A Comprehensive Comparison of VPNs and Onion Routing (TOR)
Virtual Private Networks (VPN) and The Onion Router (Tor) have much in common. Both VPNs and Tor encrypt and proxy your traffic before sending it off to its ultimate destination.
And both Tor and a VPN will hide your real IP address and, hence, your location from the sites and services you access online. So both make you harder to identify and track.
- What VPNs are and how they work
- How a VPN keeps your internet traffic private
- What TOR is and how it works
- How TOR can ensure both privacy AND anonymity.
- VPN vs TOR: Differences and similarities
- Use cases for VPNs and TOR
But despite these similarities, VPNs and Tor are different beasts with different purposes. This post will look at VPNs and Tor, how they work, and when you should use one over the other.
Let’s start with VPNs.
Both VPNs and Tor provide encryption and act as proxies for your internet traffic, masking your actual IP address and geographical location. However, while VPNs primarily focus on enhancing privacy, Tor is specifically designed to achieve greater anonymity.
VPNs operate through centralized services provided by companies, whereas Tor relies on a decentralized framework maintained by a global network of volunteers. We examine the distinct scenarios where each technology excels: VPNs are ideal for overcoming censorship or geographic restrictions, while Tor is better suited for anonymous web browsing or accessing the Dark Web.
Additionally, we discuss the strategy of combining VPNs and Tor to maximize security, noting that this approach may result in reduced internet speeds.
What is a VPN?
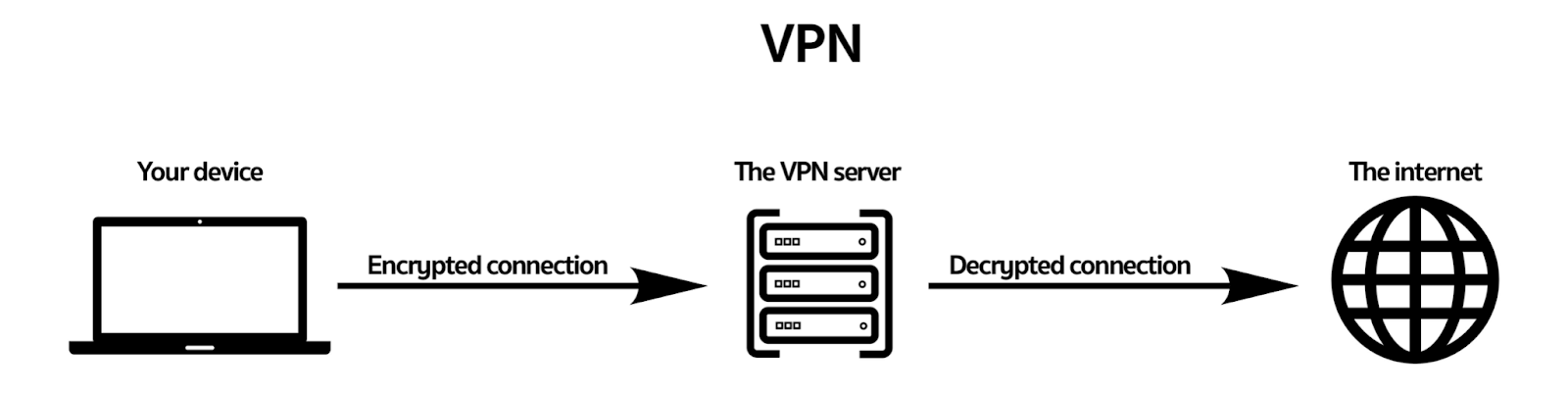
A VPN is a server that sits between your device (computer, tablet, smartphone) and the internet.
From your device, you initiate an encrypted connection to the VPN server. Once connected, all your traffic goes through the VPN server, is encrypted, and decrypted before going to the requested website or service.
This is how a VPN works:
Because your connection to the VPN server is encrypted, third parties (including your ISP) cannot know what you’re doing online.
Your ISP will see you’re using a VPN because you initiated the connection from your ISP’s network. But once the connection is made, the encryption cuts it out of the loop.
While it’s possible to detect VPN traffic and many websites, such as Netflix, detect and block VPNs, there are ways to make the VPN connection more resilient to blocking by switching protocols and ports or by using obfuscating proxies.
Using a VPN can help you bypass the geo-restrictions of streaming services like Netflix and access content that is normally only available in certain countries.
For example, if you want to access American Netflix content from outside the USA, you can use a VPN to spoof your location and appear as though you’re in the USA.
Check out our guide on the best VPN for American Netflix to find a reliable VPN that can help you access this content.
Some VPN service providers, though not all, offer some of these options to their users.
A VPN also replaces your ISP-provided IP address with the IP address of the VPN server to which you’re connected.
So any websites you access will only see the VPN server IP address, and the site will consider you as being in the server’s location even though you may be thousands of miles away.
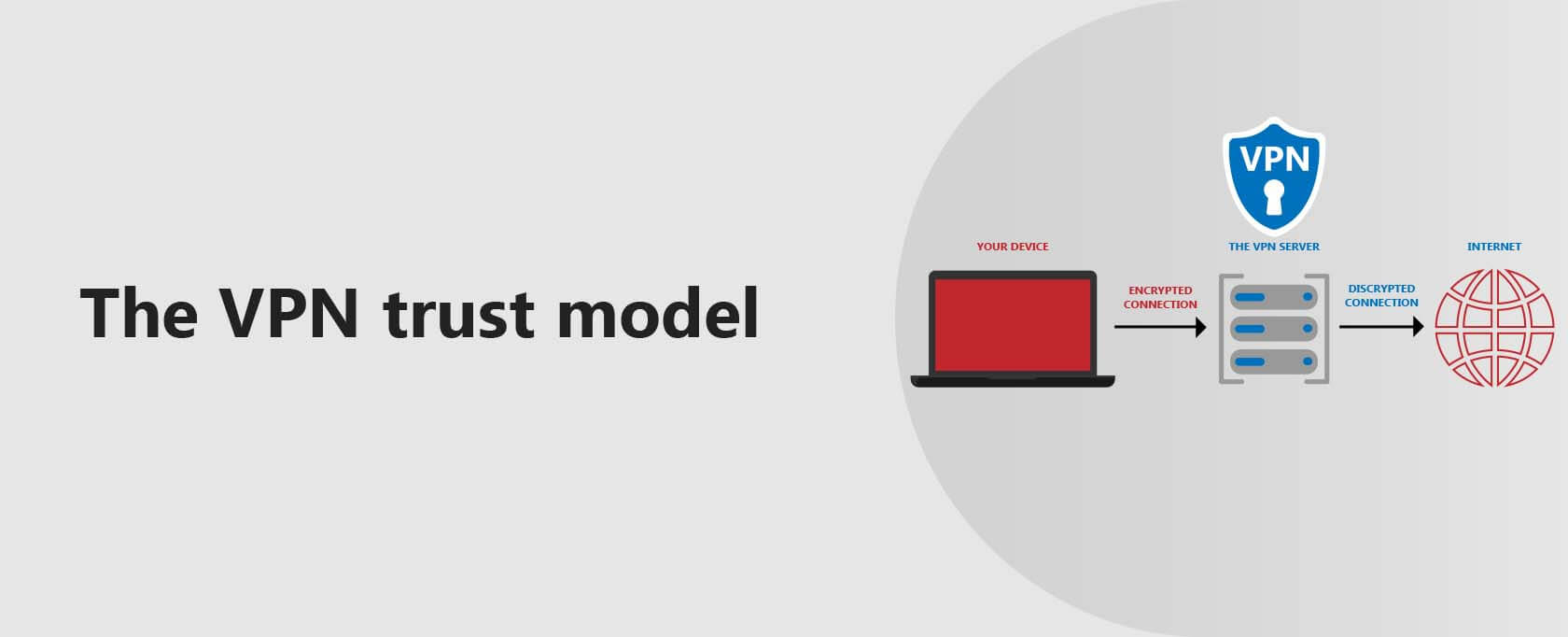
The VPN trust model
The trust model with VPNs is essentially all or nothing. You need to trust your VPN provider fully because you’re sending all your internet traffic through its servers. Your VPN provider has the technical ability to log everything you do.
VPNs are a centralized service. That means that one party holds all of the keys and hence, one point of failure or compromise. The trust model is an important distinguishing feature between VPNs and Tor.
Choosing a good VPN provider and taking the time to read its privacy policy in general and its logging policy, in particular, becomes crucial. Pick the wrong VPN provider, and you could be worse off than simply using your ISP connection.
Free VPNs are not recommended, as they tend to log and sell your data, defeating the purpose of using a VPN in the first place.
A good VPN provider will have a written privacy policy and a robust no-logging policy. Ultimately, you’ll still have to take them at their word. But you can at least make an informed decision.
Using a VPN
To use a VPN, you’re going to need a VPN client. That’s usually going to be an application produced by the VPN provider you signed up to. It could also be a third-party client, but this is becoming less frequent.
Native VPN clients (VPN client apps produced by the VPN provider) are typically very easy to use, and many require you to press a large “Connect” button to initiate a connection, as in the image below (from ExpressVPN).
Once you’re connected to a VPN server (using a native or a third-party client), all of your traffic, from your WhatsApp messages to the websites you browse, is sent through the VPN server. The VPN connection is applied system-wide.
What is Tor?
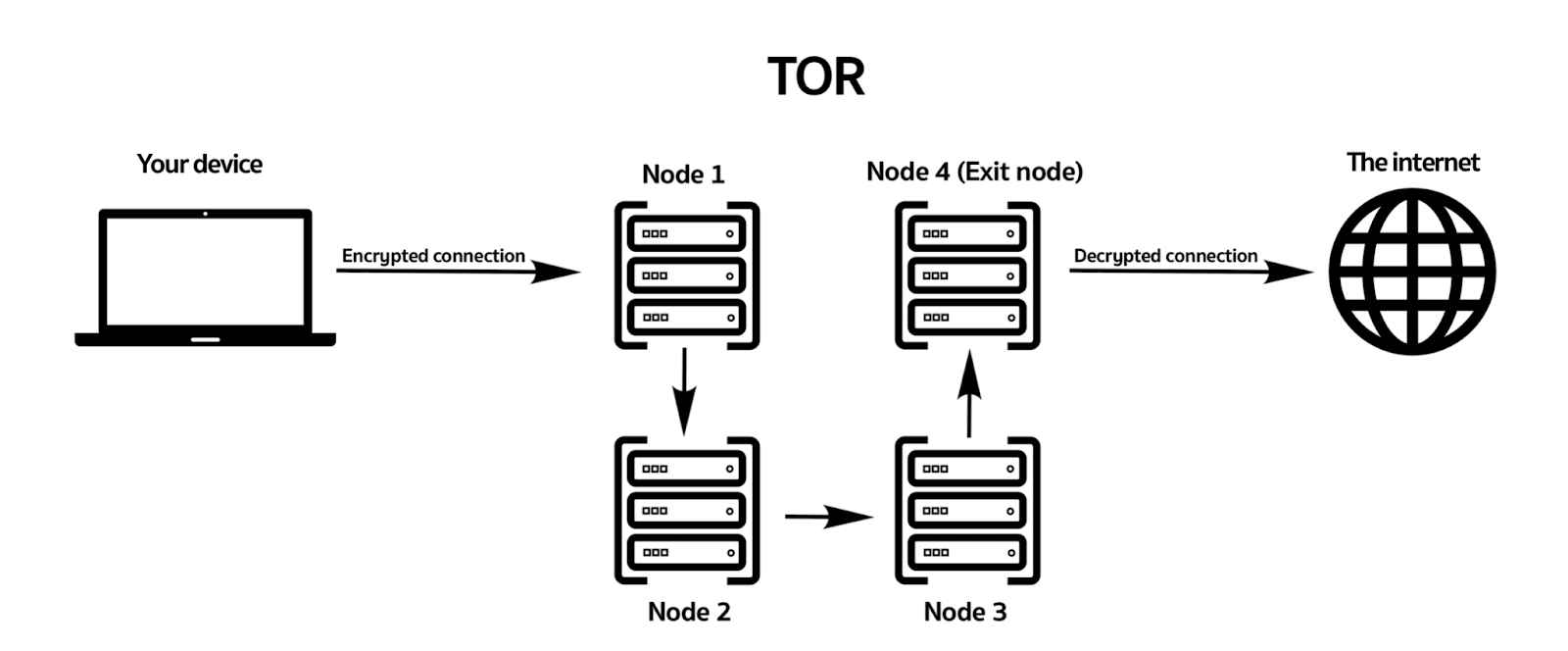
Tor stands for The Onion Router. In a nutshell, Tor is a large network of proxy servers (nodes or relays) operated by volunteers worldwide. When you use Tor, your traffic leaves your device and makes an encrypted connection to a Tor node.
From there, it gets bounced around several other random Tor nodes worldwide (usually between 4 and 6) before being decrypted by the last node in the chain and sent to its ultimate destination.
Your traffic is encrypted at each hop so that no single Tor node can tie together the request’s source, content, and destination.
This is how TOR works:
Like with a VPN, the encryption keeps your ISP and third parties from snooping on your activities. However, your ISP and any websites you visit will know that you’re using Tor.
The list of Tor exit nodes (last-hop Tor nodes, right before going out to the open internet) is public. Hence Tor traffic can easily be identified and even blocked.
The above issue can be mitigated by using Tor Bridges. Bridges are non-public nodes that can be used to connect to Tor even if your ISP is blocking access to known Tor nodes.
Websites that block Tor connection wouldn’t identify the non-public nodes as being from the Tor network. However, using Bridges is not something you can just easily set and forget.
And configuring Tor to use Bridges is beyond the scope of this article. Just be aware that there is a workaround if your ISP blocks Tor.
Using Tor will also replace your IP address with the IP address of the Tor exit node, just like a VPN. So let’s say you’re in the US and your Tor exit node is in France; websites you connect to will see a French IP address and assume you’re in France.
Tor also allows you to access what is referred to as the Dark Web. The Dark Web consists of a network of websites not accessible outside the Tor network (i.e., over the regular internet).
These sites, only accessible through Tor, have a .onion top-level domain (TLD). Much of the Dark Web hosts black markets and is used for criminal activities, but it’s also used for various legal purposes.
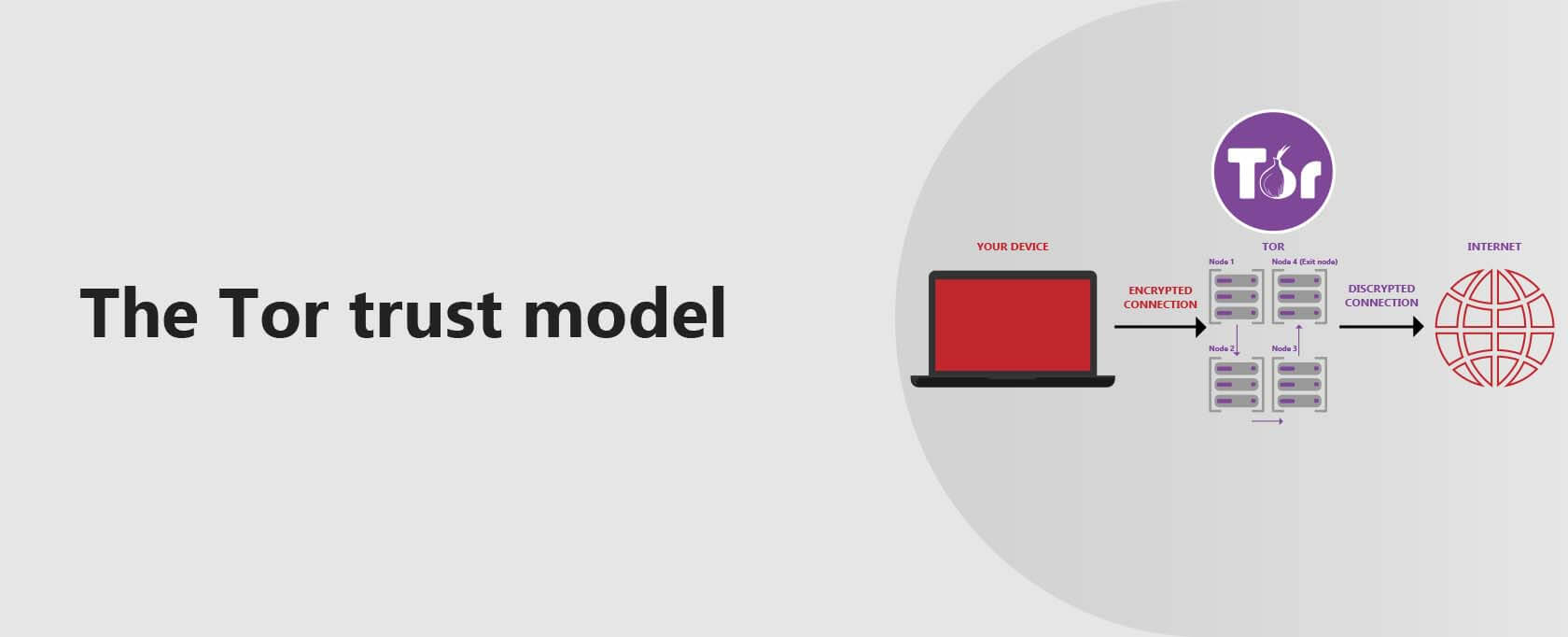
The Tor trust model
So far, VPNs and Tor seem to be practically the same, except Tor bounces your traffic across multiple servers, while a VPN typically (though not always) bounces it over just a single server. While there’s more to it, the trust model is a big distinguishing factor.
With VPNs above, we stated that the trust model was all or nothing. VPNs are centralized services, and the VPN provider can see your traffic. If you don’t trust your VPN provider, don’t connect to its network.
Tor has a significantly different trust model. Tor is distributed; it is a decentralized service. What that means is that nobody owns the Tor network, not a corporation, not an individual.
It’s run by thousands of volunteers around the world. There’s no central point to which all Tor users’ traffic converges. There’s no centralized operator to trust. You need to trust the code.
When using Tor, your connection is routed through a new, random sequence of Tor nodes every time you visit a different website.
Now, while it’s possible that an exit node—the last Tor node in the sequence—could read the unencrypted traffic that passes through it, it couldn’t identify its source. You would still remain anonymous.
Using Tor
The easiest way to use Tor is to download and install the Tor browser. It is a modified Firefox version configured to connect to the Tor network out of the box.
It also has JavaScript and WebRTC disabled for enhanced privacy and anonymity. The Tor Browser also won’t store your browsing history, won’t run any scripts, and will automatically delete your cookies when closed.
There are other ways to use Tor, such as configuring it on your router or using the TAILS operating system, but these are far from straightforward and beyond this post’s scope.
With the Tor browser, all you need to do to connect to the Tor network is launch it.
There are a few things to remember when using the Tor browser. First, only your browser traffic will go through the Tor network. Anything you do outside the Tor browser will continue using your ISP connection.
Second, because Tor bounces your traffic across multiple nodes for each request your device sends, this adds significant latency to your connection.
In other words, Tor will noticeably slow down your connection. Tor favors security and anonymity over speed and performance.
It’s also not advisable to download files using the Tor browser, as doing so may compromise your anonymity by making connections outside the Tor network.
Privacy vs. Anonymity
We looked at the similarities and the differences between Tor and VPNs. And there’s some overlap between the two, for sure.
However, in usage, VPNs are more about privacy, while Tor is more about anonymity. Privacy hides what you do, while anonymity hides who you are.
When you sign-up for a VPN, the VPN provider typically knows who you are. Odds are you paid with a credit card.
And while some VPN providers accept anonymous cash payments or cryptocurrencies, most users pay with a credit card. So, you’re not anonymous to your VPN provider.
But as long as you subscribed to a trustworthy VPN provider that keeps no activity logs, what you do should remain private – your connection is encrypted, and the provider doesn’t keep logs.
If the VPN provider is served a data request from a legal authority, it would be obliged to comply. However, it couldn’t hand over data that it never had before, such as your browsing history. But your payment information, tied to your identity, may well be handed over.
VPNs enhance your privacy; they don’t render you anonymous – especially if you log into any of your online accounts while on a VPN…
Tor, on the other hand, has no owner or centralized server. Tor is a distributed network of nodes operated by volunteers.
There is no sign-up, there is no payment, and there is no need to supply any identifying information at all. Download it, install it, and start using it.
That, coupled with the fact that your traffic is encrypted and bounced between four to six random locations before being sent to its ultimate destination, makes it extremely difficult to correlate a Tor connection to an individual user.
As long as you follow certain guidelines (like not signing into any of your online accounts), Tor can render you anonymous online.
To ensure full anonymity, it’s recommended never to log into any online account tied to you while connected to the Tor network.
This defeats the purpose of anonymity, as your Tor session can then potentially be linked to your identity.
When to use a VPN?
You’ll be better off using a VPN in the following situations:
To bypass censorship: If you reside in a country in which the internet is heavily censored, using a VPN can help you bypass those blocks.
You might need to try multiple servers until you find one that works, but a VPN is typically more successful than Tor because Tor is more easily blocked.
To bypass region blocks: Many streaming sites – like Netflix – restrict access to some of their media based on geolocation.
French content is only available to users in France; German content is only accessible to users in Germany, etc. A VPN allows you to spoof your location and hence can bypass geo-restrictions.
On public WiFI: You never know who else is using the same public WiFi as you are.
And public WiFi is typically implemented with weak security, and many public WiFi access points are open and unsecured networks. Using a VPN while on public WiFi will protect you from hackers without slowing down your connection.
To prevent ISP throttling: Some ISPs privilege certain types of traffic on their network. They achieve this by throttling other types of traffic, typically P2P traffic and video streams.
A VPN hides your traffic from your ISP. If your ISP doesn’t know what kind of traffic you’re generating, it can’t throttle it either.
To bypass restrictive firewalls: Some organizations (schools, businesses) block access to certain online content over their networks.
Using a VPN may bypass these blocks by running over common ports such as 53 (DNS) or 443 (HTTPS) or by using other obfuscation measures. Such networks would very likely block Tor connections.
Torrenting: P2P file-sharing can be risky, so masking your IP address makes sense. A VPN will achieve this while providing you with much better speeds than if you were using Tor.
When to use Tor?
Tor would be recommended to achieve the following:
Browsing the Web anonymously: As mentioned above, there is no sign-up process to use Tor. So your identity is not part of the equation.
And the fact that your traffic is bounced over multiple locations makes it almost impossible to identify an individual Tor user.
However, ensure you don’t log into any of your accounts while using Tor, or you’ll de-anonymize yourself.
Accessing the Dark Web: Tor is the only way to access the Dark Web. A VPN won’t get you there.
High-stakes private communication: Tor is a great tool for untraceable communication.
Remember above when we mentioned that despite Tor’s association with criminal activity, it was also used for many legal and legitimate purposes?
People like journalists, whistleblowers, activists, dissidents, and crime victims can use Tor to communicate safely and anonymously without being tracked or leaving any traces behind.
In certain cases, this can be a life and death matter. So Tor is indeed a valuable tool.
Can you use Tor and a VPN at the same time?
Actually, yes, you can. Nothing is stopping you from doing that. As long as you’re using a high-quality, trustworthy VPN provider, it will be a very secure setup.
Connect to your VPN first, and then launch the Tor browser. Just be aware that doing that will severely slow down your internet speed. So be prepared to make that tradeoff.
If you want to use a VPN with Tor, buying a VPN that allows payment with cash or cryptocurrencies is recommended.
You should also use a “burner” email address, not for anything else – ProtonVPN and ProtonMail are good choices for both cases.
Wrapping-up
So there you go. Both VPNs and Tor are valuable tools to keep your digital life in your control. There is some overlap between the two technologies.
However, depending on what you want to achieve online, you should choose one. Hopefully, this post will help you make more informed decisions about which tool to use and when.
Stay safe.




1 Comment
Rodango Xiang
August 24, 2021 9:57 pm
The problem with Tor is that it is likely “inundated” at every level with government or private sector exploitation.
It would be foolish to assume that anything less than a very substantial subset of the backbone server infrastructure is operated by governments (or private contractor cutouts) whose motivations are to unmask or at least monitor traffic and map the network
Not all such parties are US or even Western govt affiliated (China may very well have the greatest vested interest in this)
Additionally, ongoing open source development of the software is competing with a comparatively much greater effort to exploit or even sabotage the code by comparison to other critical open source projects (like Linux).