Cybersecurity Deep Dive: What Is the Principle of Least Privilege?
The Principle of Least Privilege (POLP) is the limitation of privileges of company employees to only what they need to perform their jobs.
In other words:
- Employee X needs read access to Databases A, B, and C
- Employee X is attributed only with read access (not write access) to Databases A, B, and C
This might seem self-explanatory but, in most companies, this is not how privileges work. Most employees have more privileges than they need to.
In the example above, employee X would also have “write” access to those databases, which allows his device to enter or modify data within those databases.
Why is this a problem? Because it increases the attack surface and attack vectors in the case of a cyberattack.
Benefits of POLP
The Principle of Least Privilege is the best standard in cybersecurity because it provides a wide number of benefits to a business/network:
1. Minimizes the Attack Surface & Attack Vectors
The attack surface represents the total number of attack vectors in a network that a threat actor can exploit for malicious intents.
It assumes that it is preferable to have fewer individuals/device with access to a given resource.
To better understand, imagine that you’re leaving to the store and you leave your front door unlocked and two of your windows opened.
If a thief decides to break in, they have three access avenues:
- Your front door
- Window 1
- Window 2
Now let’s reimagine the scenario and assume that you close your front door and leave only one window opened.
A burglar will now only have one access point – the opened window.
The two situations showcase how the limitation of attack vectors will minimize the attack surface that an attacker can exploit.
Within a company, the Principle of Least Privilege ensures that there are as few exploitable access points as possible to a given resource.
If only Employee X has write access to Database A, that means that Database A can only be infiltrated through one access point – Employee X’s device.
Similarly, if Employees X, Y, an Z have write access to Database A, that means that Database A can be infiltrated through three access points – Employees X, Y, and Z’s devices.
In cybersecurity, POLP says that one access point is better than three access points.
2. Limits Lateral Movement of Malware
Another important benefit of the Principle of Least Privilege is that it keeps lateral network movement under tight control.
In cybersecurity, lateral movement refers to the spread of a malware from one system to the other, or from one resource in the network to another.
With the Principle of Least Privilege implemented, lateral movement is restricted because an infected device doesn’t have access to many company resources.
Let me explain:
- Company A has a network comprising of Resources A, B, C, D, and E. They implement POLP
- Employee X only has access to Resources A and B
- Employee X’s device is infected with malware from a phishing site
- The malware can only spread to Resources A and B, not C, D, and E. This is because Employee X has no access to Resources C, D, and E
Take a look at the image below to understand better.
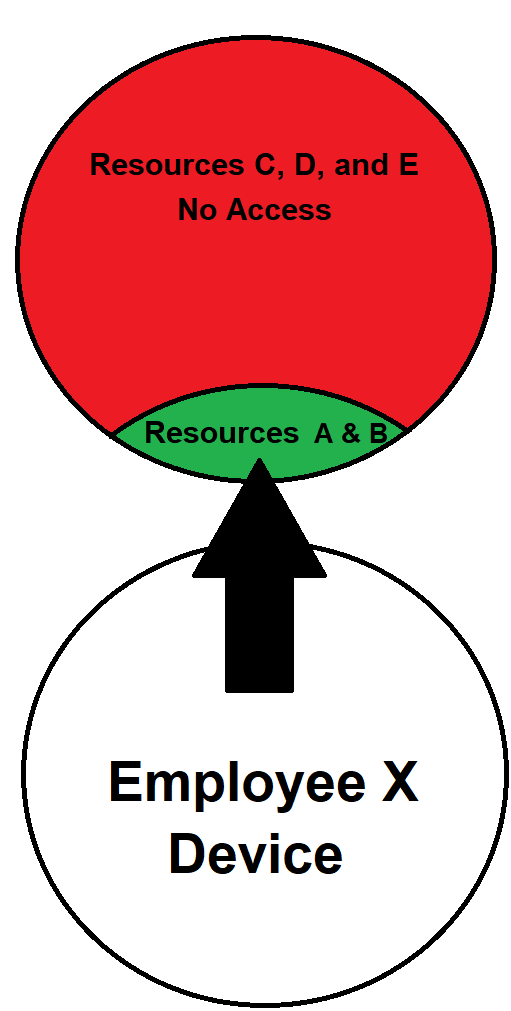
In the image above, you can see how Employee X’s device can’t access Resources C, D, and E. Likewise, any malware on his device won’t be able to spread to those resources.
Only a large portion of the network (Resources A & B) will be infected by the malware, while the biggest portion will remain unaffected.
3. Decreases the Chance of a Data Breach
Through the Principle of Least Privilege, you can decrease the likelihood of a data breach happening.
Most data breaches occur when a hacker exploits the privileged access of a company employee. But if very few employees have privileged access, then hackers won’t have any entryways into the company network.
Through POLP, you can even limit an employee’s access to internet or impose strict download requirements.
For instance, employees should only be able to download files coming from verified and pre-validated company sources.
Plus, when a hacker will realize that the lateral movement is reduced to almost zero, they’ll give up on the infiltration.
4. Improves Employee Productivity and Business Performance
In a clearly-structured ecosystem where each employee has strict privileges and responsibilities, the workflow is unimpeded.
However, if employees have super privileges that they don’t need, they may end up dealing with troubleshooting issues on systems they don’t need to use.
This leads to less overall productivity and more time waste.
Likewise, providing elevated privileges on an as-needed basis and then removing it when no longer needed increases employee productivity.
Furthermore, in the event of a data breach or malware infiltration, the system’s downtime is lessened significantly with POLP implemented.
The network becomes operational much faster, and employees can resume work quicker.
5. Keeps Track of Data Classification
With the Principle of Least Privilege implemented, it’s easy to identify those responsible for allowing unauthorized access on their machines.
If a resource becomes part of a data breach, POLP lets you find the parties who had access to that resource and identify the entry point easier.
It also lets you understand how human error played a part in the data breach and what you can do to prevent it in the future.
6. Ensures Compliance with Security Regulations
If you operate in Europe, then you have to comply with the GDPR. Other regulatory institutions are the SOX, HIPAA, and PCI DSS.
All of these regulatory entities require companies to enforce the Principle of Least Privilege in its operations.
It became an absolute requirement following the massive data breach caused by Edward Snowden during the NSA leak.
When your company is audited, not having POLP implemented means you’re breaching operational requirements and will be fined or asked to rectify these issues immediately.
How to Implement the Principle of Least Privilege

There are multiple stages to effectively implementing the Principle of Least Privilege:
- Revert all user accounts to the lowest-possible privilege
The first step is placing all employee accounts on the lowest-possible privilege. That should be the starting point of POLP implementation.
Assign higher-level privileges only to employees who need it on a daily basis to perform their duties.
So, the logic is that you should manually increase the privilege when needed and not decrease it from a higher default.
- Perform a company-wide verification to identify privilege needs and assign them
Once you revert all accounts to the lowest privilege, it’s time to see who needs what privilege.
A company-wide audit will do the trick. Check all employee accounts, processes, programs, access keys, duties, passwords, access endpoints, and so on.
Assign higher-level privilege based on an as-needed basis for long-term access needs. Don’t take into account one-time access needs.
Accounts who may need one-time higher-privileges to access a resource should be on the lower privilege by default.
- Monitor temporary higher-privilege activities and cancel them afterward
If any employees need higher-privilege access temporarily, someone should closely monitor these activities.
Just-in-time access allows for the as-needed assigning of higher privileges to anyone within the company.
However, their activities during these moments should be closely watched. Then, those privileges should be canceled as soon as they are done performing their duties.
Unnecessary privileges should not remain assigned for any longer than needed.
- Separate and isolate administrator and standard access privileges
Access requests should be isolated by privilege checkpoints within the organization. Even someone with admin privileges should only be able to utilize those privileges after a validation.
Lower-level duties only require standard user privileges, while higher-level duties require specialized privileges. The latter should be separate from the former.
This ensures that, even if a single person possess both low and high-level privileges, they won’t have unlimited access to all company resources.
- Always assign the lowest-required privileges to new employees
New employees should always be given the lowest privileges until the exact privileges required for the job are determined.
Then, the new employee should be seamlessly introduced into the POLP workflow, including the one-time higher-privilege monitorization.
- Perform monthly privilege reevaluations
It’s unlikely that the logistics of your company will remain the same, that departments aren’t restructured, and that employees won’t change roles.
All of these stages imply privilege acquisition and revoking. You should reevaluate these privileges monthly to make sure that everyone within your organization has the least privilege necessary.
The most dangerous situation that can arise is Privilege Creep.
What Is Privilege Creep?

Privilege Creep happens when unnecessary higher privileges slowly accumulate over time because the sys-admins don’t revoke them when no longer necessary.
The core idea behind POLP is to provide limited higher privilege on an as-needed basis and then revoke it when it’s no longer needed.
However, it’s human to err. And sometimes you forget. Which means you might not immediately revoke your junior coworker’s superior privileges after he’s finished his task.
But this also means that:
- There’s one more access point for a hacker to exploit
- The risk of a catastrophic mistake being made has just risen by one
Your junior coworker might make a fatal mistake and delete all the customer details from the database.
That wouldn’t happen if his higher privileges to edit the database were revoked. This is what the Principle of Least Privilege aims to correct, among other things.
Conclusion
The Principle of Least Privilege assumes that humans are inherently inclined to make mistakes and/or become rogue agents.
By separating data access through privileges and starting with the lowest privilege for everyone, you minimize the external attack surface, reduce network vulnerabilities, and avoid internal malicious attacks.
In other words, you decrease the chances of a data breach significantly.
Cybersecurity needs to be taken more seriously, especially at a corporate level. The emergence of Cybercrime-as-a-Service has changed everything.
We need to stop hoping for the best and do our best right now through proactive measures like POLP!
Sources
StrongDM – Principle of Least Privilege (How to Implement It)
CrowdStrike – Lateral Movement
Reuters – NSA to Cut System Administrators by 90 percent to Limit Data Access
F5 Labs – What Is the Principle of Least Privilege and Why Is It Important?
HeimdalSecurity – What Is Privilege Creep and How to Prevent It?
Privacy Affairs – Cybersecurity Deep Dive: What Is Cybercrime-as-a-Service?

