Biggest Cybersecurity Attacks Worldwide in 2023
Cybercrime has become a foremost threat to businesses and organizations in 2023. A Statista study shows that 36% of board members around the world are most concerned about data leaks caused by cyberattacks.
Another 36% are more worried about a disruption to their operations, while 34% fear reputational damage the most when it comes to cyberattacks.
Yet another study shows that 31% of businesses around the world think that the most important consequence of a cyberattack is the cost associated with notifying customers.
In this article, I’ll explore the biggest global cyberattacks in 2023. Here’s a summary of all the attacks throughout the year and the number of records breached:
| Cyberattack | Records Breached/People Affected |
| DarkBeam | 3.8 billion records exposed |
| ICMR Indian Council of Medical Research | 815 million records exposed |
| 220 million profiles leaked | |
| Tigo | 100 million records leaked |
| MOVEit | Over 77 million people affected |
| Luxottica | 74.4 million records leaked |
| UK Electoral Commission | 40 million records exposed |
| T-Mobile | 37 million records stolen |
| Indonesian Immigration Directorate General | 34.9 million passport records leaked |
| 23andMe | 20 million records stolen |
| PeopleConnect | 20 million records stolen |
| Latitude Financial | 14 million records stolen (8 million drivers’ licenses and 6 million other records) |
| Redcliffe Labs | 12 million patient records stolen |
| JD Sports | 10 million customer records leaked |
| Pôle employ | 10 million records exposed |
| AT&T | 9 million customer records exposed |
| MCA Insurance | 8.9 million records leaked |
| University of Minnesota | 7 million Social Security Numbers exposed |
| Elevel | 7 million data entries leaked (1.1 TB of data) |
| Oregon and Louisiana Departments of Motor Vehicles | 6 million records exposed |
| PharMerica | 5.6 million patient records breached |
| Better Outcomes Registry & Network (BORN) | 3.4 million patient records exposed |
| Teachers Insurance and Annuity Association of America | 2.6 million client records compromised |
| Genworth Financial | 2.5 million client records exposed |
| Shields Health Care Group | 2.3 million records leaked |
| Undisclosed Restaurant Database | 2.2 million data records leaked |
| Wilton Reassurance | 1.4 million insurance records leaked |
| NCB Management | 1 million financial records stolen |
| CentraState Medical Center | 617,000 sensitive patient records stolen |
| Kodi | 400,636 user records stolen |
| GoAnywhere | Over 130 organizations targeted |
This year was quite the roller-coaster from a cybersecurity standpoint. All in all, over 5.3 billion records were breached in over 953 incidents.
Let’s have a look at each one down below!
1. DarkBeam

https://techspark.co/company/darkbeam/
- When: September 18th, 2023
- What: 3.8 billion records exposed
- How: Misconfigured Elastisearch and Kibana interface
On September 18th, 2023, the CEO of SecurityDiscovery discovered that DarkBeam had “left an Elastisearch and Kibana interface unprotected, exposing records with use emails and passwords from previously reported and non-reported breaches.”
DarkBeam patches the vulnerability right away once it was announced but the fact still stands – more than 3.8 billion records had been exposed publicly.
These records are mainly from previous data breaches, with DarkBeam having gathered them to alert its customers to security incidents, but the data breach took place this year.
It’s quite ironic that a data dump meant to protect its clients ended up causing another massive data breach, impacting its customers.
It’s not clear whether someone accessed it or not but the way the data was structured, it would allow anyone to carry out extensive phishing campaigns with a high degree of credibility.
2. ICMR Indian Council of Medical Research

https://en.wikipedia.org/wiki/Indian_Council_of_Medical_Research
- When: October 9th, 2023
- What: 815 million records of Indian residents exposed
- How: Unclear how the data breach took place
On October 9th, 2023, the security company Resecurity discovered that there were over 815 million records of Indian residents for sale on the Dark Web.
The listing contained data such as names, ages, genders, passport numbers, addresses, and Aadhaar numbers (Indian identification numbers).
It’s possible that the breach originated on the ICMR’s Covid-testing database but there’s not enough evidence to make matters clear.
The identity of the threat actor who leaked the data is also unclear, as the ICMR has not issued any statements. In fact, they’ve even refused to acknowledge the existence of the data breach.
The threat actor has also shared several spreadsheets containing the four leak samples showing the Adhaar data to validate their threats.
They go by the alias “pwn0001” and they’ve posted the threat on October 9th on Breach Forums. Apparently, the hacker was trying to sell the entire data dump for $80,000.
3. Twitter

https://www.digidop.fr/en/blog/twitter-x-new-logo-identity-challenges-elon-musk
- When: January 5th, 2023
- What: 220 million Twitter profiles leaked
- How: Unclear how the data breach took place but it might be a part of an older data breach
On January 5th, 2023, hackers stole over 200 million X (Twitter) profiles and put them up for sale on an online hacking forum after the company refused to negotiate with them.
The hacker, named “Ryushi“, asked for $200,000 to delete the data or give it back. However, X refused to comply and that made the situation worse.
The good thing is that the data is only comprised of email addresses, so at the very least, the victims are not in immediate danger. Phishing, on the other hand, is a real risk.
Alon gal, the co-founder of the Hudson Rock cyber-crime intelligence firm who found the data dump said that “This database is going to be used by hackers, political hacktivists and of course governments to harm our privacy even further.“
4. Tigo

https://play.google.com/store/apps/details?id=com.tigo.flower&hl=en_SG&gl=US
- When: March 31st, 2023
- What: 100 million records belonging to over 700,000 people were leaked
- How: Unknown
Tigo is a Chinese online messaging platform, and it’s one of the most popular ones in the country.
On March 31st, 2023, a data breach took place that involved over 100 million records belonging to over 700,000 people.
The data included names, usernames, profile photos, genders, email and IP addresses, geographic locations, and private messages.
The HaveIBeenPwned platform added the Tigo entry on the 24th of July, so four months after the data breach.
Tigo offered no explanations or any official statements so far, and we don’t know anything about the origin of the attack or what happened to the data afterward.
In total, the data amounted to 300GB, so it was a very sizeable data leak, which could endanger a lot of people.
5. MoveIT

https://www.malwarebytes.com/blog/news/2023/07/moveit-transfer-fixes-three-new-vulnerabilities
- When: May 2023
- What: Data stolen from over 2,600 public, government, and business organizations all over the world through MOVEit’s systems, affecting more than 77 million people
- How: Zero-day vulnerability used to access MOVEit’s systems with the purpose of data theft
In May, the enterprise file transfer tool MOVEit reported that it became the victim of a particularly troublesome ransomware attack from the Clop hacker group.
The hackers used a zero-day vulnerability dubbed CVE-2023-34362 to gain access to thousands of clients of MOVEit. Even though a patch soon came out, not everyone was aware of it or installed it.
Clop provided a deadline (June 14th) for all the affected companies to contact them, and on that day, they named 13 of the affected companies were named, with many more in the following days.
They threatened to publicize the stolen data by June 21st if the victims refused negotiations but they changed their mind and recently stated that they’d deleted all the data stolen because they had “no interest to expose such information”.
At the time of writing this article, it is estimated that the MOVEit data breach affected over 2,600 organizations and more than 77 million people.
6. Luxottica

https://www.cascade.app/studies/luxottica-strategy-study
- When: 2021 (confirmed in 2023)
- What: 74.4 million records of 77 million accounts were leaked
- How: Unknown attack method
On April 30th and May 12th, 2023, the Luxottica database containing 74.4 million records stolen in November of 2021 was finally leaked publicly.
Andrea Draghetti, a leading researcher for Italian cybersecurity firm D3Lab said that the data dump contains 2.6 million unique domain email addresses.
Luxottica only learned of it in November 2022 when a post popped up on the dark web, describing the data breach.
The company reported the incident to the FBI and the Italian police, and the dark web site was closed, with its owned arrested by the FBI.
However, that didn’t count for much because now the data has been leaked online for free, and it’s unclear who leaked it.
Luxottica hasn’t made any official statements yet but the size of the data breach is huge.
7. UK Electoral Commission

https://en.wikipedia.org/wiki/Electoral_Commission_(United_Kingdom)
- When: August 8th, 2023
- What: 40 million records exposed publicly
- How: Potential vulnerability exploited by hackers
On August 8th, 2023, the Electoral Commission made a public statement about a “complex cyber-attack“ that resulted in a leak of 40 million records.
The data contained names, addresses, email addresses, telephone numbers, as well as the date on which the individuals achieved voting age. Apparently, the hackers had managed to access the Electoral Commission’s servers and hijack the control systems, stealing data between 2014 and 2022.
The incident originated in August 2021 when suspicious activities had been identifies on the systems. Though, at the time, the Commission ignored it only to realize what it was back in October 2022.
The plot thickens, though. A whistleblower told the BBC that the Commission had recently failed the Cyber Essentials audit right when the data breach happened.
Security researcher Kevin Beaumont also claimed that the Commission had been using an unpatched version of Microsoft Exchange Server that would have easily been breached by ProxyNotShell attacks.
While this hasn’t been proven, it stands to reason to assume that the hackers could have exploited a vulnerability in the Commission’s weak security system.
8. T-Mobile

https://en.wikipedia.org/wiki/File:T-Mobile_2020.svg
- When: Discovered on January 5th, 2023
- What: 37 million records stolen
- How: The hacker abused the API of the company to steal the data
On January 5th, 2023, T-Mobile officially announced that they’d discovered a data breach that resulted in the theft of 37 million customer records.
According to T-Mobile, “The preliminary result from our investigation indicates that the bad actor(s) obtained data from this API for approximately 37 million current postpaid and prepaid customer accounts, though many of these accounts did not include the full data set.”
More importantly, the data breach apparently took place on November 25th, 2022. However, T-Mobile only discovered the malicious activity on January 5th, 2023, nearly a month and a half later.
As soon as they found the data breach, they alerted the U.S. federal agencies and have been investigating it every since. Fortunately, they seem to have contained the data breach relatively quickly.
T-Mobile does have a history of data breaches, though. Since 2018, it suffered 8 data breaches, which ended up exposing the data of millions of customers.
9. Indonesian Immigration Directorate General

https://en.wikipedia.org/wiki/Directorate_General_of_Immigration
- When: July 2023
- What: 34.9 million passport records leaked posted on the dark web for $10,000
- How: Unclear how the hacker gained access to their systems
In July 2023, cybersecurity research Teguh Aprianto disclosed a data breach to the Indonesian Immigration Directorate General. He also identified the hacker as the hacktivist Bjorka.
Apparently, after stealing the 34.9 million data dump, he put it up for sale on the dark web for $10,000. The data included:
- Full names
- Passport numbers
- Dates of issue
- Expiry dates
- Gender
- Dates of birth
Andrew Whaley, the Senior Technical Director at Promon, said that “The biggest real-world consequence of a breach like this is identity theft. With passport data being sold on the black market, this could lead to many of the sufferers of this breach finding that criminals have fabricated counterfeit travel documents or even opened bank accounts in their name.”
It’s still unclear how the hacker infiltrated the Directorate General’s servers, but it’s safe to assume they found and exploited a vulnerability.
10. 23andMe

https://www.performancemenu.com/article/180/23andMe-DNA-Decoding-A-Review/
- When: October 2nd, 2023
- What: 20 million records stolen
- How: The hacker gained access to the company’s servers through credential stuffing attacks
On October 2nd, 2023, a member of an online forum claimed that they’re selling 20 million records from DNA testing company 23andMe. They also posted a sample from the data dump, which was apparently real.
23andMe started investigating the situation and made an official statement afterward, stating that “certain 23andMe customer profile information was complied through unauthorized access to individual 23andMe.com accounts / no indication at this time that there has been a data security incident within our systems.”
According to their investigation, the attacker compiled login credentials from various platforms and accessed 23andMe user accounts using the right username-password combinations.
The stolen data included display names, sex, birth year, profile photo, location, DNA match percentage, predicted relationship to their match, segments of their genetic ancestry results, and more.
After posting the data for sale on October 2nd, the hacker took it down and then made another listing, this time opting for a more specific sale description.
They were selling the data dump in sets of 100, 1000, 10000, and 100000 profile batches. It’s unclear how the data was stolen, though.
11. PeopleConnect

https://www.facebook.com/photo/?fbid=457254426424679&set=a.457254396424682
- When: January 21st, 2023
- What: 20 million records stolen
- How: The hackers leaked a 2019 backup database that contained 20 million customer records
PeopleConnect is the company behind Instant Checkmate and TruthFinder. On January 21st, 2023, a backup database containing customer records from these two companies was leaked online.
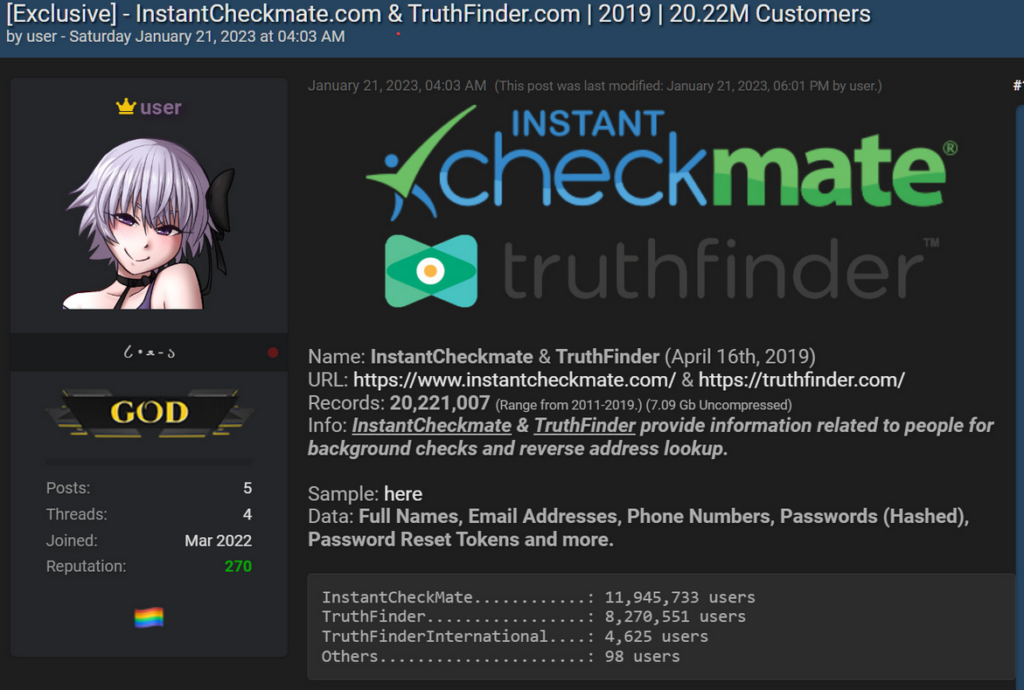
https://www.bleepingcomputer.com/news/security/truthfinder-instant-checkmate-confirm-data-breach-affecting-20m-customers/
The data came in CSV files totaling 2.9GB, and it contained customer information up to April 16th, 2019. The data included email addresses, first and last names, phone numbers, hashed passwords, and password reset tokens.
PeopleConnect published data breach notices on both TruthFinder and Instant Checkmate, saying that “We learned recently that a list, including name, email, telephone number in some instances, as well as securely encrypted password and expired and inactive password reset tokens, of TruthFinder subscribers was being discussed and made available in an online forum.”
According to their investigation, this event was either a theft or an inadvertent leak but their network hasn’t been breached. That’s good news, at least.
12. Latitude Financial

https://en.wikipedia.org/wiki/Latitude_Financial_Services
- When: March 16th, 2023
- What: 8 million drivers’ licenses and an additional 6 million records dating back to 2005
- How: An employee’s login information was stolen, which provided access to the company’s service providers that held the customer data
On March 16th, Australian loan FinService company Latitude Financial warned its customers about a data breach that affected 328,000 individuals.
A couple of days later, they released an updated notification, increasing the number of affected individuals from 328,000 individuals to 14 million.
In the new notification, the company states “As our forensic review continues to progress, we have identified that approximately 7.9 million Australian and New Zealand driver license numbers were stolen. […] A further approximately 6.1 million records dating back to at least 2005 were also stolen.”
The threat actors also managed to steal around 53,000 passport numbers, and Latitude said that they’d reimburse anyone who wanted to replace their ID documents.
In the notification, Latitude also offers defense advice against phishing and other cyberattacks, as well as steps to enroll for protection services.
The worst part about this data breach is the gross underestimation of the data breach size in their initial statement. This likely led to a loss of trust with many of their customers due to the significant difference between the first and second data breach report.
13. Redcliffe Labs

https://www.facebook.com/photo/?fbid=655889053229844&set=a.649582713860478
- When: October 2023
- What: 12 million patient records (7TB) exposed in an unsecured and publicly-accessible database
- How: Human error
In October 2023, cybersecurity expert Jeremiah Fowler discovered a publicly-accessible database that contained medical data of over 12 million patients. The database had a total size of 7TB, so it was quite sizeable.
After some investigation, Fowler found that the database belonged to Redcliffe Labs, an India-based company offering diagnostic services.
Upon being notified of the data breach, Redcliffe Labs immediately restricted public access to the database and it’s currently unclear whether any bad actors managed to access it in the meantime.
The database contained the following records:
- 620.5 GB (1.18 million) worth of records marked as “Records“, which also contained test results
- 1.5 TB (1.164 million) worth of records that showed test results using infographics
- 2.2 TB (6.09 million) worth of records named “Test results”
- 2.7 GB (3.9 million) worth of records containing logging records, mobile application files, internal business documents, and development files
Chief Technology Officer at Redcliffe, Prabhat Pankaj, stated that “We’d like to emphasize that all our databases are stored within private VPCs, making them inaccessible to the public, even with credentials. They are further safeguarded by encryption at rest.”
Even though the company has assured the public that they’re using the latest in cybersecurity protection, the 12 million data dump speaks otherwise.
According to Fowler, the database was unprotected by a password or encryption. As of right now, it’s unclear if any threat actors have accessed the data. Only time will tell.
14. JD Sports

https://en.wikipedia.org/wiki/JD_Sports
- When: January 2023
- What: Personal information of 10 million customers has been leaked
- How: Unclear how the hackers got the data
In January 2023, fashion retailer JD Sports said that there’s been a data breach where the personal data of 10 million customers has been leaked.
The data included names, phone numbers, billing and delivery addresses, order details, as well as the four digits of the victim’s payment cards.
Passwords and full payment data were not breached, according to the company. However, this much data is enough to launch phishing attacks.
The exposed data is from customers who ordered from JD Sports between November 2018 and October 2020, with purchases from brands like Millets, Scots, Blacks, Size?, and Millets Sports being most affected.
Neil Greenhalgh, the company’s Chief Financial Officer, said that “We are advising them [customers] to be vigilant about potential scam emails, calls and texts and providing details on how to report these.”
The company has begun working with a cybersecurity company to investigate the data breach and so far, we have no further details.
15. Pôle emploi

https://fr.wikipedia.org/wiki/P%C3%B4le_emploi
- When: April 2023
- What: 10 million records exposed
- How: Part of the MOVEit data breach
The French unemployment agency, Pôle emploi, has experienced a data breach in April 2023 that was associated with the MOVEit data breach in May 2023.
The exposed information included full names and social security numbers. Thankfully, email addresses, banking data, and passwords have not been exposed.
6 million of the affected individuals have registered in the unemployment centers by February 2022 and the other 4 million have registered in the last 12 months before the attack.
Pôle emploi has created a dedicated phone support line where they offer assistance to the concerns of the affected victims and provide more information about the incident.
The company has also clarified that the data breach has not affected its financial aid program or the online platform. So, job seekers can safely access their online portal using their passwords.
The MOVEit data breach is estimated to have affected over 1,000 organizations and over 77 million people. But the full extent of the data breach has not been determined yet.
16. AT&T

https://en.wikipedia.org/wiki/AT%26T_Internet
- When: January 2023
- What: 9 million records of customers exposed in a data breach
- How: Unclear how the data breach happened
In January 2023, AT&T suffered a data breach where 9 million customers were affected. The company only found it two months later, in March, and notified the affected customers.
The leaked information included names, wireless phone numbers, email addresses, and wireless account numbers. Fortunately, there was no credit card information included in the data dump.
AT&T said that “A small percentage of impacted customers also had exposure of rate plan name, past due amount, monthly payment amount, various monthly charges and/or minutes used. The information was several years old.”
They alerted law enforcement agencies as soon as they became aware of the breach, and then notified its customers to turn off their CPNI data sharing in their accounts.
Apparently, AT&T’s systems have not been affected since the current breach originated in one of their vendor’s systems. The vendor has not been named, however.
17. MCNA Insurance

https://www.mcnatx.net/
- When: March 6th, 2023
- What: 8.9 million data records exposed, including full names, addresses, phone numbers, email addresses, dates of birth, social security numbers, driver’s license numbers, ID numbers, health insurance information, bills and insurance claims, and other data
- How: Lockbit ransomware group claimed the attack
On March 6th, 2023, the Managed Care of North America Dental (MCNA) experienced a data breach where the personal data of 8.9 patients was exposed.
The Lockbit ransomware group had gained unauthorized access to its systems and stolen multiple sets of data, including:
- Full names
- Physical addresses
- Email addresses
- Phone numbers
- Dates of birth
- Driver’s license numbers
- Social Security numbers
- ID numbers
- Health insurance information (insurance company, plan information, member number, and Medicaid-Medicare ID numbers)
- Care for teeth or braces data (number of visits, dentist name, past care, doctor name, medicines and treatment, x-rays/photos)
- Bills and insurance claims
The company notified the Attorney General immediately and then taken several steps to remedy the situation and improve its security systems.
Lockbit then threatened to publicly expose all the stolen data (700GB) and demanded a ransom of $10 million. On April 7th, 2023, Lockbit publicized all the stolen MCNA data on its website.
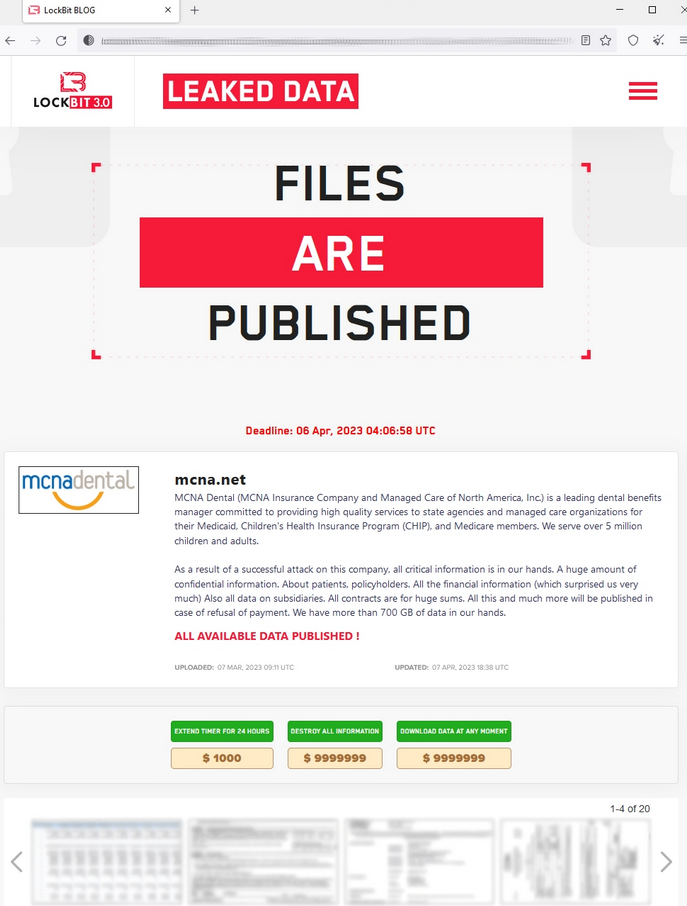
https://www.bleepingcomputer.com/news/security/mcna-dental-data-breach-impacts-89-million-people-after-ransomware-attack/
It became publicly accessible by anyone, so at this point, the data has likely been obtained by other bad actors who will use it maliciously.
Targeted phishing emails and other social engineering attacks will likely ensue as a result, and MCNA recommends that all affected users monitor their credit reports.
18. University of Minnesota

https://facts.net/world/landmarks/9-astonishing-facts-about-university-of-minnesota/
- When: July 21st, 2023
- What: 7 million Social Security Numbers exposed
- How: No information provided on how the data breach occurred
On July 21st, 2023, the University of Minnesota learned that a threat actor has stolen 7 million unique Social Security Numbers from their digital database.
After the investigation, they found that there was no malware, phishing email, or other disruption involved. In short, they don’t know how the data breach occurred.
Moreover, the data seems to be dated 2021 and earlier, up until 1989 when the university started digitizing its databases.
“Our investigation is continuing, but our security professionals have not detected any system malware (including ransomware), encrypted files or fraudulent emails related to the incident. There have been no known disruptions to current University operations as a result of this data security incident,” the university stated.
They also mentioned that they’ll notify the affected individuals and offer resources for additional protection against any misuse of their personal information.
19. Elevel

- When: January 24th, 2023
- What: 7 million data entries leaked, a total of 1.1 TB of data
- How: Unclear how the data was leaked
On January 24th, Cybernews discovered a data breach comprised of 1.1 TB of data that was attributed to Elevel – a Russian electrical engineering company.
The company has multiple wholesale stores as well as an e-commerce business. And the data leak contained 7 million data entries spread over two years. The data included names, surnames, email addresses, phone numbers, and delivery addresses of the customers.
https://cybernews.com/privacy/russian-e-commerce-giant-data-leak/
https://cybernews.com/privacy/russian-e-commerce-giant-data-leak/[/caption]
Cybernews stated that “If left exposed, threat actors could download and clone the cluster’s data and use for nefarious purposes, including phishing attacks, as they possess sufficient PII (Personally Identifiable Information) and the make their scam seem legitimate.”
The data dump also contained the clients’ login credentials (including passwords) in URL encoding. This is a very weak encryption standard according to most experts, so we can assume that this poses quite a risk to the exposed Elevel customers.
The good thing is that the data leak was officially “plugged“, according to Cybernews. There’s no more risk of bad actors getting their hands on Elevel customers’ private data.
20. Oregon and Louisiana Departments of Motor Vehicles

https://mypharmerica.com/
- When: June 2023
- What: 6 million records exposed
- How: Part of the MOVEit data breach
In June 2023, the Oregon and Louisiana Departments of Motor Vehicles reported a data breach caused by the MOVEit Transfer data breach.
In total, 6 million records were exposed, containing the following information:
- Names
- Addresses
- Height
- Eye color
- Social Security numbers
- Birth date
- Driver’s license number
- Handicap placard information
- Vehicle registration information
The Louisiana OMV stated that “Louisiana’s Office of Motor Vehicles is one of a still undetermined number of government entities, major businesses and organizations to be affected by the unprecedented MOVEit data breach.”
They haven’t found any evidence of the data being sold on the dark web or used in any malicious activities, though. That’s not to say this won’t happen in the future.
The MOVEit ransomware hacker group did promise that they would delete the stolen data but can we really trust the words of criminals?
At the same time, the Oregon DMV also reported a data breach where 3.5 million Oregon residents had their IDs or driver’s licenses exposed through the MOVEit data breach.
Oregon residents should still take precautions against extortion attempts by any bad actors who are in possession of their private information.
21. PharMerica

https://mypharmerica.com/
- When: March 2023
- What: 5.8 million patient records breached
- How: Ransomware group Money Message gained unauthorized access to the company’s database
In March 2023, PharMerica and its parent company, BrightSpring Health Services, were hacked by the Money Message ransomware group.
After gaining unauthorized access to the databases, the hackers exfiltrated with 4.7 TB of data, amounting to patient data of over 5.8 million patients. The data included names, addresses, dates of birth, Social Security numbers, health insurance data, and medical data.
PharMerica had sent data breach notifications to all the affected patients between March 12th and March 13th. In many cases, the compromise data belonged to deceased individuals, so the company encouraged family members to contact the national credit reporting agencies about the data breach.
PharMerica doesn’t state how the attack took place but we do know that the Money Message ransomware group is responsible.
Apparently, the group started leaking the stolen information publicly in April after claiming that they’d engaged in negotiations with PharMerica. It’s likely that the company refused to pay, and so the hackers leaked the information.
PharMerica hasn’t mentioned any ransom in their public statements or their data breach disclosure, though. They might have wanted to save their reputation and omit these details intentionally.
22. Better Outcomes Registry & Network

https://www.bornontario.ca/en/about-born/about-born.aspx
- When: May 31st, 2023
- What: 3.4 million patient records exposed
- How: Part of the MOVEit data breach
On May 31st, 2023, BORN (Better Outcomes Registry & Network) became aware of a data breach involving personal health information dated January 2010 – May 2023. The data belonged to pregnant women and newborns.
The data included full names, dates of birth, postal codes, home addresses, health card numbers, and in some cases, lab test results, dates of service/care, procedures performed, pregnancy and birth outcomes, risk factors, and types of birth.
In total, there were 3.4 million patients affected by the data breach, with the data being collected from multiple BORN healthcare facilities in Ontario.
After they found the data breach, BORN notified the proper authorities and posted a public notice on their website. We still don’t know whether the bad actors made the data public or whether they negotiated a deal with BORN.
There hasn’t been any evidence about the data being put up for sale on the Dark Web either. But this doesn’t mean it won’t happen in the future.
It’s important to note that the BORN data breach was caused by the MOVEit fiasco which is still affecting organizations all over the world months after it happened.
23. Teachers Insurance and Annuity Association of America

https://upload.wikimedia.org/wikipedia/commons/2/26/Teachers_Insurance_and_Annuity_Association_of_America-College_Retirement_Equities_Fund_logo.svg
- When: July 14th, 2023
- What: 2.6 million client records compromised
- How: Part of the MOVEit data breach; its vendor, Pension Benefit Information, was attacked and led to an infiltration to TIAA systems
Another victim of the MOVEit data breach, the TIAA (Teachers Insurance and Annuity Association of America) reported a data breach on July 14th, 2023.
The non-profit organization provides financial services for those in academic fields, and they had been using MOVEit. The company notified the Maine Attorney General on July 14th, and the scale of the attack became public knowledge.
One of its vendors, Pension Benefit Information, was compromised in an attack, and this allowed access to the TIAA systems. It was a supply-chain attack, in other words.
A class action lawsuit was opened against TIAA, and the plaintiff, Gayle Jentez, claimed that the organization had not implemented the necessary security measures to protect the personal data.
The data exposed included names, dates of birth, addresses, genders, and Social Security numbers. And apparently, the victims saw an increase in the number of spam texts and calls, email messages, and a general invasion of their privacy as a result of the breach.
24. Genworth Financial

https://www.genworth.com/content/dam/Americas/US/Images/Public/Logos/genworth-og.jpg
- When: May 31st, 2023
- What: 2.5 million client records leaked (including names, dates of birth, physical addresses, policy numbers, and Social Security numbers)
- How: Part of the MOVEit data breach; Genworth Financial’s vendor was hacked, which allowed the threat actors to infiltrate the Genworth servers
On May 31st, 2023, the Genworth Financial data breach came to light – an entire 2.5 million customers and policy holders had been affected.
The cause of the data breach was a Genworth Financial vendor, PBI Research Services, who had been infiltrated by the threat actors. Through supply-chain principles, this opened the way to the Genworth Financial systems.
The data affected include names, policy numbers, customer names, and Social Security numbers. Genworth posted a notice on its website, saying that affected individuals will receive a notification letter either from them or from PBI.
According to a press release from August 24th, 2023, if you were a victim of this data breach, you may be entitled to compensation for the damages incurred.
25. Shields Health Care Group

https://shields.com/
- When: March 2023
- What: 2.3 million records leaked, including dates of birth, social security numbers, home addresses, healthcare data, billing information, and other financial details
- How: Unclear how the threat actors gained access to the firm’s systems
In April 2023, Shields Health Care Group, a Massachusetts medical service provider, reported a data breach that had taken place a month prior.
The threat actors had managed to steal the patient records of over 2.3 million people including their names, dates of birth, SSNs, home address, and healthcare and financial data.
After investigating the event, the company reported they don’t know how the hackers gained access to their systems but that they “take the confidentiality, privacy, and security of information in our care seriously.”
They also mentioned that “Upon discovery, we took steps to secure our systems, including rebuilding certain systems, and conducted a thorough investigation to confirm the nature and scope of the activity and to determine who may be affected.”
According to the HIPPA Journal, a team of forensic investigators could not determine how the attack took place but that 2.3 million patients had been affected. The company also took immediate action in rebuilding its security systems and implementing new ones.
26. Undisclosed Restaurant Database

- When: September 2023
- What: 2.2 million data records of Pakistani citizens, including credit card details and contact numbers, have been leaked
- How: Believed to be part of a 2022 data leak that was reposted on a dark web forum on September 16th, 2023.
In September 2023, a post appeared on a dark web forum with an alleged data dump belonging to several Pakistani restaurants. The data dump allegedly contained over 2.2 million users from Indolj, a popular food ordering app. The hacker demanded a payment of 2 Bitcoins to not publish the data.
However, Indolj officially stated that the data breach could not have originated from them since they do not store transactional records or other payment-related information about their customers.
The security company CTM360 confirmed this fact and said that the data breach likely originates from an older leak in 2022.
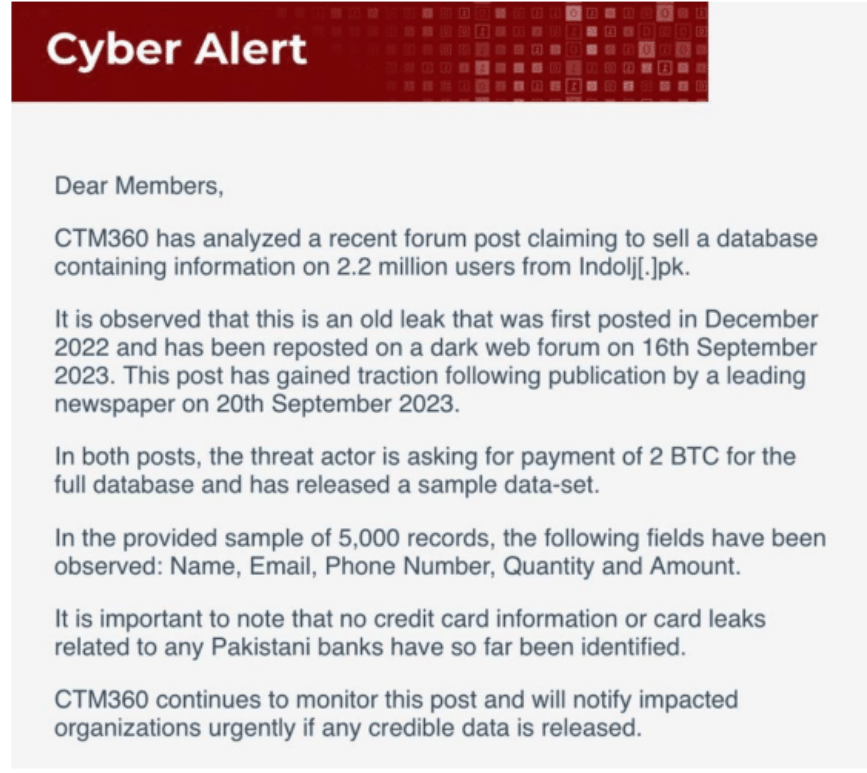
https://propakistani.pk/2023/09/22/restaurant-app-indolj-denies-data-breach-after-hackers-share-allegedly-stolen-but-old-data/
They claim that some of the data stolen involved names, phone numbers, emails, quantity, and amount. They also did not identify any card leaks or credit card information related to any Pakistani banks data breaches.
Moreover, the hacker posted a sample of 5,000 records where they named the victims and offered other private information to prove their claims.
It’s currently unknown whether someone has paid this ransom, though it’s highly unlikely. We also don’t know if the database was made public.
27. Wilton Reassurance

https://dxc.com/us/en/insights/customer-stories/wilton-re-takes-on-insurance-risk-profitably
- When: June 2023
- What: 1.4 million insurance records of New Yorkers leaked online
- How: Part of the MOVEit data breach; PBI Research Services was a vendor of Wilton RE, so the hacker used a supply-chain attack to reach the target
In June 2023, Wilton Reassurance discovered that it, too, had become a victim of the MOVEit data breach. The New York-based insurance provider had suffered a data breach of over 1.4 million records.
PBI Research Services had been hacked, and because it was a vendor of Wilton Reassurance, the hackers managed to go up the supply chain and infiltrate its systems.
The leaked data included names and social security numbers, so the potential of targeted phishing attacks is quite high.
Wilton Reassurance is offering 24 months of free identity restoration services and credit monitoring for all affected individuals in an attempt to help everyone involved.
At this point in time, we don’t know whether the data leaked from Wilton Reassurance is up for sale on the dark web or if the hackers have demanded a ransom.
What we do know, however, is that PBI has since patched the vulnerability and closed off access to any malicious actors looking to steal more data.
So, any companies still using PBI are safe.
28. NCB Management

https://www.linkedin.com/company/ncb-management-services-inc./
- When: February 1st, 2023
- What: 1 million financial records stolen
- How: Unclear how the data breach occurred
NCB Management, a debt collection company, has suffered a data breach in February 2023. A threat actor had accessed the credit card data of 1 million Bank of America past-due accounts.
They were able to access a lot of data, including:
- First and last names
- Physical addresses
- Phone numbers
- Email addresses
- Dates of birth
- Employment positions
- Payment amounts
- Social Security numbers
- Driver’s license numbers
- Credit card numbers
- Routing numbers
- Account numbers
- Account balance
- Account status
The large amount and specific nature of the leaked financial information is particularly worrisome, as it opens the potential for many scam attempts that use social engineering principles.
The company also penned a notification letter to its clients that read “Recently, confidential client account information maintained by NCB was accessed by an unauthorized party. To date, we are unaware of any misuse of your information as a result of this incident.”
They also mentioned the fact that they “obtained assurances that the unauthorized third party no longer has access to any of NCB’s data,” which could mean that the company opted to pay the ransom (unknown value).
29. CentraState Medical Center

https://www.centrastatejobs.com/
- When: February 2023
- What: 617,000 sensitive patient records stolen
- How: Ransomware attack that involved a compromised personal data cache
CentraState Medical Center discovered the data breach in December 2022 but came out publicly with it in February 2023 after they’d finished the forensic investigation.
Apparently, a ransomware attack had stolen a cache of personal data containing the medical data of 617,000 patients. The data included names, addresses, dates of birth, Social Security numbers, health insurance information, patient account numbers, and medical record numbers.
According to the HIPAA journal, CentraState Medical Center is facing a class-action lawsuit over the ransomware data leak on account of their lack of robust security methods that would have protected the personal data.
The company did send notifications to all affected patients a few days after they became aware of the data breach. They also offered free identity theft protection and credit monitoring to all affected clients.
The lawsuit aims to obtain monetary compensation for the privacy violation, reimbursement for out-of-pocket expenses associated with identity protection measures, and injunctive relief.
30. Kodi

https://kodi.tv/
- When: April 2023
- What: 400,636 user records were leaked, including personal data
- How: An unauthorized party had compromised the MyBB forum database and stole the personal data, though the Kodi servers have not been breached
In April 2023, Kodi learned that someone had breached the MyBB forum database and stolen profiles on Kodi users. These profiles contained usernames, email addresses, and encrypted passwords. There were also direct messages, public forum posts, and team forum posts included.
Kodi publicly stated that “MyBB admin logs show the account of a trusted but currently inactive member of the forum admin team was used to access the web-based MyBB admin console twice: on 16 February and again on 21 February.”
This can mean two things – either that admin team member has gone rogue or someone has used their device to access the MyBB database.
Kodi did mention that the servers hosting the MyBB software have not been infiltrated or compromised, so the vulnerability was easily patched and there are no more risks.
The threat actor responsible for the data breach also tried to sell the data dump on BreachForums but they did not succeed since the site was taken down.
Kodi did mention that they would begin a full-scale global password reset just to make sure that its users would not be in any danger.
31. GoAnywhere

https://www.prnewswire.com/news-releases/goanywhere-managed-file-transfer-50-released-with-unified-interface-and-advanced-reporting-300116042.html
- When: March 2023
- What: Unknown number of leaked records but estimated to be a few million (over 130 organizations targeted)
- How: Zero-day vulnerability used to access the servers and the Clop ransomware gang is suspected
In March 2023, the GoAnywhere file transfer service has suffered a data breach due to a zero-day vulnerability, similar to MOVEit. And just like it, it has enabled attacks against hundreds of organizations (130 so far) because of the leaked data.
Some of the known targeted companies are Hatch Bank, Rubrik, Hitachi Energy, and the City of Toronto. In all of these cases, the victims reported that the GoAnywhere MFT remote code execution vulnerability has been used in the data breach.
So far, we don’t know specifics about the number of records lost for individual companies that have used GoAnywhere services but we should be seeing new attacks in the coming months.
Some of the victims were contacted by the CL0p ransomware gang who asked for a ransom in exchange for the stolen data.
A City of Toronto official has official said that “The access is limited to files that were unable to be processed through the third-party secure file transfer system. The City is actively investigating the details of the identified files“.
So, some of the victims are not even ware as to the nature of the data that was leaked through the GoAnywhere breach.
To Wrap Up...
The biggest data breach this year has been DarkBeam, with 3.8 billion leaked records. That’s almost 71% of all the compromised records of 2023 from just one single data breach.
With over 953 cybersecurity incidents in 2023 and over 5 billion breached records, 2023 is definitely not a good year for businesses around the world.
Cybercrime-as-a-service is getting more infamous, new malware variants are being developed, and social engineering is becoming increasingly sophisticated.
Cybersecurity needs to step up its game and consumers need to increase their cyber-awareness. Fortunately, PrivacyAffairs is here to help you with handy cybersecurity guides and studies.
Stay safe and always protect yourself online!
Sources
Statista – Most Concerning Consequences of Cyber Incidents According to Board Members Worldwide as of June 2023
Statista – Most Important Consequences of Cyber Attacks Worldwide as of February 2023
Cybernews – DarkBeam Leaks Billions of Email and Password Combinations
The Hindu – U.S. Cyber Security Firm Indicates Data Breach Sourced from ICMR
Reuters – Twitter Hacked, 200 Million user Email Addresses Leaked, Researcher Says
Nist.Gov – CVE-2023-34362 Detail
Emsisoft – Unpacking the MOVEit Breach: Statistics and Analysis
Twitter – Andrea Draghetti Luxottica Report
Electoral Commission – Electoral Commission Subject to Cyber-Attack
SEC.Gov – T-Mobile Data Breach Report
CPO Magazine – 34 Million Indonesian Passports Exposed in a Massive Immigration Directorate Data Breach
Cyberscoop – DNA Testing Service 23andMe Investigating Theft of User Data
Bleeping Computer – TruthFinder, Instant Checkmate Confirm Data Breach Affecting 20M Customers
Latitude Financial – Latitude Cyber Response
Website Planet – Millions of Highly Sensitive Patient Records Exposed in Medical Diagnostic Company Data Breach
The Guardian – JD Sports Hit by Cyber-Attack that Leaked 10m Customers’ Data
Pole Emploi – A Pôle emploi Provider Victim of Cyber-Malware Act
Bleeping Computer – AT&T Alerts 9 Million Customers of Data Breach After Vendor Hack
Maine Gov – MCNA Data Breach Notification
Security Week – University of Minnesotta Confirms Data Breach, Says Ransomware Not Involved
Cybernews – Russian e-Commerce Giant Exposed Buyers’ Delivery Addresses
Express Lane – Louisiana Office of Motor Vehicles Addresses a Data Security Incident
HIPAA Journal – Almost 6 Million Individuals Affected by PharMerica Data Breach
Born Incident – MOVEit Cybersecurity Incident
Bloomberg Law – TIAA Sued Over MOVEit Data Breach of 2.4 Million Consumers (1)
Dark Reading – Genworth Financial Under Investigation for Data Breach
Shields – Notice of Data Security Incident
HIPAA Journal – 2 Million Patients Affected by Shields Health Care Group Cyberattack
Pro Pakistani – Restaurant App Indolj Denies Data Breach After Hackers Share Allegedly Stolen but Old Data
JD Supra – Wilton Reassurance Announces Data Breach Related to MOVEit Software Vulnerability
Cybernews – US Debt Collector Breach Exposed 1M+ People
HIPAA Journal – CentraState Medical Center Facing Class Action Lawsuit Over December 2022 Ransomware Attack
The Hacker News – Kodi Confirms Data Breach: 400K User Records and Private Messages Stolen
Security Week – GoAnywhere MFT Users Warned of Zero-Day Exploit
Privacy Affairs – Cybersecurity Deep Dive: What Is Cybercrime-as-a-Service?
Privacy Affairs – The Art of Cyber Deception: Social Engineering in Cybersecurity

