Hackers Sell Access to Argentine Government Communications & ID Card Data of Millions
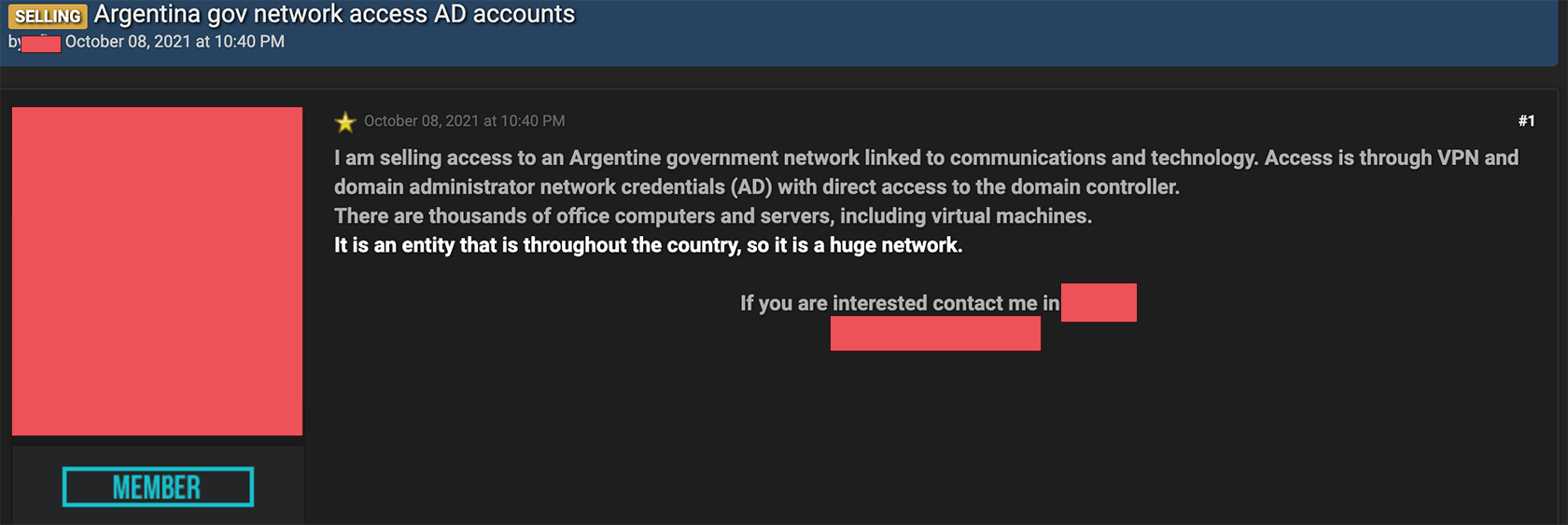
An unknown hacker or hacker group claims to sell access to an Argentine government network linked to internal communications and technology.
The same hackers claim to possess sensitive ID card data on millions of Argentine citizens.
Seller is the same entity that released the confirmed IOSFA leak a few weeks ago that allegedly affected over 1 million Argentine military personnel.
Highlights:
- Hackers claim to sell access to an Argentine government network linked to communications
- Claim to have access to thousands of office computers and servers of various Argentine government agencies
- Claim to posses ID card data of millions of Argentinians
- Card data includes: photo, name, address, processing number, type of ID, and code located on the back of the card
- Seller is the same person or group who released the confirmed IOSFA leak
Today on a popular dark web hacker forum, an unknown hacker or hacker group claims to possess the means to access a sensitive and restricted Argentine government network linked to communications and technology.
The hackers claim they have access to thousands of office computers and servers, including virtual machines belonging to various Argentine government agencies.
Allegedly, interested buyers can buy access – which will be carried out through a VPN – and domain administrator network credentials with direct access to the domain controller, that will allow them to access the communications network of the Argentine government.
Same Seller Who Leaked IOSFA Data
The seller is the same individual or group who released sensitive data on more than one million members of various Argentine military branches and police agencies a few weeks ago.
Privacy Affairs broke the previous story on September 29. The next day, the IOSFA (Institute of Social Work of the Armed Forces) confirmed that the database leak had occurred; however, it added that the data was outdated.
In both of these instances, the alleged seller was the same forum poster, raising the strong possibility that this new breach may also be legitimate.
Also Sells Sensitive ID Card Data
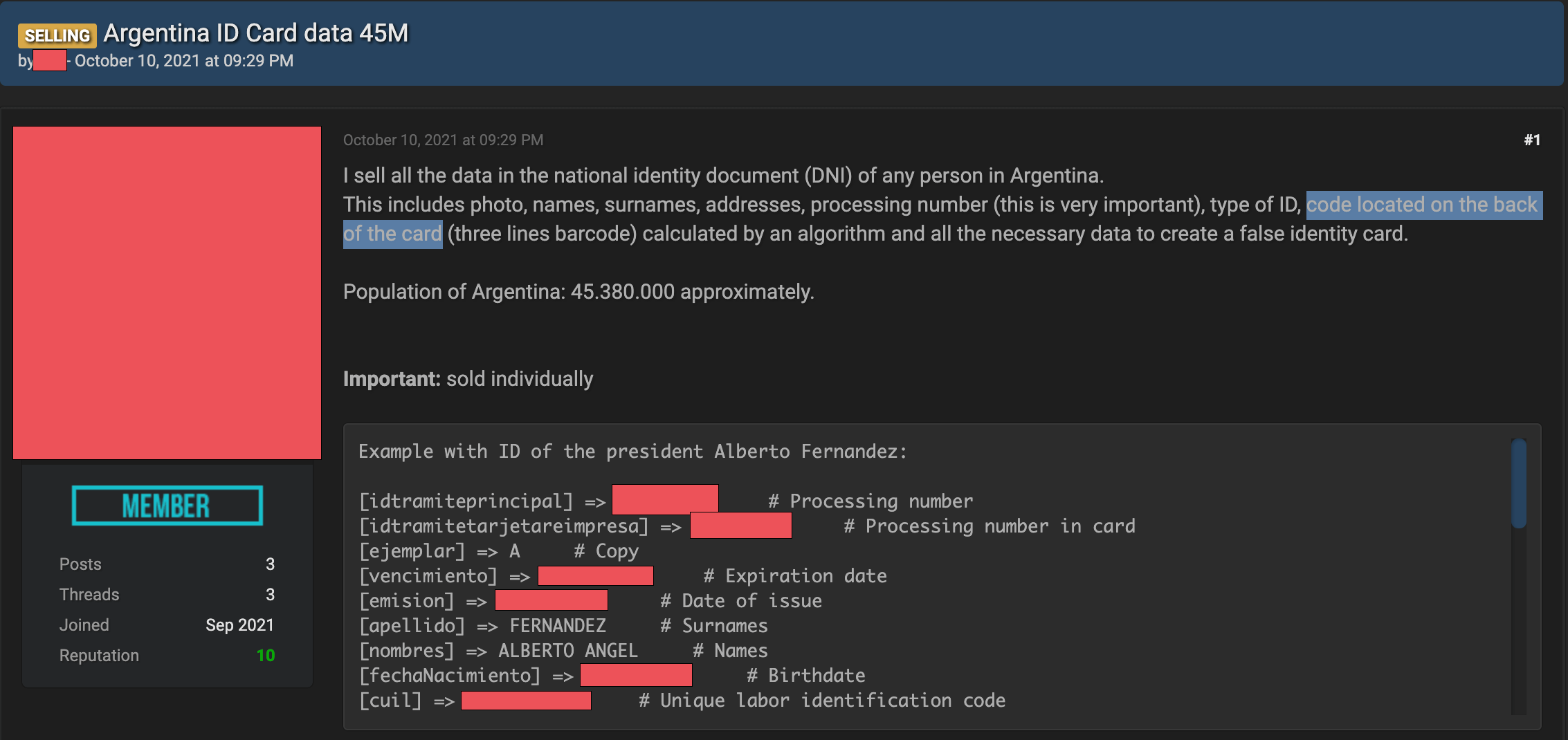
The same seller involved in the two leaks mentioned above has a third forum thread claiming to possess and sell personal data on nearly all Argentine citizens.
The forum post claims that buyers can get ID card data on nearly every Argentine citizen on request. The seller intends to sell these on an individual basis.
The hacker claims that they have data on several million Argentine citizens.
The data allegedly includes information such as photos, names, surnames, addresses, processing numbers, type of ID, and code on the back of the card (three lines barcode) calculated by an algorithm.
The hackers claim that the processing number and the code on the back of the card will allow criminals to create authentic-fake ID cards.
It is unclear if this data leak is real – but we again want to point out that this is the same seller as the one who earlier leaked the officially confirmed IOSFA leak.
If real, the hackers may appear to be a sophisticated threat actors who managed to penetrate the Argentine government’s IT infrastructure.
We will update this story as more details emerge.
Our Mission
We believe security online security matters and its our mission to make it a safer place.