How to Encrypt Your Internet Connection – Complete Guide
As a regular internet user, you’ve probably heard the term encryption. Many internet users have no clue what encryption is, but you must know why you need to encrypt your internet connection and how you can do so.
Prying eyes on the internet abound. That’s why most popular messaging applications, like WhatsApp and Viber, implement end-to-end encryption. You, too, should hide your data and bolster your defenses.
This article will serve as an in-depth guide on encrypting your connection journey. Cybercrime is rampant in this day and age — you don’t want to be caught vulnerable.
What Is Encryption?
Generally, encryption makes data unreadable. The purpose of encryption is to secure your data from unauthorized access and keep your privacy intact.
Encryption uses cryptography techniques to scramble the messages or data you send so that it becomes unreadable to everything and everyone except that data’s intended recipient.
Encryption is an essential security tool to protect sensitive data from the wrong hands.
Why Encrypt Your Internet Traffic?
A bunch of reasons! Here are some highlights:
- To cover your browsing tracks. Tracking your browser history is sometimes valid regarding better product or movie suggestions. However, there will come a point when it feels too invasive. After all, you need your personal space on the internet, too, right?
- To stay safe from potential hackers. You might be thinking, Why would a hacker want my details anyway? I’m just an ordinary citizen. Well, don’t get complacent. If you’ve got money, that’s enough reason for a hacker to take an interest in you and your online banking credentials. Hackers can observe your internet data, access your bank accounts, and rob you blind. Encryption can protect your login usernames and passwords from being seen by intruders.
- To shield yourself from the prying eye of the government. Nowadays, the government loves to pry into internet traffic. You might think they’re only trying to protect you from cultural exploitations and insecure websites, but there’s more to it. Many governments don’t respect their citizens’ privacy. And countries like China have many restrictions regarding people using the internet, especially on social media.
- To stay away from the prying eyes of ISPs, too. They’re not all that innocent either. ISPs can sell your internet data to advertisers and marketing agencies to boost their businesses. Some don’t even consider network neutrality. Whenever they see you do something that requires higher bandwidth, they can slow down your connection.
Convinced you need to encrypt your internet traffic? Good. Keep reading…
How to Encrypt Your Internet Traffic?
You’ve got some options:
- Tor Browser
- HTTPS
- End-to-end encrypted messaging applications
- Encryption in the local Wi-Fi network
- A good VPN
Tor Browser
Most VPNs require you to purchase a subscription for maximal benefit. But another feasible solution to encrypt your data is the Tor Browser.
This is free software! It’s an open network that can help you stay anonymous and defend against potential cyber attackers and privy government agencies.
Those annoying third-party trackers and ads can’t follow you, as every website you visit is isolated by the browser.
And your browsing history and cookies are cleared automatically when you finish your work. In a standard browser, that happens only manually, usually when an issue occurs.
The Tor Browser offers multi-layered encryption. It relays your internet traffic and encrypts it three times when passing through the Tor network. Not only that, but it also gives you ways to defend against ISPs and governments watching your internet traffic.
You can download Tor Browser here.
HTTPS
The secure version of HTTP is known as the HyperText Transfer Protocol Secure (HTTPS). It’s primarily used for sending data between a website and a browser. HTTPS is encrypted so that the security of the transferred data is ensured. So what makes this secure?
TLS (Transport Layer Security) encryption techniques are used here. HTTPS authenticates the data sender and receiver at each end and ensures that the data sent hasn’t been breached, ensuring integrity.
With an added layer of encryption with HTTPS, all your usernames, passwords, credit card information, and other sensitive information is protected.
How do you know if the website you’re visiting has HTTPS enabled? Easy. Look at the URL in your browser, and you’ll see the address starting with “https://” if HTTPS is enabled.
Otherwise, the URL will have a warning message: “Not Secure.”
The problem is that not every website uses HTTPS, but you can enable it using your browser settings and with the help of third-party applications.
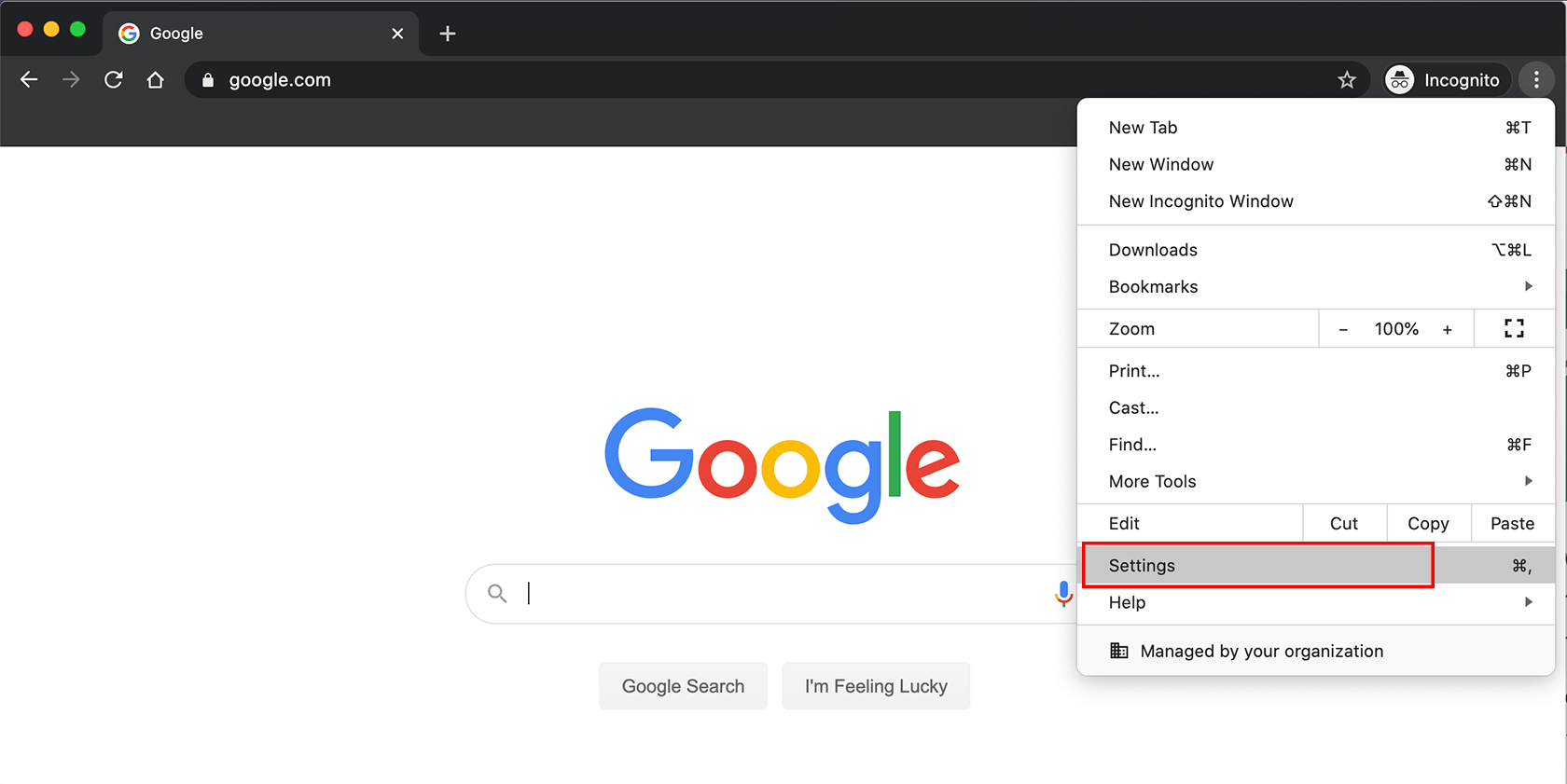
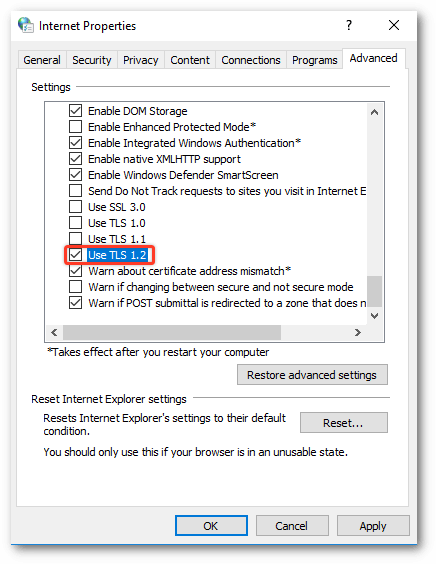
How to enable SSL certificates in Chrome using Windows
1. Go to Settings.
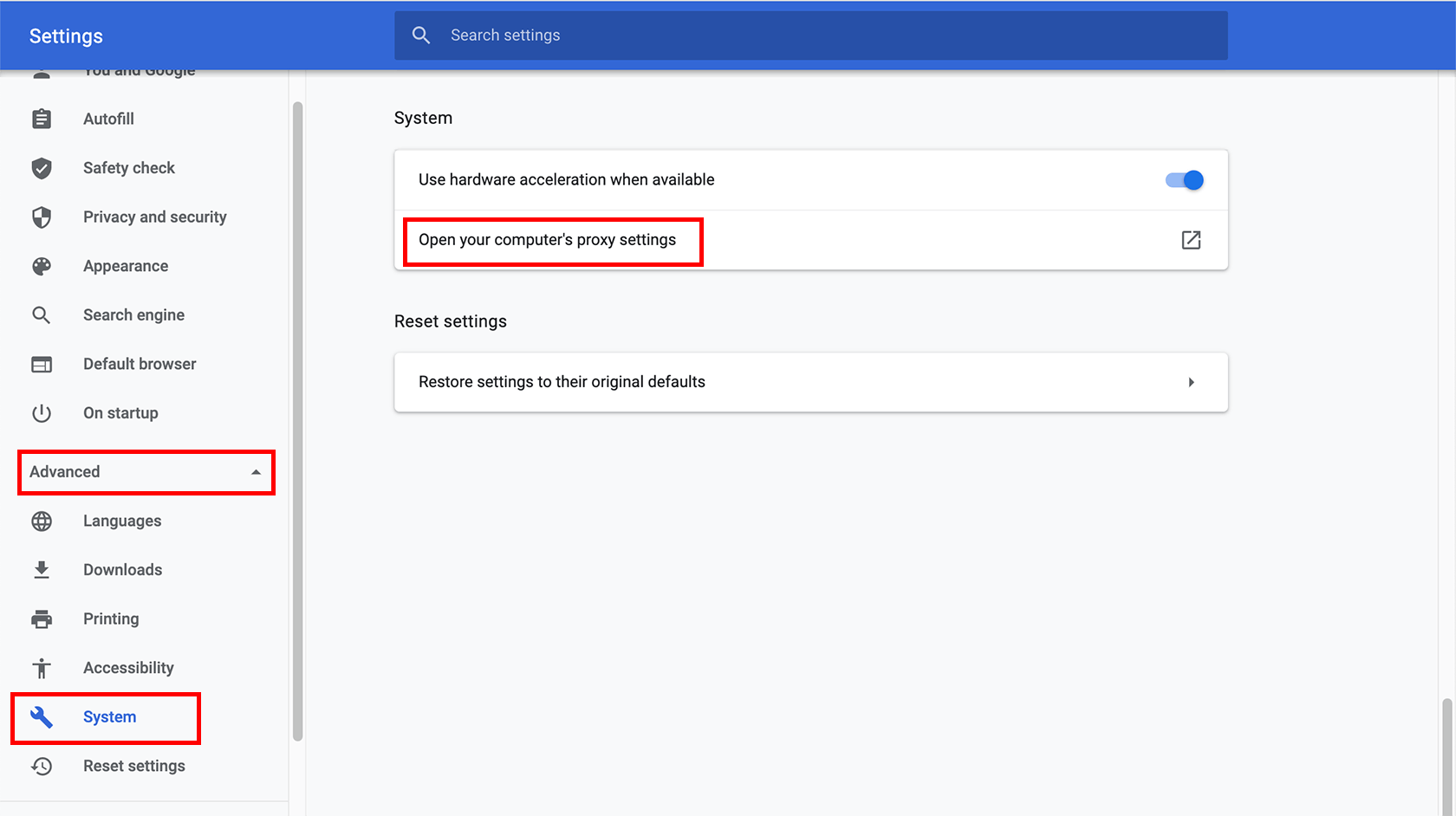
2. Then click on System settings under the Advanced option.
3. Then click on “Open your computer’s proxy settings.”
4. Check the option box next to “Use TLS 1.2”.
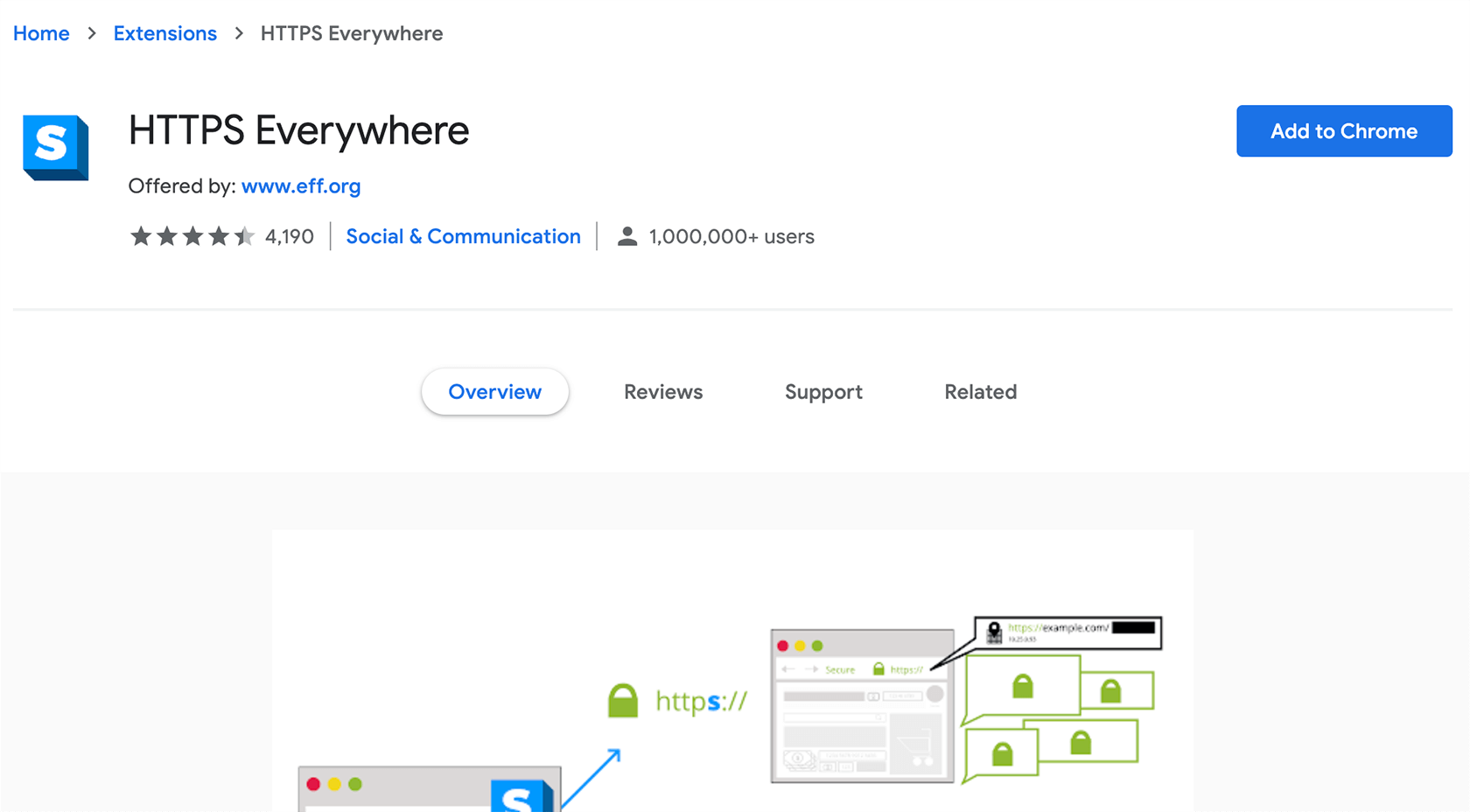
Using HTTPS everywhere
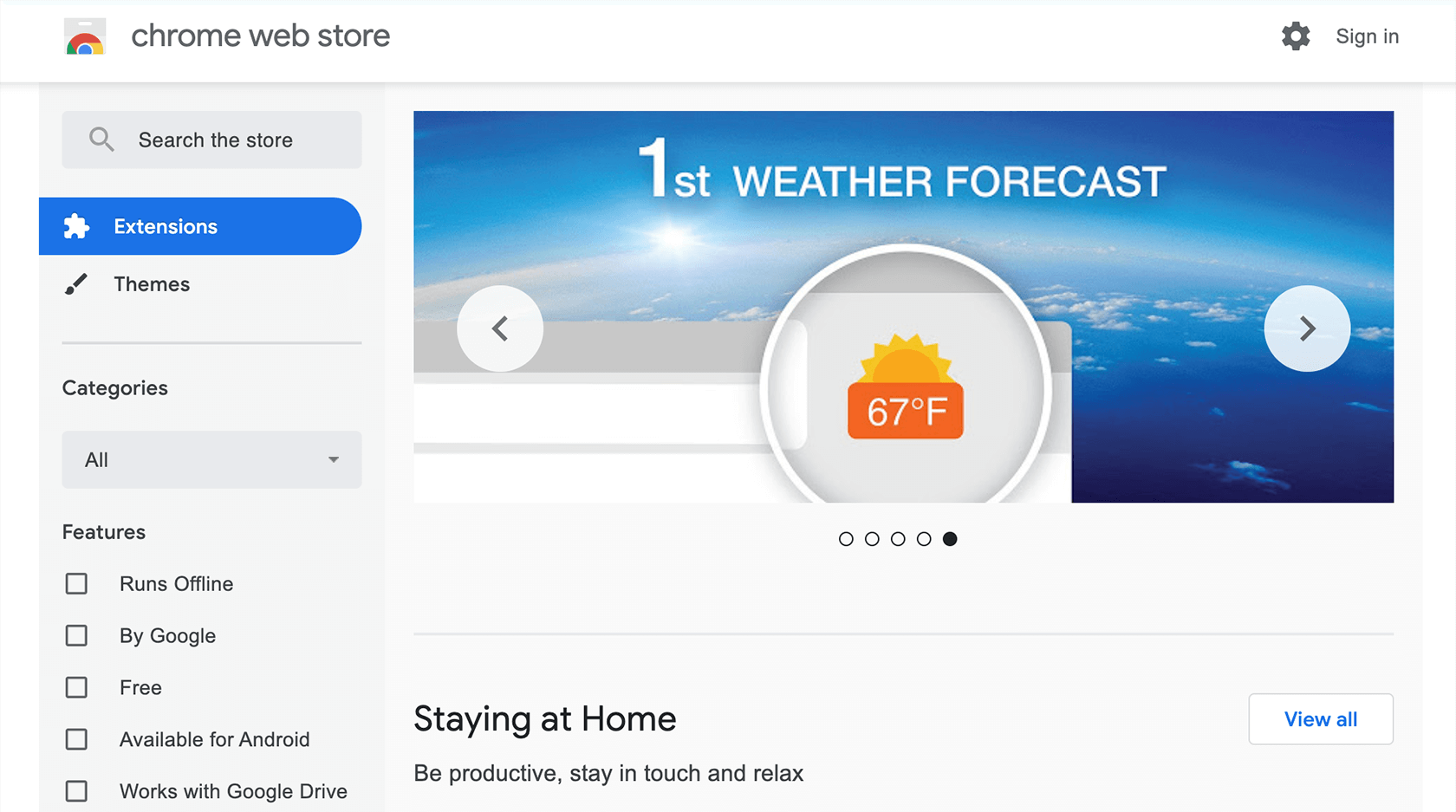
This is another option where you can enable HTTPS encryption. You can get the “HTTPS Everywhere” extension by the Electronic Frontier Foundation via the Chrome Web Store. Here’s how:
1. Go to the Chrome Web Store.
2. Search for “HTTPS Everywhere” and click on the “Add to Chrome” button.
3. Click on the “Add extension” button.
This extension is available for Firefox and Opera as well.
End-to-end encrypted messaging applications
Did you know that your standard SMS texts aren’t encrypted at all? Third parties won’t be able to spy on your messages and monitor them. That’s why it’s better to use messaging apps that offer end-to-end encryption.
So what exactly is end-to-end encryption?
End-to-end encryption (more commonly referred to as E2EE) guarantees that only you (one end) and the person you’re communicating with (the other end) can read and modify the data being transferred. Transferred information is encrypted on the sender’s end, and only the receiver can decrypt it.
Let’s look at some popular messaging apps that offer these encryption facilities.
Owned by Facebook, WhatsApp is currently the most popular messaging platform globally. You can send and receive messages, share images and videos, and take audio and video calls — all enabled with end-to-end encryption.
WhatsApp security guarantees that only the user and the person communicating with that user can read the sent messages. Not even WhatsApp itself can read the data.
The message you send is secured with a lock, and only the receiver of that particular message can unlock it with a unique key and read the message.
Not only that, but each message has a unique lock and key, which makes it more secure. WhatsApp does this automatically, and you don’t need to worry about how to turn the encryption on in the settings.
Viber
Viber didn’t have end-to-end encryption until version 6.0 was released. This release brought more security to its vast user range of over 900 million globally.
Known as Rakuten Viber since 2017, it provides quality messaging and calling services, all secured with end-to-end encryption.
Wickr Me
Wickr Me is a private messenger application provided by Wickr, and it’s all about the privacy and security of your data.
Wickr’s mission is to provide a secure communication platform trusted by individuals, teams, and corporations across industries, sizes, and scales, to manage their most valuable communications.
With its 256-bit, authenticated end-to-end encryption, only the intended receivers can read messages; not even Wickr can obtain the decryption keys.
Wikr’s other advanced security features include multi-factor authentication, encryption of devices at rest, client network traffic obfuscation, detecting screenshots being taken, and many more.
Read more about Wickr security here.
Signal
Signal, a cross-platform messaging application across Android, iOS, macOS, Windows, and Linux operating systems, can be used to send messages to individuals or groups.
These messages may consist of audio files, images, videos, and voice messages, all encrypted by Signal. The Signal Foundation and Signal Messenger LLC built it.
Signal invites you to share securely. It boasts state-of-the-art end-to-end encryption supported by the open-source Signal Protocol. Like the apps above, no one — not even Signal — can listen to or read your messages.
Encryption in the Local Wi-Fi Network
This is the most basic option to start encrypting your internet traffic. Ensure you’ve set a password when joining your Wi-Fi network; otherwise, this is vulnerable to any attacks by anyone who can access the wireless router.
People nearby can freely access the router and gain access to your internet traffic. Who knows what information they may see in your browsing history?
Encrypting your Wi-Fi connection is pretty straightforward:
1. Enter the router’s IP address in the address bar of your web browser and enter the admin panel. This is usually 192.168.1.0 or 192.168.1.1. If none work, check the bottom of your router to get the correct IP address.
2. Log in to the admin panel by entering the username and password.
3. Click on the “Network” option and go to “Security” settings under “WLAN.”
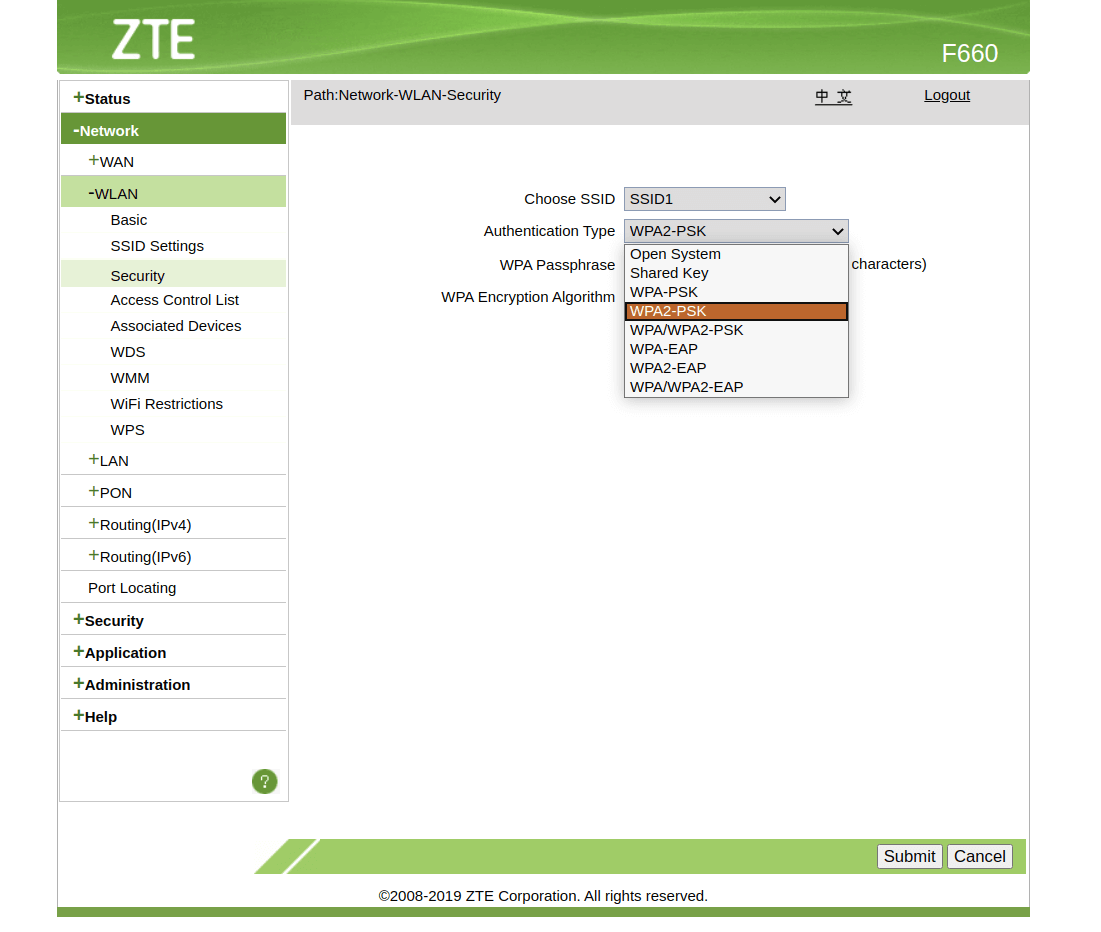
4. You’ll see several options under the authentication type. Enable WPA2-PSK. The other options — WEP (Wired Equivalent Privacy) and WPA (Wi-Fi Protected Access) — are much older encryption versions and more vulnerable to attack.
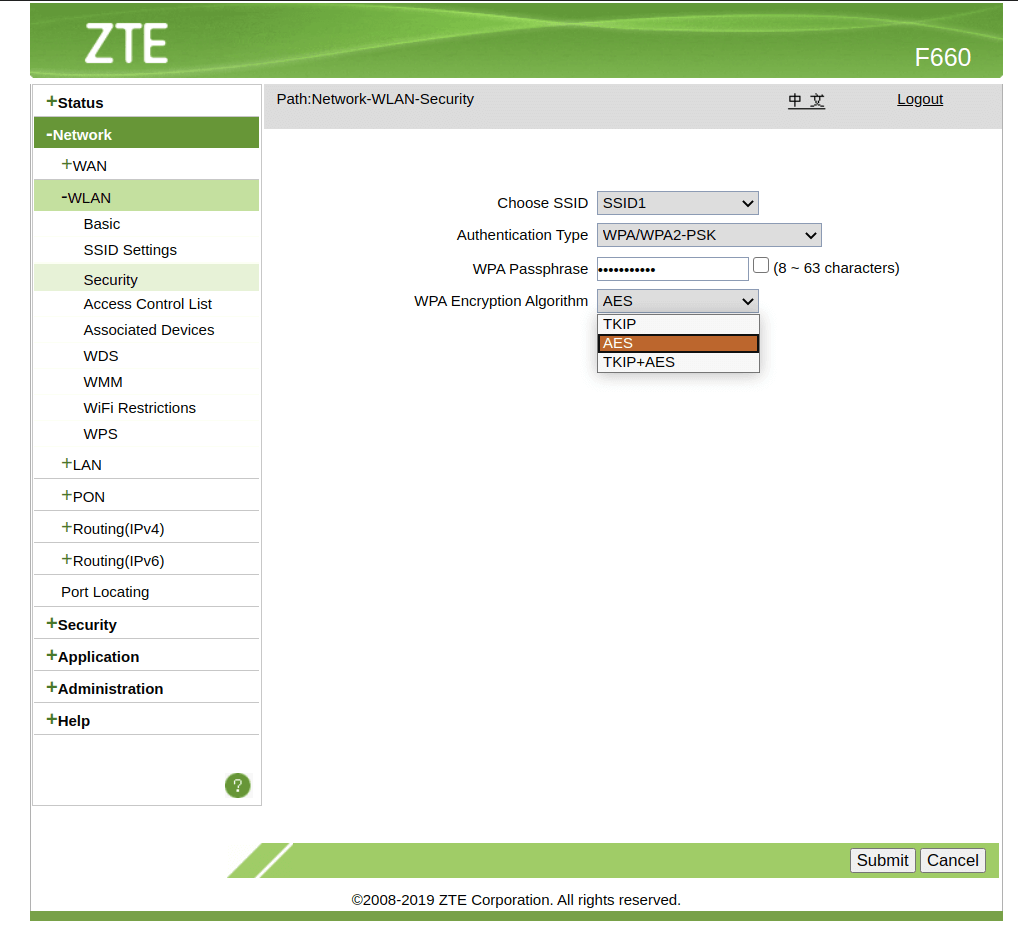
5. Next, set a strong password for your Wi-Fi router.
6. Finally, choose “AES” as your WPA encryption algorithm.
7. Save and exit.
A Reliable VPN service
A reliable VPN (Virtual Private Network) is the best way to encrypt your data. A VPN protects your privacy online and keeps you anonymous by creating a private network from a public internet connection. Your IP address is masked, so no one can track your activities online.
The best thing is that the data that’s transferred is encrypted. So, in a nutshell, a VPN not only hides your identity but also protects your data.
As a bonus, you can configure almost any internet-connecting device with a VPN provider, your mobile phone, your personal computer, and even your router.
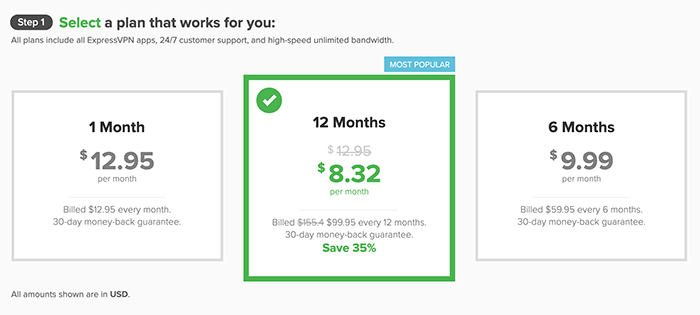
Some of today’s best VPNs are ExpressVPN, NordVPN, SurfShark, VyprVPN, and IPVanish. These VPN vendors allow you to use the application with multiple devices using the same subscription. Yes, some VPNs can be expensive, but the benefits you’ll gain are worth the money.
How to encrypt your data with a VPN
1. Choose a VPN and create an account – we recommend ExpressVPN
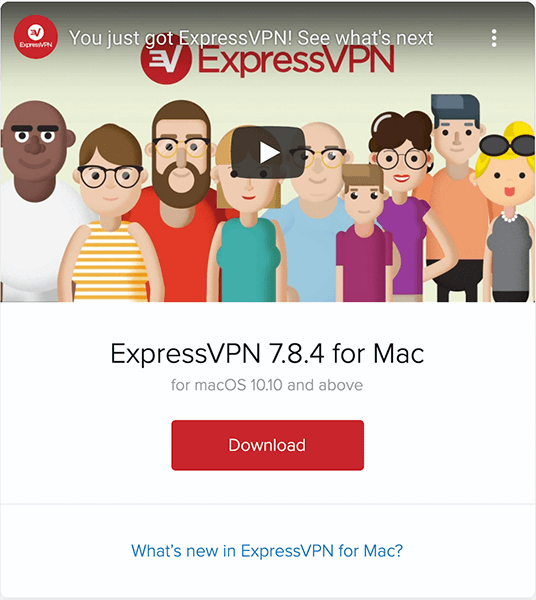
2. Download ExpressVPN.
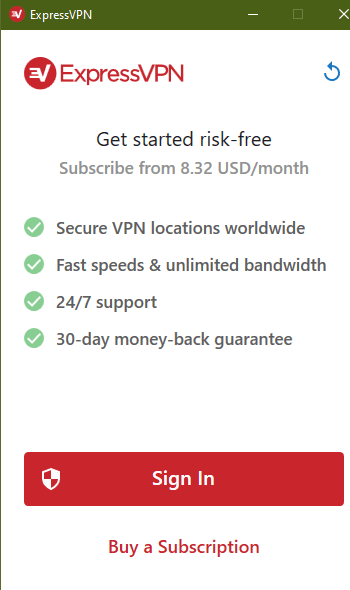
3. Log in to your account.
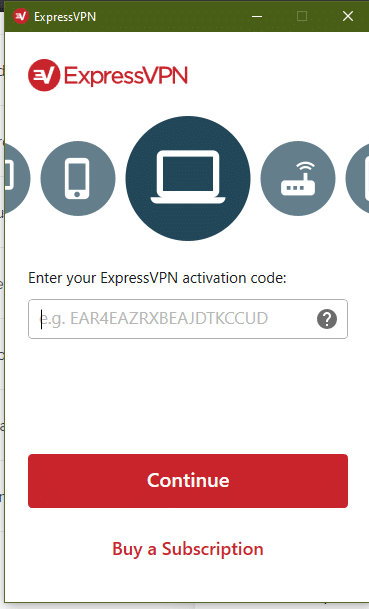
4. Activate your subscription.
5. Connect to a server of your choice.
Different Types of Encryption
Now that you’ve got a good idea of encryption basics, let’s quickly explore a few other kinds of encryption. Here are the most popular:
- Triple DES or Triple Data Encryption Standard. TDES applies the original DES cipher algorithm three times on every data block. Although it’s much slower than the single DES process, it provides more security.
- Advanced Encryption Standard (AES). This is also called Rijndael and is known to be the best encryption mechanism. That’s probably why this is the standard encryption type in the United States. Symmetric key encryption is used by AES, where only one secret key is involved in encrypting and decrypting the information shared.
- Rivest-Shamir-Adleman (RSA). RSA uses one-way asymmetric encryption. Its enormous key length, which can go up to 2048 bits, makes it harder to decipher the data encrypted by RSA.
What Else Can I Do to Protect Myself?
As technology advances, it brings both benefits and challenges. While encryption is a strong foundational defense, it is only part of a broader security strategy.
Additional protective measures include firewalls, robust passwords, enhanced authentication techniques, intrusion detection systems, and antivirus software, among others.
For those who prioritize the security of their data and information, exploring these additional methods to further strengthen your security posture is worthwhile.




4 Comments
TUbIdY
May 24, 2025 9:19 am
Great guide! I appreciate the detailed steps on encrypting my internet connection. The tips on choosing a VPN and setting up encryption protocols were especially helpful. Looking forward to implementing these suggestions for better online security!
s8 Game
April 19, 2025 5:08 am
This guide is super helpful! I had no idea there were so many ways to encrypt my internet connection. The step-by-step instructions made it easy to follow. I especially appreciated the tips on choosing the right VPN. Looking forward to more posts like this!
naomi
October 6, 2022 4:06 am
How to unblock Instagram at school
Anonymous
December 21, 2023 12:10 am
vpn