Cybersecurity Deep Dive: Everything About DDoS Attacks
A Distributed-Denial-of-Service attack, DDoS for short, is a type of cyberattack that has one goal – to disrupt a company’s infrastructure and interrupt its activities.
It achieves this by sending an overwhelming amount of traffic to its servers, network, or services.
If the servers are not equipped to handle that much traffic simultaneously, they will crash, freezing the company’s systems for as long as the DDoS attack continues.
In the following paragraphs, I’ll explain how DDoS attacks work, their impact, and how to defend against them, actively and proactively.
Let’s get started!
How Does a DDoS Attack Work?
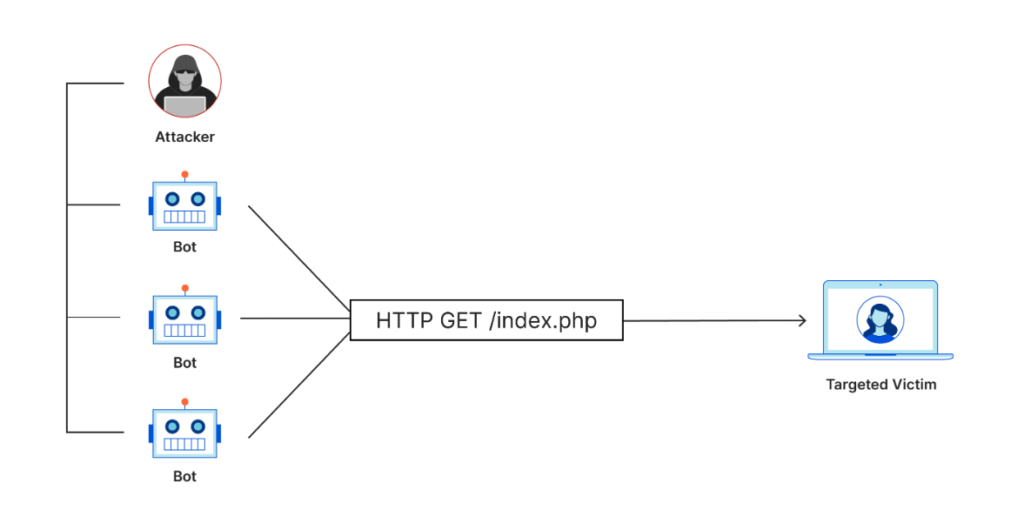
DDoS attacks use “botnets” to send multiple simultaneous requests to the target company’s servers in an attempt to overwhelm it.
A botnet is essentially a network of “zombie” devices (computers, mobile devices, laptops, etc.) controlled by the “botmaster” (hacker) after infecting them with malware.
These individual infected devices are called “bots” and the botmaster can easily control them from a distance.
After the botmaster infects enough devices to launch a DDoS attack, he sends specific instructions to each device, and the attack can begin.
Here’s how it all happens:
- Hacker infiltrates 2,000 devices of random individuals who aren’t aware of it
- Hacker creates a botnet out of those 2,000 devices by installing a controlling malware in each one
- Hacker selects a target to attack
- Hacker sends specific instructions to every device in the botnet to access the company’s IP address simultaneously
- The target’s servers receive 2,000 simultaneous requests and crash due to not being able to handle so many requests at once
An infamous DDoS attack was launched against Dyn in October 2016. Dyn controlled most of the internet’s DNS infrastructure, so the attack brought down sites like Netflix, Twitter, Reddit, CNN, and others around Europe and the US.
The botnet responsible for the Dyn attack was believed to consist of approximately 100,000 compromised IoT (Internet of Things) devices, including digital cameras and DVR players.
At its peak, the botnet unleashed a staggering 1.2 terabits per second (Tbps) of traffic—making it nearly twice as powerful as any distributed denial-of-service (DDoS) attack recorded up to that point.
Types of DDoS Attacks
There are three types of DDoS attacks:
- Application Layer Attacks
- Protocol Attacks
- Volumetric Attacks
All three types of DDoS attacks will disrupt and overwhelm the target’s servers but the means to achieve that are different.
Moreover, all DDoS attacks will manipulate the network connectivity in some capacity. To help you understand how network connections work, here’s a helpful OSI Model.
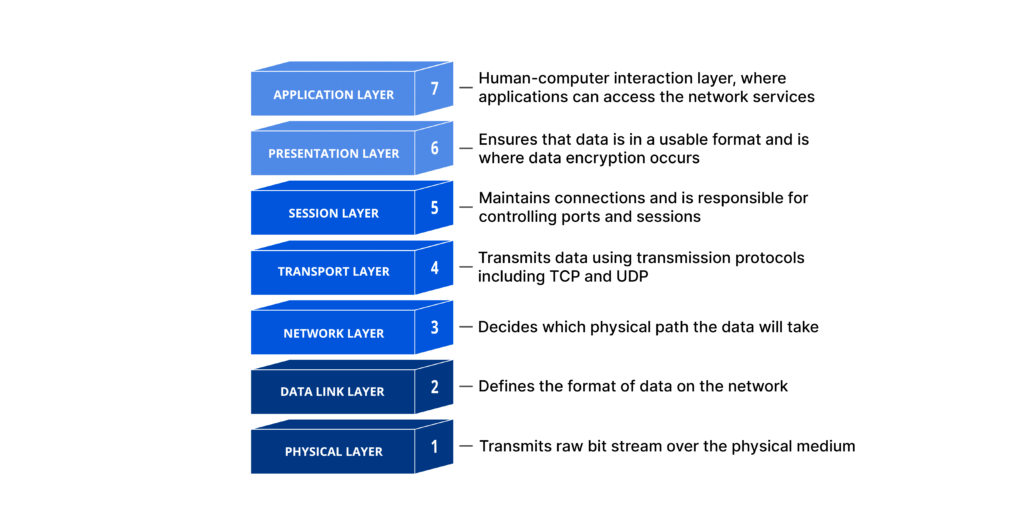
https://www.cloudflare.com/learning/ddos/glossary/open-systems-interconnection-model-osi/
So, a network connection has seven layers, and DDoS attacks manipulate some of these layers to overwhelm the servers.
Let’s take a look at the three DDoS attack types in more detail!
1. Application Layer Attacks
https://www.cloudflare.com/learning/ddos/what-is-a-ddos-attack/
Application Layer DDoS attacks are also known as Layer 7 attacks because they manipulate the 7th layer in the OSI Model above (the Application Layer).
The goal of an Application Layer DDoS attack is to exhaust a server’s resources so that it ultimately crashes due to insufficient resources.
This is why the Application Layer attack’s strength is measured in RPS or requests-per-second.
The target of this attack is the HTTP side of a server, more precisely the web pages that the server generates and delivers as a response to HTTP requests sent by the client.
The simple act of loading a web page seems simple for the client but it’s a complex process for the server. That’s because it has to load multiple files, access databases, run queries, and then create the webpage.
Examples of Application Layer attacks:
- Instructing the botnet to open the same webpage simultaneously, making multiple HTTP requests to the server
- Instructing the botnet to refresh the same webpage simultaneously multiple times
With so many HTTP requests to load a webpage, the server’s computational capacity may be overwhelmed. It doesn’t have the necessary resources to satisfy all the HTTP requests at once, so it crashes.
This is how a denial-of-service attack works via an Application Layer DDoS attack!
2. Protocol Attacks
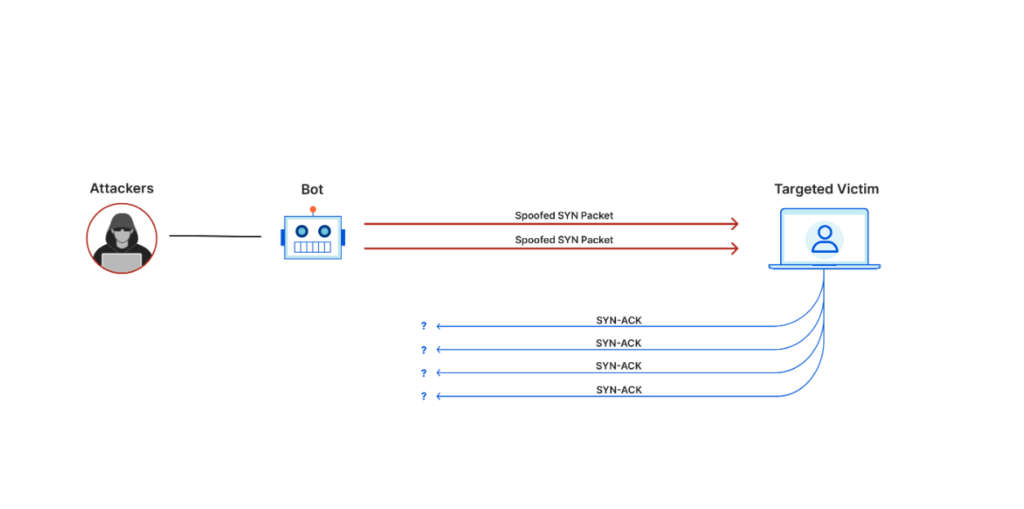
cloudflare.com/learning/ddos/what-is-a-ddos-attack/
Protocol DDoS attacks manipulate the 3rd and 4th layers of the OSI network model above (the Network and the Transport Layers).
These attacks are measured in packets-per-second and will target specific resources like load balancers, firewalls, routers, and other resources.
However, the idea behind Protocol Attacks is a bit different compared to Application Layer attacks.
While Application Layer attacks relies on overwhelming HTTP requests to crash the server, Protocol Attacks exploits the TCP handshake involved in a protocol-type exchange of information.
The TCP handshake relies on three steps:
- SYN Packet sent by the client to the server or resource
- SYN-ACK packet sent by the server/resource to the client
- ACK packet sent back by the client to the serve/resource
In a Protocol Attack, the third step is missing. The victim server/resource doesn’t receive the ACK packet from the client (hacker botnet), so it can’t complete the data transfer.
The client sends multiple TCP SYN packets using spoofed IP addresses to the server/resource. The server will respond to the connection requests and will wait for the ACK packet to complete the handshake, but it never arrives.
So, more and more unanswered connection requests are piling up, which exhaust the resources of the target server/requests.
3. Volumetric Attacks
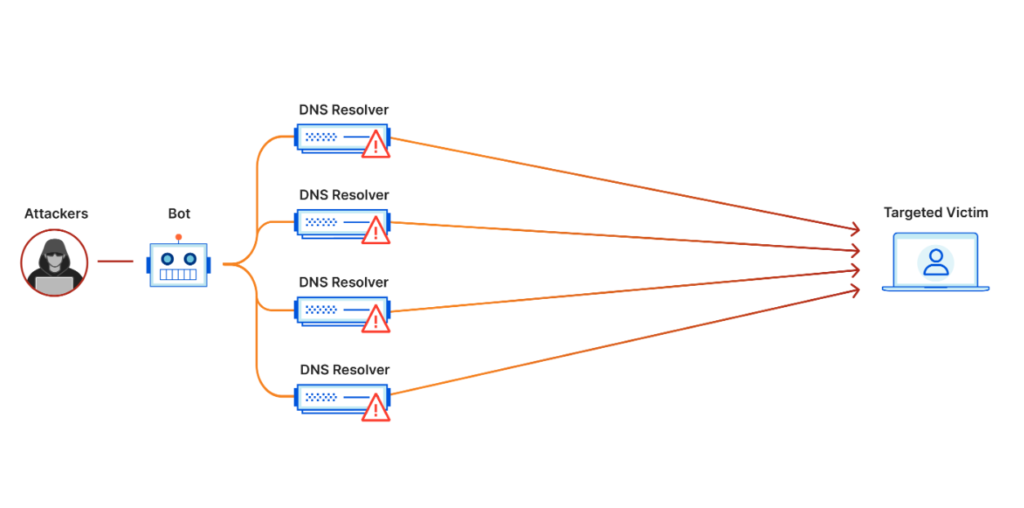
https://www.cloudflare.com/learning/ddos/what-is-a-ddos-attack/
The Volumetric Attack is the most common form of DDoS attack and it’s also what most people refer to (unconsciously) when talking about DDoS attacks.
Its attack strength is measured in bits per second or gigabits per second (see the Dyn attack), and its goal is to overwhelm a server with traffic and requests.
This brute-force approach needs a large-enough botnet to exhaust all the server’s bandwidth.
Alternatively, hackers can use DNS amplification to achieve the same result easier. Here’s how:
- The hacker sends several small DNS requests using the victim’s spoofed source IP address to a DNS server
- The DNS server responds to the victim with a much larger DNS response than the attacker sent
- The victim’s servers are eventually overwhelmed from the amount of traffic received
So, either through botnet requests or DNS amplification, the Volumetric Attack is meant to overwhelm the server with requests.
The difference between a Volumetric Attack and Application Layer Attack is that the latter is more complex and requires more specific actions to pull off.
Ways to Spot a DDoS Attack

It’s impossible to know when a DDoS attack will be launched. However, there are red flags you can identify when the attack is underway.
Detecting a DDoS attack at an early stage can help you mitigate it faster, avoiding the brunt of the assault and the denial-of-service.
Here are several ways you can identify a DDoS attack:
- A sudden increase in web traffic coming from a single location or IP address
Most DDoS attacks rely on botnets, which are infected devices that are usually located within the same area.
Once the botmaster instructs the botnet to begin a DDoS attack, all the devices will start sending constant requests to your servers.
These will appear as a spike in your traffic coming from the same devices and area.
- Slow loading time on your website
If you’re noticing unexplainable slowness on your website, then it might be because your servers are flooded with requests.
Once the system is overloaded, it’ll slow down, leading to slower loading times. This is often the first red flag that people notice during a DDoS attack.
- The server responds with a 503 error
When a DDoS attack increases your server traffic, the server will often respond with a 503 unavailable error because it can’t handle that many requests.
Usually, this error will disappear once the traffic volume goes down but if it doesn’t, then you’re likely dealing with a DDoS attack.
During a DDoS attack, the traffic volume never subsides until the hacker decides to stop the attack.
- Decreased site and service performance on the same network
DDoS attacks will target a server’s internet network, so any device/service using that network will perform slower.
That’s because the network bandwidth is limited, and the DDoS attack consumes all the available bandwidth.
Any service using the network will either slow down or crash. Often, these subsidiary services show the first red flags because they’re more vulnerable than your servers.
- Increased memory or CPU usage on your server
DDoS attacks target a server’s resources by increasing its CPU and memory usage to the brink of collapse.
Watch out for any surges in CPU or memory surges. If they’re sudden and unexplainable, then it might be a DDoS attack during its initial phase.
- Traffic source addresses will request the same data set after the request timeout
When a client requests a set of data over a DNS server, the server needs to provide that data within a given timeframe.
During a DDoS attack, the server is so overwhelmed with requests that it can’t deliver those data sets within the allocated time. This is when a request timeout occurs.
If the client receives a request timeout, it won’t request the same data for some time believing that the server is down.
However, if you notice that the same traffic source addresses are requesting the same data sets despite the request timeout, that’s a red flag.
Authentic traffic doesn’t behave like this. Once it receives a request timeout, it won’t send anymore requests for some time.
- A sudden spike of traffic to a single page or service
When launching a DDoS attack, hackers will often focus on a few pages or services and direct the botnet on those pages.
So, if you notice a sudden and uncommon increase in the traffic coming to a page or service, it should raise a red flag.
Common Targets of DDoS Attacks & Motivations
While it’s true that any online business is a potential target of a DDoS attack, hacker usually focus on a few key industries and market segments.
First, let me tell you about the most common motivations of DDoS attacks:
- Ideological Reasons – hacktivism is not a new phenomenon, and it refers to hackers who attack targets who disagree with their ideology
- Extortion – This is the most common reason for a DDoS attack, to steal money from a target, or steal valuable data that you can then sell for a profit on the Dark Web
- Business Conflict – Many businesses engage in strategic DDoS attacks against their competitors to crash their websites and gain an advantage
- Cyber Warfare – DDoS attacks are even used by world governments against enemy countries to cripple their infrastructure and weaken them
- Boredom – Cyber-thugs, as I like to call them, send random DDoS attacks to random targets without a greater goal in mind. They’re just bored and want the adrenaline rush
- Demonstrations – Cyber-criminals will often launch DDoS attacks to prove the effectiveness of their scripts to incentivize buyers to purchase their services
- Revenge – Seeking revenge on a political opponent, a government, or a company is very common, and it’s often done through DDoS attacks. Disgruntled employees often resort to this attack pattern when they have a dispute with their employee and they’re fired
- Preparation for a Bigger Attack – Many hackers use DDoS attacks as a precursor to other, more sophisticated or insidious attacks. The goal is to weaken the target’s network and then infiltrate it with a parallel attack
In recent years, there’s been an increase in DDoS attacks that are short and high-intensity, pointing to the idea that hackers are becoming more efficient and specific with their targets.
Now that we know about the motivations behind DDoS attacks, let’s look at the most common targets as of 2023:
1. Software and Technology Sector
According to a survey by AtlasVPN in June 2021, 65% of all organizations targeted by DDoS attacks were in the US and the UK, and 83% of them were in the Internet and Computer sectors.
SaaS, cloud-based technology companies, and other tech-based organizations are the most common targets of DDoS attacks around the world.
DNS and NTP reflection and amplification attacks were the most used attack vectors, with 33% and 26% usage, while SYN floods and UDP floods accounted for 22% and 27% of attacks.
The reason why the technology sector is the preferred target of DDoS attacks is the interconnectedness of the industry.
Tech companies include hosting providers, internet service providers, SaaS, and cloud-based companies used by a multitude of other companies and services.
Attacking the service providers will automatically affect the downstream customers too, in a chain reaction of increasing proportions.
2. Financial Sector
The Financial sector is the second-most targeted industry by DDoS attacks around the world. The reason for this is simple – money.
Banks, loaning agencies, credit companies, and all money-related organizations are prime targets for hackers because of the potential profits involved.
Often, DDoS attacks against financial companies are followed by other attacks like ransomware, malware, or phishing attacks.
Cryptocurrency platforms have seen a massive surge in DDOS attacks of 600%, with a 15% increase in the HHTP DDoS attacks.
There’s also been an increase in the complexity of DDoS attacks launched against crypto companies, likely because of the increasing cybersecurity measures they use.
3. Information Services Sector
The Information sector includes any companies or organizations that aggregate information in some way or another.
These companies either produce or process information. And information is valuable on the Dark Web, as we know too well.
It’s no surprise that this sector is the third most targeted by DDoS attacks in the world. Once they get their hands on IP or other personal data, hackers can sell it for a profit without being tracked by the authorities.
Moreover, the amount of information in the world is constantly growing because more people are using the internet, more technologies are created, and there are more ways to use the internet.
Naturally, hackers will redouble their focus on this industry for the foreseeable future.
4. Gaming Sector
Akamai Technologies, which is the most reputable cybersecurity and cloud computing company in the world, reported in 2022 that DDoS attacks against the Gaming industry have doubled in the last year.
The report claims that the Gaming industry is the target of 37% of all DDoS attacks. This is likely caused by the shift to cloud gaming, which creates new attack vectors for attackers.
Microtransactions have also become more popular, which is a very attractive attack target for hackers.
Jonathan Singer, Akamai’s Senior Strategist, reported that “As gaming activity has increased and evolved, so has the value of disrupting it through cyber attacks. Also, with the industry’s expansion into cloud gaming, new threat surfaces have opened up for attackers by bringing in new players who are prime targets for bad actors.”
The gaming industry is also populated with younger audiences who are less aware of cybersecurity risks and are easily manipulated.
How Do DDoS Attackers Hide Themselves?

To ensure that their attacks are effective as possible, hackers will try to avoid detection and hide their traces when launching a DDoS attack.
Here’s how they do it:
1. Spoofing
According to Forcepoint, “Spoofing is the act of disguising a communication from an unknown source as being from a known, trusted source”.
DDoS hackers will spoof the source and destination addresses though IPv4 networks, which are more vulnerable than IPv6.
The bad actors will forge packets with fictitious source addresses, letting them manipulate legitimate devices into replying to these packets in good faith.
Hackers will send millions of replies to the victim host even though the host device never requested these replies.
That’s because the replies look legitimate through the spoofed source and destination addresses.
That’s the gist of it.
2. Reflection
DDoS attackers will use multiple servers (DNS, NTP, or SNMP) to hide their identities from the victim.
Internet services like the Domain Name System and Simple Network Management made it difficult for victims to identify the origin of the attack or the identities of the attackers.
That’s because these servers don’t keep logs on the services that people are using on these servers.
This no-log policy is generally a good thing, since you don’t want anyone to keep track of your online activities.
But this also means that hackers have more leeway in the scale of attacks they conduct due to how easy it is to remain anonymous
3. Amplification
I’ve mentioned amplification before as the driving factor behind Volumetric Attacks. What I didn’t say is that amplification is also good at hiding the attacker’s traces.
The hacker doesn’t send a packet directly to the victim but rather “convinces” a legitimate service into sending hundreds and thousands of replies to the victim network/server.
It’s an indirect attack method that keeps the hacker anonymous at all times.
How Long Do DDoS Attacks Last?

According to a SecureList report in 2019, 81.86% of all DDoS attacks lasted less than 4 hours.
It’s very uncommon for a DDoS attack to last more than a few hours but there have been cases of attacks lasting several days.
The largest-ever DDoS attack recorded lasted 509 hours (almost 21 days), and it happened in 2019, as reported by Kaspersky.
Let me show you the distribution of DDoS attacks by duration in Q3 and Q4 2019, from a SecureList study:
| Duration | Percentage of DDoS Attacks |
| Less or Equal to 4 Hours | 84.42% in Q3 2019 81.86% in Q4 2019 |
| Between 5-9 Hours | 8.22% in Q3 2019 10.19% in Q4 2019% |
| Between 10-19 hours | 4.13% in Q3 2019 5.33% in Q4 2019 |
| Between 20-49 hours | 2.19% in Q3 2019 2.05% in Q4 2019 |
| Between 50-99 hours | 0.8% in Q3 2019 0.36% in Q4 2019 |
| Between 100-139 Between | 0.12% in Q3 2019 0.14% in Q4 2019 |
| Equal or More than 140 Hours | 0.12% in Q3 2019 0.08% in Q4 2019 |
There seems to be an increase in the duration of DDoS attacks from Q3 to Q4 2019. The number of DDoS attacks with a duration of less or equal to 4 hours has dropped by around 3%.
DDoS attacks with higher durations have increased. The same report mentions that in Q4 2019, there were three DDoS attacks that lasted for more than 20 days, while in Q3 2019, not even an attack lasted more than 12 hours.
Here’s the same report for Q2-Q3 2022:
| Duration | Percentage of DDoS Attacks |
| Less or Equal to 4 Hours | 95.42% in Q2 2022 94.29% in Q3 2012 |
| Between 5-9 Hours | 3.36% in Q2 2022 3.16% in Q3 2012 |
| Between 10-19 hours | 0.92% in Q2 2022 1.60% in Q3 2012 |
| Between 20-49 hours | 0.24% in Q2 2022 0.75% in Q3 2012 |
| Between 50-99 hours | 0.05% in Q2 2022 0.14% in Q3 2012 |
| Between 100-139 Between | 0% in Q2 2022 0.14% in Q3 2012 |
| Equal or More than 140 Hours | 0.01% in Q2 2022 0.01% in Q3 2012 |
It seems that in 2022, DDoS attacks have decreased in duration, with almost 95% of them being less than four hours in Q3 2022.
Less than 0.01% of all DDoS attacks in 2022 are equal to or more than 140 hours, and it’s almost the same story for DDoS attacks lasting 100-139 hours.
However, this isn’t necessarily good news. While the duration of DDoS attacks has decreased, their number has increased.
Geography of DDoS Attacks
DDoS attacks aren’t random, geographically speaking. They target certain countries because that’s where the biggest profits lie.
Let’s look at which countries have been most targeted by DDoS attacks in Q2 2022 and Q3 2022:
| Country | Percentage of DDoS Attacks |
| United States | 45.95% in Q2 2022 39.60% in Q3 2012 |
| Mainland China | 7.67% in Q2 2022 13.98% in Q3 2012 |
| Germany | 6.47% in Q2 2022 5.07% in Q3 2012 |
| France | 4.60% in Q2 2022 4.81% in Q3 2012 |
| Hong Kong | 1.75% in Q2 2022 4.62% in Q3 2012 |
| Brazil | 3.20% in Q2 2022 4.19% in Q3 2012 |
| Canada | 3.57% in Q2 2022 4.10% in Q3 2012 |
| Great Britain | 3.51% in Q2 2022 3.02% in Q3 2012 |
| Singapore | 2.90% in Q2 2022 2.13% in Q3 2012 |
| Netherlands | 2.91% in Q2 2022 2.06% in Q3 2012 |
| Other | 17.47% in Q2 2012 16.42 in Q3 2022 |
Most DDoS attacks are targeting the US (39.60% in Q3 2022), but there’s been a 6% decrease in attacks against the US between Q2-Q3 2022.
Instead, attacks against Mainland China have almost doubled, signifying a shift in the interests of threat actors, maybe.
Now, let me show you the distribution of unique DDoS targets by country in Q2 – Q3 2022:
| Country | Percentage of Unique DDoS Attacks |
| United States | 45.25% in Q2 2022 39.61% in Q3 2012 |
| Mainland China | 7.91% in Q2 2022 12.41% in Q3 2012 |
| Germany | 6.64% in Q2 2022 5.28% in Q3 2012 |
| France | 4.42% in Q2 2022 4.79% in Q3 2012 |
| Hong Kong | 2.01% in Q2 2022 4.36% in Q3 2012 |
| Canada | 2.97% in Q2 2022 3.21% in Q3 2012 |
| Great Britain | 3.77% in Q2 2022 2.96% in Q3 2012 |
| Singapore | 3.22% in Q2 2022 2.11% in Q3 2012 |
| Poland | 1.37% in Q2 2022 2% in Q3 2012 |
| Other | 21.26% in Q2 2022 18.90% in Q3 2012 |
The US is still at the top of the list in terms of unique DDoS targets but the stats show a positive outlook between Q2 and Q3 2022.
China shows the same substantial increase in unique targets as it did in total attacks, which makes for an important distinction.
More Chinese-based businesses have been hit by DDoS attacks instead of more DDoS attacks being directed against the same targets.
DDoS vs. DoS Attacks – Important Distinctions

DDoS and DoS attacks are not the same. While the end-goal remains the same – flooding the victim’s server with traffic to overload it – the methods used are different.
While DDoS attacks rely on multiple computers flooding a single target resource, DoS attacks are one-on-one, meaning that a single system attacks another system.
Essentially, DDoS attacks are many-on-one, while DoS attacks are one-on-one.
There are other key differences between the two, though:
- Ease of detection and mitigation – DoS attacks are easier to detect and protect against because they come from a single source. DDoS attacks are distributed among multiple sources, making them harder to detect or mitigate
- Speed of Attack – DoS attacks are slower than DDoS attacks because it’s faster to launch an attack from multiple sources. The higher attack speed makes detection and mitigation more difficult, as well
- Traffic Volume – DDoS attacks can send much more traffic to the victim server because they employ multiple devices to send traffic simultaneously. DoS attacks use one machine that can send limited traffic, making these attacks less effective
- Scale of Damage Inflicted – The more traffic sent at once, the more effective a DDoS attack is. And since DDoS attacks send more traffic, this makes them more destructive and harder to mitigate than DoS attacks
- Method of Execution – DoS attacks use a script or tool to launch the attack from a single device. DDoS attacks will coordinate several bots (infected devices), creating a botnet that the hacker controls via a command-and-control center. DDoS attacks are thus more intricate to carry out
- Ease of Attack Source Tracing – DDoS attacks are much harder to track because of the botnet (multiple devices) used in the attack. DoS attacks use a single device, which makes them much easier to track
It’s quite clear that DDoS attacks are the stronger, more dangerous form of DoS attacks. They require more resources and more technical knowledge, but they have superior attack capabilities.
Impact of DDoS Attacks

DDoS attacks can have a significant impact on the productivity and performance of a company in many ways, including:
- Loss of Revenue
When a company is hit by a DDoS attack, there’s going to be downtime, employees won’t be able to access certain services, and production will halt to a stop.
A period of total downtime can mean tens of thousands of dollars lost for companies in the Finance sector, for instance, but any company offering an online service will lose revenue, essetially.
According to a Statista report published in 2019, 25% global enterprises were losing $301,000 – $400,000 per hour of downtime in 2020.
And 17% of all enterprises were losing more than $5 million per hour of downtime, which is a mind-boggling sum.
- Loss of Productivity
Even if production doesn’t come to a complete halt during a DDoS attack, productivity will still be negatively impacted.
If certain applications or services become inaccessible, employees won’t be able to work efficiently, so there will still be a degree of downtime.
Business owners might want to consider the cost-per-hour of employee downtime in case a DDoS attack does occur.
- Damage Remediation Costs
When a DDoS attack hits, it almost always causes damage to systems, services, and it affects performance. System recovery, labor costs, overtime costs, hiring outside consultants to assess the DDoS damage, these are all damage remediation costs.
The aftermath of a DDoS attack can, in fact, impact more than the IT department and systems. It can affect public relations, customer support teams to respond to customer complaints, and other correlated systems.
- Reputational Damage
Many companies and industries (Health, Hosting, Finance, etc.) will suffer reputation damage when struck by a DDoS attack. The public will lose trust in the company’s ability to safeguard their personal data and provide consistent quality services.
Such services must be available consistently, or else customers will leave bad reviews and spread the word on social media, harming the company’s reputation.
DDoS attacks create a period of downtime of a few hours up to a few days, if the attack is particularly severe. If this happens often enough, it’ll leave the company’s reputation in tatters.
- Market Share Damage
Public companies also have to preserve their market share to remain attractive to investors and keep shareholders appeased. Constant downtime due to DDoS attacks will undoubtedly harm that market share.
- Potential Ransom Costs
While ransomware is different from DDoS, hackers have begun combining both attacks in recent years.
They first launch a DDoS attack and demand a ransom in exchange for stopping the DDoS assault and restoring functionality to the company.
Or they first send a ransom demand and threaten that they’ll launch a DDoS attack if they don’t get paid.
DDoS attacks can be very destructive, depending on the target victim’s security system, industry, sophistication of the attack, and other factors.
From losses in productivity to drops in market share and massive reputation damage, companies hit by DDoS attacks have a lot of remediation to do to recover.
Cyber-insurance would help mitigate most of these issues by covering the majority of these costs. It’s certainly worth looking into for companies operating in high-risk industries.
How to Prevent a DDoS Attack in 6 Steps

While DDoS attacks come unexpectedly, there are ways to protect yourself against them before they hit.
Let me give you a summary of these 6 prevention methods:
1. Reduce the Attack Surface Area
DDoS attacks are more devastating the more attack surface there is. So, limiting the attack surface will mitigate most of the impact of a DDoS assault on your servers. It also allows you to implement security safeguards more efficiently because of the network segmentation.
You should minimize the potential points of attack by not exposing your resources to unknown or outdated applications, protocols, or ports.
You should also use Load Balancers, Content Distribution Networks, and Access Control Lists (or firewalls) to control the traffic that reaches your server and applications.
2. Get Network Redundancy
DDoS attacks work by overloading your network capacity through large volumes of traffic. Consequently, if you have a lot of unused and redundant Internet connectivity, DDoS attacks won’t work.
Increasing the bandwidth (transit) capacity and the server capacity will improve your chances of avoiding a DDoS attack substantially.
Your hosting provider manages your bandwidth capacity, so talk to them and demand more redundant internet connectivity.
As for server capacity, you should use enhanced networking and extensive network interfaces that allow for larger volumes of resources to be used at once.
Load balancers (mentioned above) are another great solution to monitor and shift the resource loads seamlessly to avoid overloading any particular system.
3. Active Threat Monitoring
There’s no escaping a proactive attitude when it comes to preventing DDoS attacks. You should employ constant log monitoring to identify any weird network traffic patterns in the early stage.
Weird traffic spikes, unusual network activities, anomalous requests or IP blocks, these can all be identified beforehand.
Having more time to prepare before a DDoS attack starts makes the difference between total disruption and a controlled damage mitigation.
4. Use a Content Delivery Network
Caching resources with a Content Delivery Network will decrease the number of requests on the origin server. This will reduce the chance of overload during a DDoS attack.
This strategy is often overlooked by webmasters and business owners but it’s an easy solution that will take you far in preventing DDoS attacks.
5. Rate Limiting
With Rate Limiting, you can limit the amount of network traffic that goes through your network for a given period of time.
Web servers will be more resilient to DDoS attacks and mass requests from specific IP addresses. Rate Limiting is especially useful against botnets that will spam a specific endpoint with many simultaneous requests.
6. Move to the Cloud
Scaling your business to the cloud will mitigate most DDoS attacks because the cloud has more bandwidth to work with. You no longer rely on limited local resources but on cloud-based ones that can be much larger.
A cloud-based hosting provider like CloudFlare can significantly reduce the risk of DDoS attacks through their systems. These companies usually have anti-DDoS protection in place, as well.
These six prevention methods should help you avoid most DDoS attacks before they have a chance to impact your business.
As always, caution and prevention are key to staying alive in any online industry!
How to Respond to a DDoS Attack
We’ve already seen how destructive DDoS attacks are, and I’ve talked about prevention method.
But what if, despite your efforts, your servers still get DDoS-ed by a sophisticated cyberattack? How do you respond in the most effective way possible?
That’s what I’m here to explain. Here are the 4 most effective response methods when hit by a DDoS attack:
1. Follow the Established Procedures
When an DDoS attack hits the servers, every relevant team member should follow the pre-established procedures:
- Who receives the DDoS notification?
There should be a security manager in charge of formulating the response plan and coordinating everyone else in mitigating with the DDoS attack.
Whoever notices the DDoS attack should notify the security manager or whoever is in charge of DDoS mitigation.
- Verify the DDoS attack
The next step is determining whether the current crisis is indeed a DDoS attack or just an unnatural flux of traffic during a busy business period.
Any escalation procedures will be on hold before this determination is made by someone with sufficient cybersecurity knowledge.
- Implement Escalation Procedures
Once you determine that you’re dealing with a DDoS attack, you should implement the escalation procedures.
For instance, you might divert the traffic to scrubbing centers, implement rate-limiting, and traffic filtering to mitigate the impact.
The next step is identifying the attacking IP addresses and blocking them to stop the DDoS attack.
Finally, restore your network operations after you’ve fully contained the DDoS attack, and learn your lesson.
2. Implement Rate Limiting
According to Imperva, “Rate limiting is a technique to limit network traffic to prevent users from exhausting system resources”.
It’s one of the best mitigation methods against DoS and DDoS attacks, and many APIs will have it implemented by default.
Once the API detects that a client is making too many calls and sends too many requests, they’ll throttle or temporarily block it.
There are three types of rate limits:
- User Rate Limits – it tracks a user’s IP address and blocks it from making too many requests in a given timeframe. This is the most used rate limiting method in the industry
- Geographic Rate Limits – it tracks the users’ geographic location and sets a rate limit to them. This is especially useful when you have behavioral data for users in a particular region, and you know when they’re most active or least active
- Server Rate Limits – you can set rate limits specific to any given server, if you know that some servers will be more commonly used
Rate Limiting acts as both a prevention and mitigation procedure for DDoS attacks because once the DDoS attack begins, you might change rate limiting protocols based on the current attack conditions.
3. Add New Servers to Mitigate Overloading
Once you’re hit with a DDOS attack, you don’t have too much time to act. One of the first things you should do is add new servers to distribute the traffic load.
This will lower the chance of any server overloading and shutting down the systems. This is why you should already have network redundancy and spare servers that you don’t use.
While this doesn’t stop the DDoS attack, it preserves your system and keeps you operational until you can block the invading IP addresses.
4. Migrate to a New IP Address
Another (temporary) solution to a DDoS attack is to migrate legitimate traffic to another IP address to preserve business functionality and avoid a complete shutdown.
This is an inexpensive process that will buy you time for other, more long-term mitigation methods.
The attackers will eventually find the new IP address and start flooding it with requests, so don’t expect this short break to last long.
Migrating to a new IP address might also be difficult from an organizational perspective. You’ll need to make some internal changes to accommodate the moved resources to the new IP address.
Conclusion
DDoS attacks are among the most common cyberattacks in 2023, and they’ve become a more significant threat than many realize.
More companies are falling victim to DDoS attacks than ever before, and hackers are becoming increasingly sophisticated in their methods.
While cybersecurity can still combat these threats, it must be implemented correctly—no more mistakes, cutting corners, or relying on hope.
Security awareness must be a top priority for any online company, regardless of the industry.
Employees need to be trained to accurately identify the warning signs of DDoS attacks and respond effectively to mitigate them.
Ultimately, companies need to adapt quickly if they hope to stay afloat in today’s digital landscape. With cybercrime at an all-time high, robust cybersecurity is no longer optional but essential.
Conclusion
The Guardian – DDoS Attack that Disrupted Internet Was Largest of Its Kind in History, Experts Say
CloudFlare – What Is the OSI Model?
GeeksForGeeks – TCP 3-Way Handshake Model
eSecurityPlanet – How to Tell if You’ve Been DDoSed: 5 Signs of a DDoS Attack
Imperva – DDoS Attacks
PropertyCasualty360 – 5 Most Targeted Industries for DDoS Attacks
AtlasVPN – 65% of All DDoS Attacks Target US and UK
Blog Cloudflare – DDoS Threat Report for 2023 Q2
Akamai – Akamai Research Shows Attacks on Gaming Companies Have More than Doubled Over Past Year
Comptia – What Is a DDoS Attack and How Does It Work?
ForcePoint – What Is Spoofing?
SecureList – DDoS Attacks in Q4 2019
Kasperski – DDoS Attacks Increased by 18 Percent in the Second Quarter Compared to 2018
SecureList – DDoS Attacks in Q3 2022
Fortinet – DoS Attack vs. DDoS Attack
Corero – The Damaging Impacts of DDoS Attacks
Statista – Average Cost per Hour of Enterprise Server Downtime Worldwide in 2019
Privacy Affairs – What Is Cyber Insurance and How Does It Impact Cybercrime?
Cloudflare – How to Prevent DDoS Attacks | Methods and Tools
SecurityScoreCard – Benefits of Continuous Compliance Monitoring in the Cloud
Red Button – How to Identify and Respond to a DDoS Network Attack
Imperva – Rate Limiting

