Your 2024 Ultimate Guide to Tor Browser
In this guide, we will discuss the Tor browser, how it works, how to use it, and how to ensure your safety and security.
Tor Browser is software that lets you surf the internet and use all web services anonymously. Nobody — not even government organizations, law enforcers, or big corporations — would be able to check your browsing history or track your location, provided you follow certain security practices.
Below we will discuss the following topics:
- What TOR is and how it works
- How to install Tor on any device and OS
- Tips to ensure your security while using Tor
- The legality of Tor
Use the navigational menu on the right (desktop) or down below the image (mobile) to quickly jump to sections that are to your interest.
It uses onion routing, a technique that directs web traffic through a global network to hide the user’s location and other details.
In this article, I’ll guide you through installing and using the Tor browser on various devices and operating systems. I’ll also offer tips on maintaining security while using Tor and discuss the legal aspects of using the browser.
Although Tor provides significant anonymity, it doesn’t guarantee complete security. Therefore, I recommend using a VPN alongside Tor for enhanced protection.
Tor Browser — The Basics
Who Uses Tor, and Why?
There are several main categories of Tor Browser users:
- Users who want to surf the web privately, without internet service providers (ISPs), advertisers, and businesses mining their data. This group makes up the majority of users.
- Users trying to avoid being spied on and censored. These are issues often faced by journalists and human rights activists working in regions of the world with repressive regimes.
- Military personnel. Certain U.S. military organizations, including the US navy, use Tor.
Of course, criminals infiltrating the dark web — to exchange information, sell services, or run illegal marketplaces — could theoretically form another user category.
So while Tor is legal for the most part — except in China, where it’s forbidden, and in Venezuela, Iran, Saudi Arabia, Russia, Turkey, and Egypt, where it’s restricted — it can be used to perpetrate illegal activity. (We trust you’re no criminal, so this shouldn’t matter!)
How Does Tor Browser Work?
Short for “The Onion Router,” Tor is based on a technique called onion routing.
This allows Tor to direct internet traffic through a massive global overlay network, thereby hiding its users’ location and other information about their activity — on the dark or surface web.
Thanks to the onion routing technique, it’s considerably more difficult for a third party to trace individual user activity.
Now let’s get into some more granular detail. Encryption is used at every level of the application layer in Tor Browser’s communication protocol stack (just like the layers of an onion).
Tor applies encryption to different user data multiple times while sending it through a circuit of successive, randomly selected Tor relays.
Each relay decrypts a layer of encryption to reveal the next relay in the circuit to pass the remaining encrypted data onto it.
Then the final relay decrypts the innermost layer of encryption, sending the original data to its destination while keeping the IP address of the source hidden.
Since any network surveillance relies heavily on the information about the source and destination of data, this technique makes it much harder to trace any network activity to the source.
How Secure Is Tor Browser?
In terms of privacy, Tor offers the best level of anonymity. This doesn’t necessarily mean that Tor Browser is perfect, but it does provide another layer of security for your day-to-day browsing.
In terms of safety, Tor is perfect for normal web browsing. However, it’s not 100% secure, especially if you use it to access illicit marketplaces or message boards on the dark web.
To help you minimize risk, we’ll get into a few recommendations later. But one basic tip we’ll share now is that it’d be a great idea to use a VPN while browsing with Tor Browser.
Check out our guide on choosing the best VPNs for recommendations.
How Much Does Tor Browser Cost?
Nothing. Tor Browser is managed by The Tor Project organization as an open-source project, so it’s free. (If you’re feeling generous, you can make a donation, though.)
Getting Started with Tor Browser
How to Install Tor Browser
It’s easy! First, go to Tor Project’s website, and click on the “Download Tor Browser” button at the top right corner.
Then, on the Download page, select from any of the major operating systems available (Windows, Linux, Mac, Android). Here’s a detailed, step-by-step guide for each one:
Windows
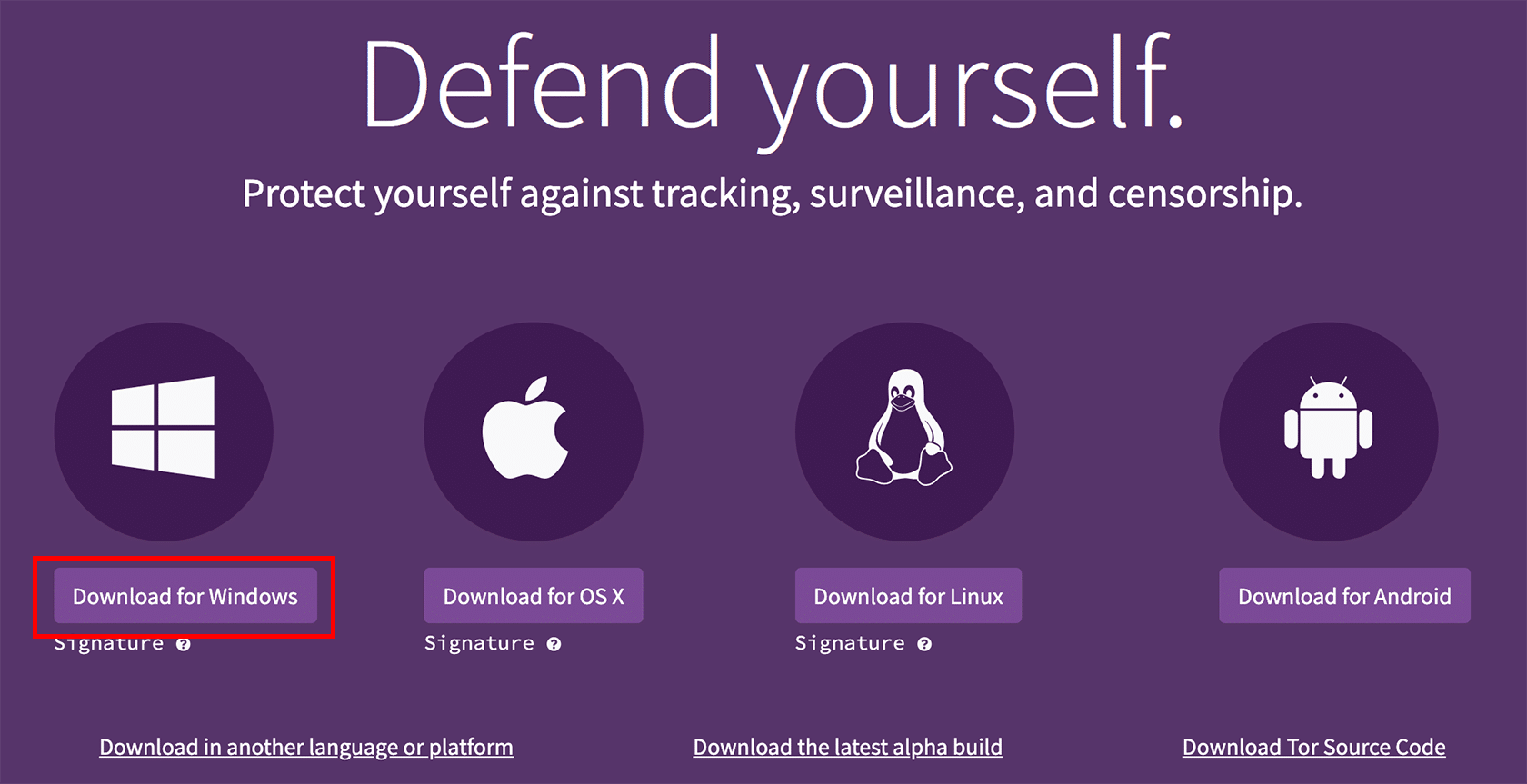
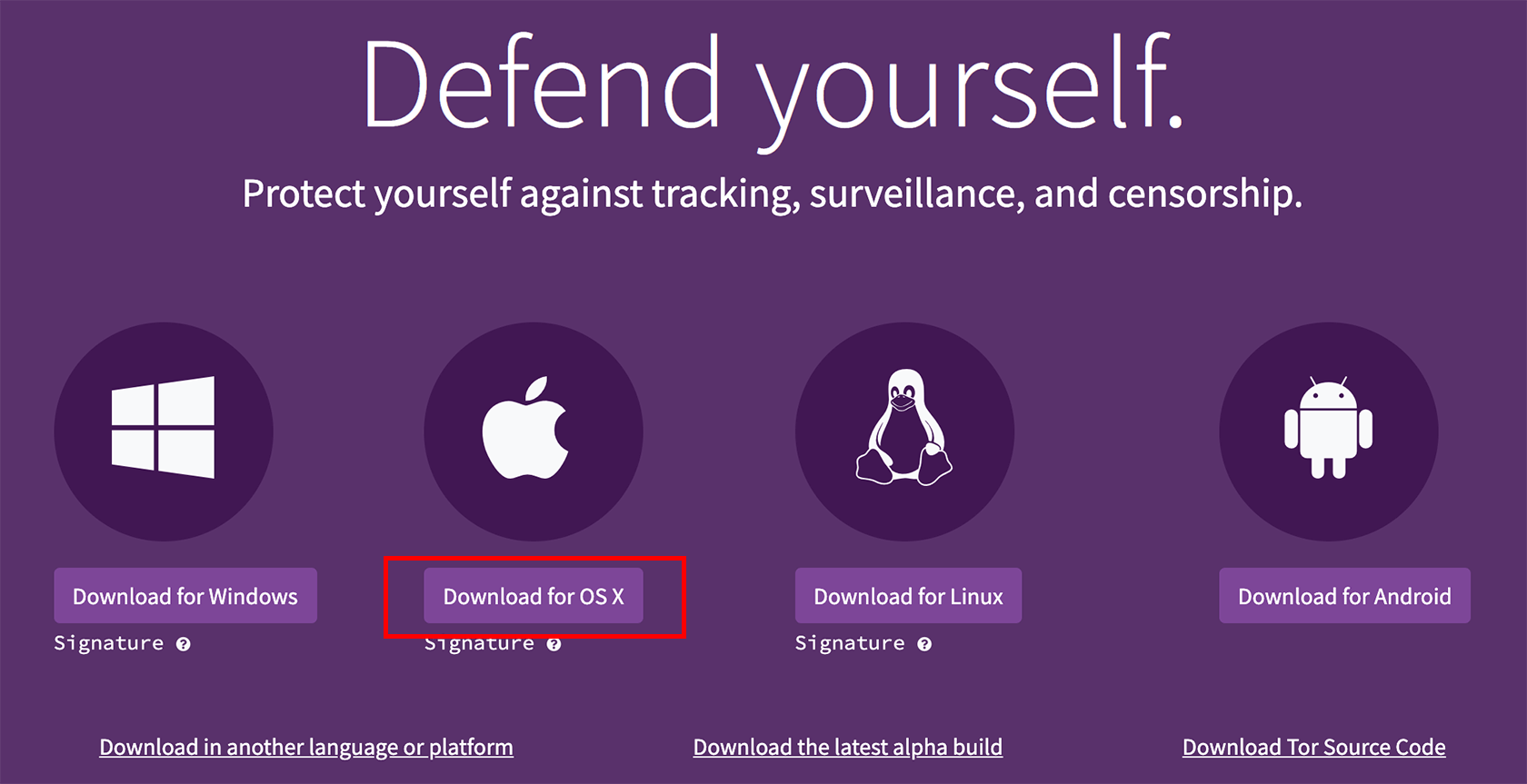
Click the “Download for Windows” button.
Launch the .exe file after it’s downloaded by double-clicking it.
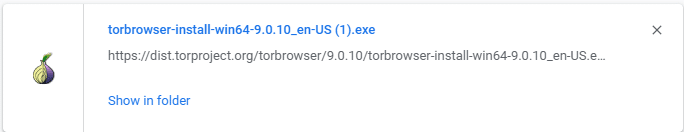
Choose your language and click OK.
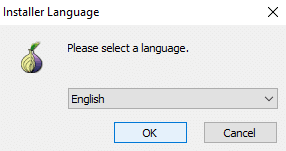
Follow the installation prompts.
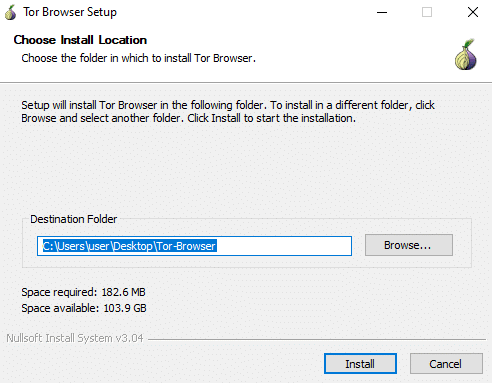
Click Finish when the installation is complete. And you’re done!
Linux
Click on the “Download for Linux” button.
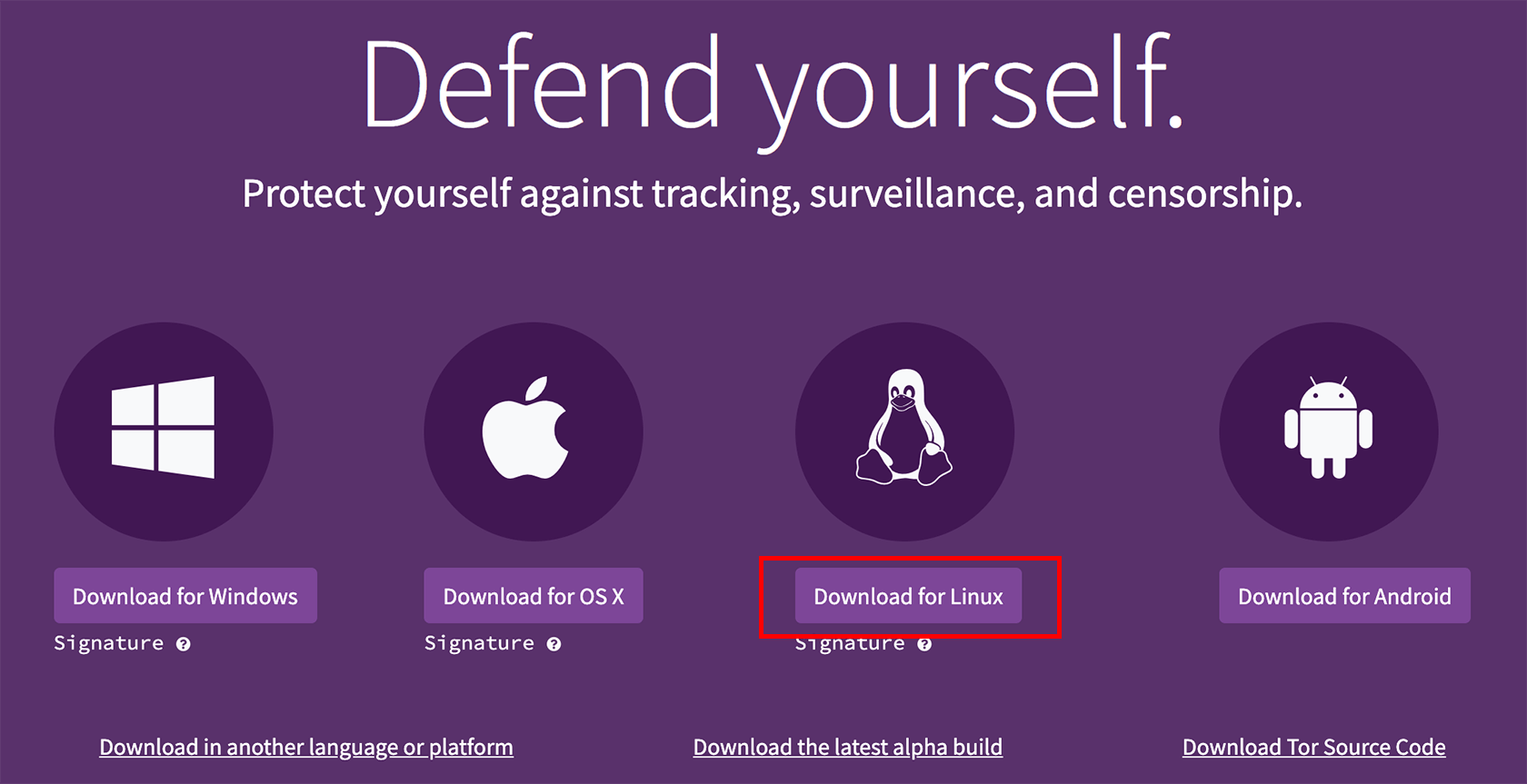
Wait for the setup file to download. After downloading, go to the directory, it was downloaded to. Right-click on the downloaded file and select Extract Here.
After Tor Browser setup files are extracted, double-click on Tor Browser Setup.
Congratulations! Tor Browser is installed, and you’re all set.
Mac
Click the “Download for OS X” button.
After the downloading is complete, open the Downloads folder and double-click on the file downloaded (TorBrowser-7.0.2-osx64_en-US.dmg).
After the installation is complete, a new window will pop up and request that you drag Tor Browser to the applications folder.
All done! Now Tor Browser is installed on your Mac.
Android
Click on the “Download for Android” button.
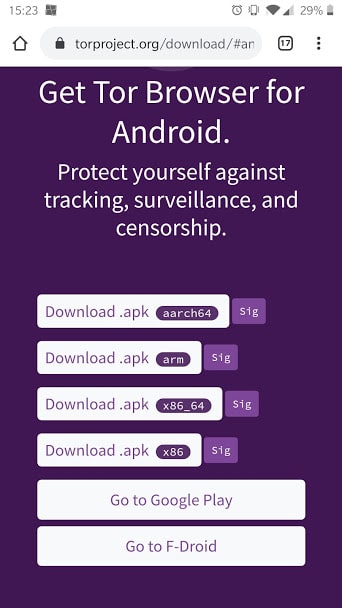
Then click Go to Google Play and tap Install.

After the installation is finished, tap Open to launch the Tor Browser application. Then tap Connect to start the connection to the Tor network.
And voila! Tor Browser is now installed on your Android device.
How to Use Tor Browser
Using Tor Browser is fairly straightforward. It’s much easier to start using Tor Browser than to explain how to do so!
But let’s give it a shot. First, launch Tor Browser by clicking on the “Start Tor Browser” shortcut on your desktop.
Tor Browser’s configuration window will pop up. Click Connect.
The Tor Browser homepage will open up in a new window. Now you can use Tor Browser.
Where to Start?
If you don’t know where to begin, that’s perfectly understandable. Since sites on the dark web aren’t meant to be indexed, and since they don’t have proper URLs, you’ll probably need to find initial Tor network ( sometimes called the “onionland”) links, to begin with.
Here are several articles with links to legal dark websites that will get you started:
- 10 Tor Websites To Visit For The Dark Web Experience
- 11 Most Interesting (Legal) Deep Web Sites
- The Top 80+ Websites Available in the Tor Network
- The top 9 .onion websites from the depths of the dark web
How to Uninstall Tor Browser
Uninstalling Tor Browser is pretty simple, too. For Windows, remove the Tor Browser folder. For Linux, delete the Tor Browser directory from your computer.
Fully uninstalling Tor Browser from a Mac is slightly more involved. You can uninstall Tor Browser manually by finding the appropriate folder and dragging it into the trash bin. But Tor’s service files will stay on your Mac and require some effort to be deleted.
So the better option, if you’re a Mac user, would be to use a third-party uninstalling tool for Mac. For example, Mac App Cleaner & Uninstaller, AppCleaner, or CleanMyMac 3 can do the job.
Using Tor Browser — Safety Tips
While using Tor Browser adds an extra layer of protection to your web browsing session, it’s not 100% full-proof. So here are a few basic recommendations to help you stay safe, secure, private, and legal when using Tor Browser.
Keep your personal information to yourself
To keep your identity private, avoid using your real email address, social network accounts, and anything that requires your info.
Tor Browser lets you stay anonymous, but giving up your personal information on websites could easily render the browser useless.
If you use the dark web and want to prevent your Tor activity from being traced, create a virtual identity that’s nothing like your real-world identity.
Consider using Linux instead of Windows
Many experts advise against using Windows for Tor browsing, as it has the highest number of vulnerabilities and bugs. These can be exploited to inject your system with malicious code or to compromise your confidentiality.
You’d be more secure if you could run Tor Browser on Linux.
Stay up to date
Keeping your Tor Browser client, Tor-secured applications, and other systems updated will save you from the latest detected vulnerabilities.
Disable JavaScript, Java, and Flash
Using active content on Tor is always risky. You should disable JavaScript, Java, and Flash components, such as Adobe Flash, QuickTime, ActiveX controls, and VBScripts.
Using these on Tor may expose your data since active content applications normally run with your user account privileges. This would allow websites to track you in ways Tor Browser can’t protect you from.
JavaScript, which is a powerful web development programming language, can be used to enable user tracking by websites despite configured proxy settings. The same goes for Java and Adobe Flash components running on virtual machines.
Don’t use P2P protocol and torrents
BitTorrent clients won’t typically encrypt your IP address, which could be shared with torrent trackers and peers. This is how peer-to-peer file sharing on Tor can quickly expose your identity.
Tor Browser Privacy and Security Details
It’s fair to say that, for the most part, Tor Browser will keep your content private and your identity secure. But keep in mind that 100% anonymity and privacy aren’t guaranteed.
Still, Tor Browser provides a reliable additional layer of security to protect your privacy and anonymity.
How Can Tor Browser Be Traced?
As previously mentioned, Tor Browser uses “onion routing” to protect your internet traffic and hide your identity and location. However, it has several weaknesses and isn’t 100% secure.
One of its vulnerabilities is that each server, which essentially operates as another relay in the Tor network, belongs to volunteers. So, users can’t be entirely sure about the security of each relay the data comes from.
This is mostly fine since the encryption allows each relay server to see only the locations of the last and the next. But the exit node removes the final layer of encryption and has access to the user’s original site.
So your location and identity could theoretically be traced by a server acting as an exit node in the Tor network.
Moreover, Tor Browser is also vulnerable to several potential hacker attacks (just like other browsers are). Ensure you minimize risk by following all the security tips and recommendations above.
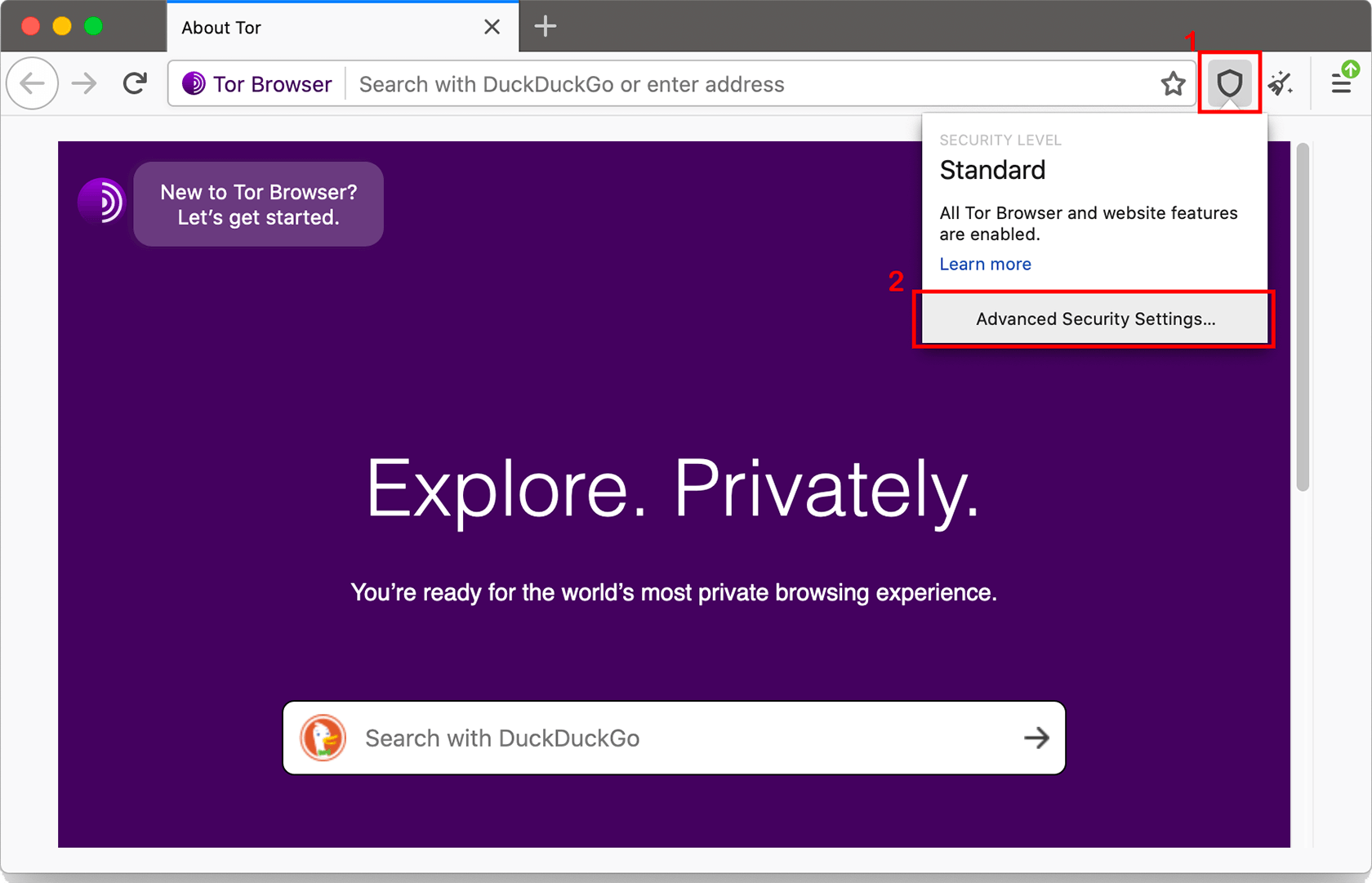
What Security Level Settings Are Built Into Tor Browser?
You have several options to disable certain web features that could otherwise compromise your security and anonymity.
Just set up Tor Browser’s Security Levels. Keep in mind, though, that increasing Tor Browser’s security levels may prevent certain web pages from functioning properly.
Security Settings
You can access security settings by clicking the shield icon next to the URL bar. Then click on Advanced Security Settings.
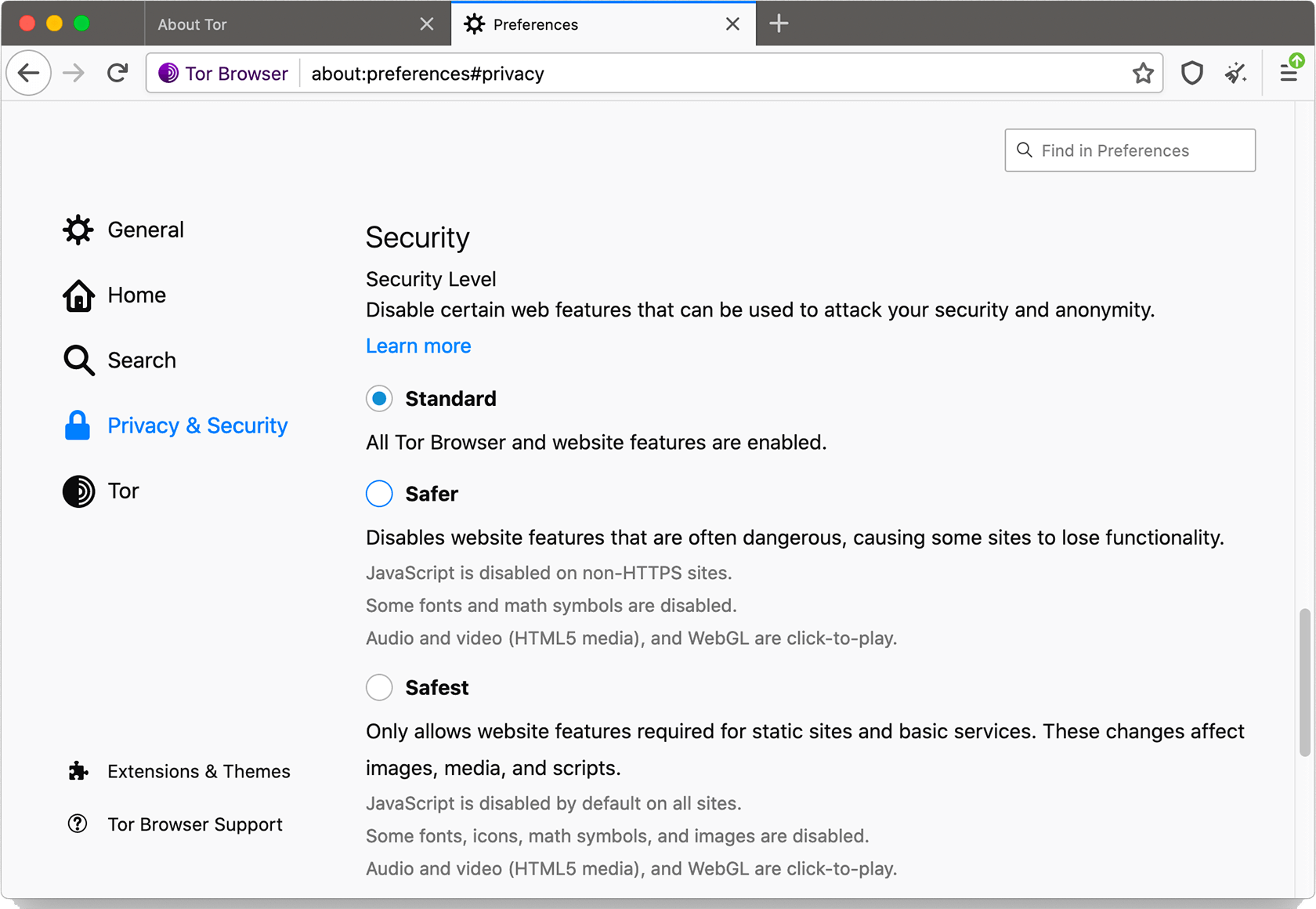
Security Levels
Tor Browser offers users three basic security levels: Standard, Safer, and Safest.
Standard
All Tor Browser and website features are enabled.
Safer
This disables website features often considered to be dangerous. Some sites will lose functionality.
- JavaScript is disabled on non-HTTPS sites
- Some fonts and math symbols are disabled
- Audio and video (HTML5 media), and WebGL, are rendered click-to-play
Safest
This level only allows website features required for static sites and basic services. These changes affect images, media, and scripts.
- Javascript is disabled by default on all sites
- Some fonts, icons, math symbols, and images are disabled
- Audio and video (HTML5 media) are rendered click-to-play
Tor Browser and VPN
Is Tor Browser similar to a VPN (Virtual Private Network), and do you need a VPN if you’re already using Tor?
Recall that Tor passes your data from one node to another while encrypting and then re-encrypting it. By contrast, a VPN provides you with a secure, encrypted connection to a remote server elsewhere.
So while Tor Browser and VPN are different, their functionalities complement each other. Using both would significantly increase your chances of staying anonymous and keeping your data private.
Turning a VPN on before you start using Tor Browser would allow you to hide your original location and IP address even from the exit node relay server, which, as you’ll recall, can trace your original location (in the absence of VPN functionality).
Can you still be traced when using Tor Browser with VPN?
Yes, but only if you’re not careful. Remember that a VPN allows you to completely hide your real IP address from any volunteer server in the Tor network.
Moreover, a VPN prevents your ISP from detecting that you’re using Tor, which your ISP would otherwise easily recognize.
A VPN lets you hide all your Tor activity from your ISP by providing you with a secure encrypted connection right from the start. Your VPN provider also won’t see your activity within the Tor network.
Combining Tor Browser with a VPN gives you pretty good privacy and anonymity. You could still be vulnerable, though, if you use active components while browsing through the Tor network or if you share any private data while on Tor websites.
The Dark Web and Alternatives to Tor Browser
Many other networks are similar to Tor, but they differ in how they’re built, how they approach the browsing process, and the goals they’re meant to achieve. The most popular alternatives to the Tor network include Freenet, I2P, Freepto, Tails, Subgraph OS, and more.
Check out our Tails VPN guide for more info.
Can you access the Dark Web without Tor Browser?
Sure. Several projects allow you to access the dark web using a regular web browser. Tor2web, which uses reverse proxies to allow users to access websites with .onion domain names, is the most well-known.
But before you try using Tor2web or one of its alternatives, be forewarned that it’ll most likely be unsafe.
Using the dark web without Tor Browser’s encryption means that your activity will be easily accessible to several parties, including your ISP and the operator of the reverse proxy you use to access the dark web.
So, even though it’s technically possible to use the dark web without Tor Browser or one of its alternatives, you’re better off not even trying it. And if you do, please don’t say we didn’t warn you!
Additional Info You Might Want to Know (or Brush Up On)
Tor History 101
How did Tor come to be?
You’ll recall that “Tor” is an acronym for the original name of this project: “The Onion Router.”
Onion routing was originally developed in the mid-1990s by the United States Naval Research Laboratory to keep the U.S. intelligence community’s online communication and data away from prying eyes.
The alpha version of The Onion Routing project, or Tor project, was developed by mathematician Paul Syverson and computer scientists Roger Dingledine and Nick Mathewson.
It was launched in September 2002, while the first public version of Tor was presented almost two years later, in August 2004. That same year, the source code of Tor was released by the Naval Research Laboratory under a free license.
In December 2006, Roger Dingledine, Nick Mathewson, and several other developers of Tor founded The Tor Project, which is a U.S.-based nonprofit organization responsible for maintaining Tor to this day.
Why was Tor Browser made public?
The goal was to use this new technology to protect internet users in the early 2000s from companies that wanted to collect their data.
At the time, Tor Project founders became increasingly concerned with emerging companies and websites that provided their services for free in exchange for user data. Why? Because that valuable data could be sold for profit.
So Tor Browser was publicly launched as a way for users to have full control over how their data might be used.
Dark Web 101
What is the Dark Web?
Simply put, it’s the part of the internet that exists on darknets, which requires specific software, configuration, or authorization to access.
The dark web content isn’t indexed by web search engines, making it part of the deep web, which covers all web content invisible to search engines.
The opposite of the dark web is the surface web (also called the visible or indexable web). The surface web is the part of the internet available to everyone and searchable by the usual search engines, like Google.
What’s the Dark Web Used For?
The dark web often conjures up images of some dark market, where illegal drugs, weapons, pornography, and various criminal services are sold.
But the truth is, the dark web isn’t inherently so nefarious. It’s just a more private segment of the internet that provides users with much higher levels of anonymity than the surface web.
And that’s why criminals love the dark web; it’s easier to run their operations discreetly without getting caught.
But again, this isn’t what the dark web is all about. Some of the most common legal and perfectly ethical resources exist on the dark web:
- Whistleblowing websites, where people with inside knowledge can post all kinds of sensitive information anonymously (WikiLeaks is probably the most famous example)
- Specialist forums, where professionals from specific fields can communicate with each other away from the general public’s eyes
- Large content directories, like The Hidden Wiki
- Other kinds of websites that share free content, like research papers, analytical reports, and more.
Is it illegal to use the Dark Web?
No, it’s not. But it’s illegal to use websites with illegal content (which, as we’ve already established, is plentiful on the dark web).
And, to state the obvious, any illegal activity stays illegal even if it was conducted on the dark web.




3 Comments
User
October 4, 2021 10:43 pm
“the exit node removes the final layer of encryption and has access to the user’s original location” – Wrong.
It is the payload of the packet that is encrypted, not the whole TCP packet. When the packet leaves the exit node, the return address is the address of the exit node.
Anonymous
July 15, 2023 12:11 pm
dm?
Nina
September 6, 2021 4:57 pm
Did not work for me. I have Linux. I downloaded several times. No .exe file, no setup/install prompt. Sigh.