Liverpool City Council Website Targeted by NoName Hacker Group in Latest DDoS Attack
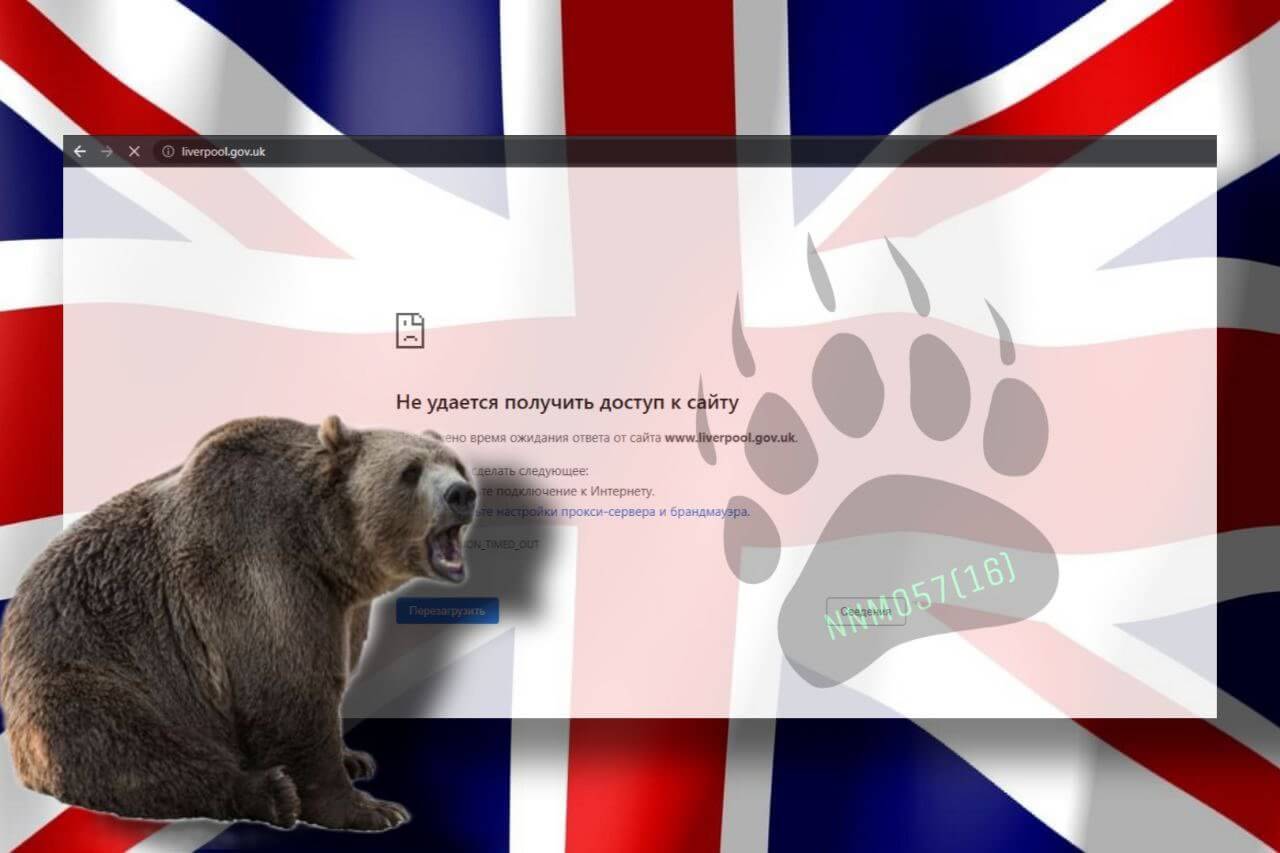
The Russian hacker group NoName has targeted Liverpool City Council’s website with a Distributed Denial of Service (DDoS) attack, causing temporary unavailability.
The group, known for attacking government institutions and companies with a pro-Ukrainian stance, has left the website currently not working.
- Russian hacker group NoName launches DDoS attack on Liverpool City Council website
- Website temporarily unavailable, currently not working
- NoName targets government institutions and companies with pro-Ukrainian stance
- Other recent attacks include Rheinmetall, French National Assembly, and Estonian & Ukrainian banks
The DDoS attack on Liverpool City Council’s website highlights the ongoing threat posed by the NoName hacker group to institutions supporting Ukraine.
The institution’s website is, as of the writing of this article, still unresponsive.
The Russian hacker group posted the following on Telegram:
DDoS attacks can lead to significant disruptions in public services, confusion, and frustration among citizens, and may undermine public trust in institutions’ ability to protect against cyber threats.
Other attacks by NoName
NoName has been active in targeting various European businesses and government institutions in recent times.
The collective has targeted Rheinmetall, a German weapons manufacturer anticipated to provide Ukraine with arms and ammunition, resulting in the temporary unavailability of its website.
Moreover, the group executed a DDoS attack on the French National Assembly’s website, causing it to be inaccessible on March 27.
NoName has also taken responsibility for assaults on the Scottish Assessors Association’s portal, a railway ticket sales platform in England, websites belonging to Europol GaZ Company and Poland’s national judicial council, the Italian Constitutional Court, and the nation’s transport regulation webpage.
In March, the group struck multiple Estonian and Ukrainian banks and organizations, such as the Bank of Estonia and BLRT Grupp.
Although NoName predominantly employs DDoS attacks to induce short-term unavailability of their targets’ websites, no data breaches have been linked to their operations thus far.
It is likely, but not currently known for sure, that NoName operates on behalf of or is even part of Russian Intelligence services.

Our Mission
We believe security online security matters and its our mission to make it a safer place.

