Underground Ransomware Actor Breaches 11 Targets
The Underground ransomware gang announced a massive operation recently. The hackers listed 11 victims on their leak website, along with a short summary of each. The amount of data leaked varies between 35 GB and 1,6 TB.
- Neither of the victims has commented on the situation yet
- The Underground hackers also revealed each victim’s projected revenue, which will most likely influence the value of the ransom
- The gang poses as a cybersecurity professional, exposing the victims’ vulnerabilities and asking for payment in exchange for their services
- According to the reports, the hackers delete Volume Shadow Copies, which prevent the victims from decrypting the files themselves
Underground hackers use the double-extortion practice to force the victims into paying the ransom. They always leave a ransom note behind, containing information about the type of data they stole and where they’ve exfiltrated it.
The gang first emerged in July of 2023 and was involved in a handful of operations since. Unlike typical ransomware actors, the Underground team poses as cybersecurity experts, claiming to detect and solve system vulnerabilities.
While rare, this approach is not entirely unique, as other ransomware actors use it to various degrees of success.
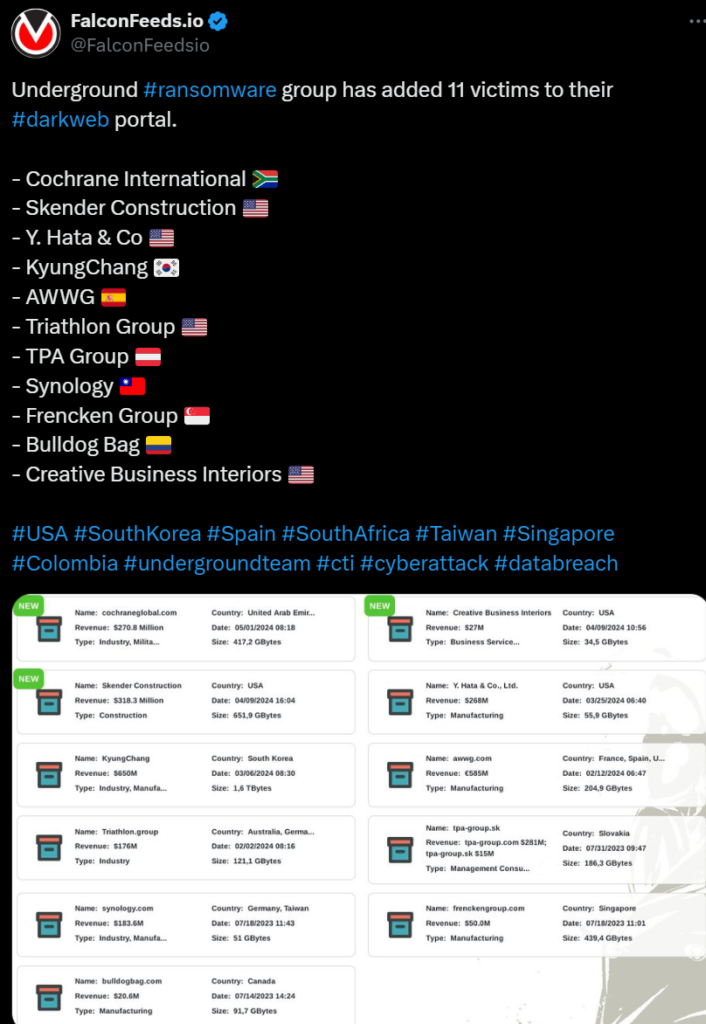
Underground’s victims qualify as medium-to-high-value with revenues varying between $20 million and $650 million. It’s unclear how many of them have decided to contact the hackers at this point.
The victims are located in several countries, including South Korea, South Africa, Singapore, and the US. This shows that the Underground team has already become a global player in less than a year since its inception.
Who Is Underground?
There are some conflicting reports and theories at play regarding Underground’s actual identity. One such theory claims that the gang is the successor of the infamous Industrial Spy ransomware that was active during 2022. This hasn’t been confirmed yet.
No matter its descendance, Underground proved itself to be worthy of attention. The gang appears to be extremely effective at detecting and breaching high-value targets. They also demand extremely high ransoms, based on the victim’s revenue.
In one instance, the ransom got as high as $3 million.
The primary MO is standard. The hackers identify their target of choice, breach it, deletes the backup copies of the files, and encrypts specific files and directories. They then exfiltrate the target data and leave the ransom note behind.
An interesting point here, the operators don’t change the name of the encrypted files and don’t add any extension. The victim only discovers that they’re inaccessible when attempting to activate them.
All victims get a 3-day deadline to pay the ransom. If not, the hackers threaten to leak the data online. There is no clear data regarding how Underground conducts negotiations or how reasonable they are. But the expectations should be set quite low.
Experts advise victims to adopt a no-negotiations policy. In case of an attack, the standard recommendation is to disconnect the compromised device from the network. You should also scan for any suspicious activity or have a professional do it for you.
And, whatever you do, never negotiate and never pay the ransom.
Our Mission
We believe security online security matters and its our mission to make it a safer place.

