized repository
This will be helpful when accessing the documents by anyone involved in the audit. Also, make sure to make backup and hard copies in case of damages. Use an easy naming convention to organize them to identify and pick up the required document easily.
3. Educate your employees
Give a heads up about the audit to all the organization members so that everyone will be aware of the process. When everyone is informed, It can make auditors and your tasks easier during the process.
4. Consider automating the process
You can use audit workflow and preparation software which provides pre-built policies to map with SOC 2 compliance policies and many other functionalities to automate the compliance process.
What Benefits Will Your Organization Get With SOC 2 Certification?
Investing in this certification can provide you with the following key benefits.
For service organizations
- Opportunity to get your security in order – During the certification process, you get the opportunity to identify your existing security posture and remediate potential issues and security gaps that will otherwise be hidden and unnoticed.
- Competitive Advantage – Having a SOC 2 certification proves your trustworthiness to clients and interested parties. It will improve your reputation over competitors who do not own this attestation.
- Increase Revenue – Consumers are often interested in choosing organizations with SOC 2 certification. This means demand for your services could rise, which will be a stepping point to achieving higher revenue.
- Cost Saving – Consider an instance where a data breach occurs due to a security loophole in your system. The cost of such a data breach and the damage to your organization’s reputation could be millions of dollars, far outweigh the SOC 2 certification cost. Passing SOC 2 attestation can save you from such unnecessary costs.
For customers
- Sense of Assurance – This is a report assessed by an independent auditor who provides an independent opinion about the organization’s security posture. Due to this nature, customers may feel a sense of assurance that their data is secured by third parties.
- Receive visibility and transparency about the service provider’s internal control gaps – customers can identify potential areas of risk and find methods to mitigate them within their scope.
- Ease of choosing potential vendors – use this as evaluation criteria to select the most trusted service when two or more vendor companies have the same capabilities.
Summary
Achieving SOC 2 compliance helps your organization stand out from the crowd. This guide explains in detail everything you need to know about this standard framework, from its definition to the certification process.
You can follow the checklists and tips described in this guide to better prepare for the audit and save time and costs. Because the more you prepare, the fewer problems you face and meet the expected success from the examination.