VPN Obfuscation — Full Guide & Best Obfuscated VPN
In general usage, obfuscation is done to hide or obscure a message’s intended meaning, making it difficult to understand.
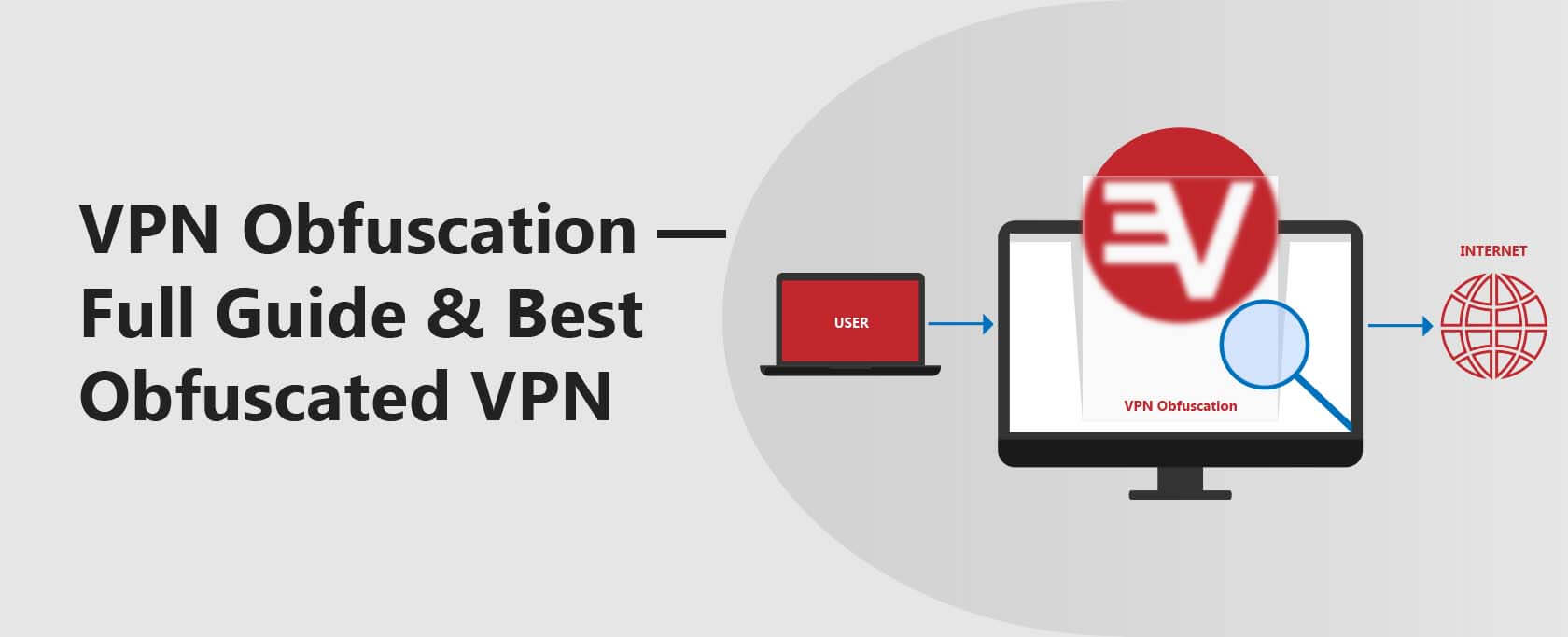
In the context of VPNs, obfuscation is done to hide VPN traffic and bypass VPN blocks.
- VPN obfuscation is a method to hide your VPN traffic and VPN usage.
- VPN obfuscation can bypass VPN bans and VPN restrictions
- It works by scanning non-blocked ports and using those for VPN traffic or disguising your VPN traffic as unencrypted regular web traffic
- It makes your VPN traffic look like regular internet traffic, allowing you to circumvent VPN bans
Looking for a stealth VPN with obfuscation? ExpressVPN offers this as a feature. By using this feature you will be able to hide your VPN traffic and bypass VPN bans.
Below in this article, you can find a much more detailed description of how a stealth VPN works.
Internet Service Providers (ISPs) and governments love to spy on user traffic and use that info for data analytics. The goal, ultimately, maybe to filter for or block out content. But obviously, not everyone appreciates this, so users may employ VPNs to prevent other parties from spying on their data.
Unfortunately, the battle doesn’t end here. Sometimes, governments block VPNs or the standard ports through which VPN traffic passes. So then, as a countermeasure, users employ VPN obfuscation (also known as “cloaking technology” or “stealth VPN”).
How does VPN obfuscation work? By scanning for non-blocked ports and pushing VPN traffic through them or disguising that traffic as unencrypted normal internet traffic. A VPN protocol has unique metadata that can be used to diagnose its identity — obfuscation removes such metadata.
In short, obfuscation ultimately makes VPN traffic look like normal traffic to VPN blockers.
I’ll explain why obfuscation is essential, its primary goals, and the various methods used to achieve it. These methods include Obfsproxy, Stunnel, the SSTP protocol, SOCKS5 Proxy or ShadowSocks, and OpenVPN Scramble or XOR Obfuscation.
I’ll also clear up common misconceptions and concerns about obfuscation and highlight ExpressVPN as a top provider in this field.
My goal with this article is to help you maintain your privacy, navigate censorship, and avoid ISP throttling by using a stealth VPN with obfuscation features.
Why Use VPN Obfuscation?
Obfuscation techniques and obfuscated servers help you achieve five primary goals:
#1. Bypass censorship by the government
The governments of countries like China, North Korea, Egypt, and Iran implement many measures to stop their citizens from accessing blocked or filtered websites. For example, China’s “Great Firewall” blocks Facebook, WhatsApp, and even Twitter.
In response, some users implement a VPN (Virtual Private Network) and make their content unreadable. However, ISPs can detect traffic from a VPN server, and they block this traffic in different ways:
- By blocking the traffic going to a particular VPN server (if the ISP or government knows it).
- By blocking the ports that VPN traffic enters through (this port is usually 1194).
- By detecting the nature of the traffic and labelling it as VPN traffic. This is an advanced method that uses Deep Packet Inspection to identify the signature of the OpenVPN protocol.
VPNs can pass the traffic from different servers and through various ports to avoid the first two blocking types. But to counter advanced detection mechanisms such as DPI, VPNs need obfuscation to disguise their traffic as normal traffic.
#2. Avoid network blocks
Even if your government doesn’t restrict internet access, you may not be completely out of the woods yet. Your workplace or university, for example, might employ special detection techniques to render even your VPN obsolete. Fortunately, VPN obfuscation can help you here, too.
#3. Increase privacy and anonymity
VPN obfuscation provides you with more security, privacy, and anonymity over your data. You’ll be safer not only from the prying eyes of governments and ISPs but also from those of cybercriminals.
#4. Unblock streaming websites
Unfortunately, a VPN might not always unblock popular platforms like Netflix in countries where it’s unavailable. These platforms block VPN traffic visiting their sites through the various means previously discussed in this article. An obfuscated VPN server is your only hope of accessing these sites.
For those specifically interested in Netflix, our guide to the best Netflix VPN offers valuable insights into choosing a VPN capable of consistently bypassing the streaming giant’s VPN blocks.
Check out our guide on how unblocking websites work to learn more about this subject.
#5. Avoid ISP throttling
ISP throttling is when your ISP halts or meddles with speed when you stream or download large files. A VPN can stop this from happening, but only to the extent that it isn’t detected as VPN traffic. Obfuscation is a practical solution to this problem, too.
How Does VPN Obfuscation Work?
There are several ways to obfuscate your VPN traffic. Note that for any obfuscation to work, both the client and obfuscated server need to be set up.
Obfsproxy
This worked parallel to the Tor Project and was originally designed as a countermeasure for the block on the Tor browser in countries like China, Iran, and Syria.
However, this can also be used with OpenVPN.
How does Obfsproxy work? As previously discussed, DPI algorithms can detect traffic belonging to a particular type, such as HTTP, BitTorrent, SSL, and VPN.
Obfsproxy allows Tor traffic or VPN traffic to flow while taking on a preferable appearance. It adds a wrapper around your traffic and uses a handshake that consists of unrecognizable byte patterns.
Stunnel
This proxy server adds an extra layer to user VPN traffic so it’s seen as TLS/SSL traffic. This way, DPI algorithms can’t detect it as VPN traffic.
TLS/SSL is an encryption type used by HTTPS. So, snooping ISPs and governments can’t distinguish between real HTTP traffic and one masked by the Stunnel software.
SSTP protocol
Secure Socket Tunneling Protocol (SSTP) changes VPN traffic to look like HTTPS traffic. This VPN protocol uses SSL encryption and port 443 instead of TCP. Sniffers would have difficulty distinguishing between normal HTTPS traffic and VPN traffic, as HTTPS protocol also uses SSL for secure browsing.
The only drawback with the SSTP protocol is that it can be used only on Windows platforms, not Linux or macOS platforms.
SOCKS5 Proxy or ShadowSocks
A Chinese programmer first introduced this as a solution to the VPN block in China. The Socket Secure 5 (SOCKS5) protocol is at play here, and it’s secure enough to use this.
ShadowSocks delivers fast and reliable service while adding an extra layer of protection so that unauthorized persons are given no access to shared data.
OpenVPN Scramble or XOR Obfuscation
OpenVPN traffic is disguised so it can’t be detected as generated from an OpenVPN server. This has been proven to effectively defy DPI algorithms, as it can bypass even the strongest VPN blocks implemented by many ISPs.
OpenVPN Scramble is also known as “XOR Obfuscation” because it’s implemented using the XOR encryption algorithm. The XOR algorithm is a very simple additive cipher.
OpenVPN itself does that. This algorithm scrambles the data in the OpenVPN traffic so that DPI algorithms can’t identify the added signature. Although this may not sound very secure, it’s not this cipher’s duty to worry about security.
Concerns About VPN Obfuscation
Traffic encryption
There’s a misconception that obfuscation decrypts VPN traffic. But VPN traffic is always protected with a reliable VPN, and obfuscation only masks the VPN traffic so that ISPs can’t detect it as such.
Network neutrality
Network neutrality is the concept that ISPs should treat all internet communications equally — regardless of the content, user, website, destination IP, and more. ISPs can’t charge differently or slow down connections for different users. But in reality, they don’t follow this principle.
So the advantages of net neutrality regarding obfuscation also depend on the ISPs. If they decide to charge differently for specific services their customers use, a VPN can’t help.
Drawbacks of using VPN obfuscation
- Obfuscation demands more resources than your regular VPN traffic to introduce extra layers of protection.
- If you don’t have a high-speed internet connection, obfuscation can crash your online activities.
- VPN obfuscation may slow down your connection due to extra encryptions.
Obfuscation and the Best VPN Providers
Many VPNs claim that they offer the best obfuscation techniques. But beware because unless it’s a reliable VPN, it may fail even to bypass government firewalls. And even if it works, it might still be annoyingly slow.
Let’s look at some of the best VPN providers whose services live up to the quality they claim.
ExpressVPN
So far, ExpressVPN is rated as the best VPN to provide obfuscation in countries like China. This is impressive, considering China has an advanced online censorship system known as the Great Firewall.
Although ExpressVPN may not be as cheap as other VPN vendors, it has a wide range of o obfuscated server locations and offers 24/7 service. It’s available almost 100% of the time and provides the best security.
ExpressVPN is a good option if you are interested in unblocking Hulu or watching ITV in the USA.
You can try ExpressVPN risk-free. So even if it is not for you, it’s easy enough to avail of the 30-day money-back guarantee and switch to a different vendor.
How to set up Obfuscation in ExpressVPN
1. Download the ExpressVPN application.
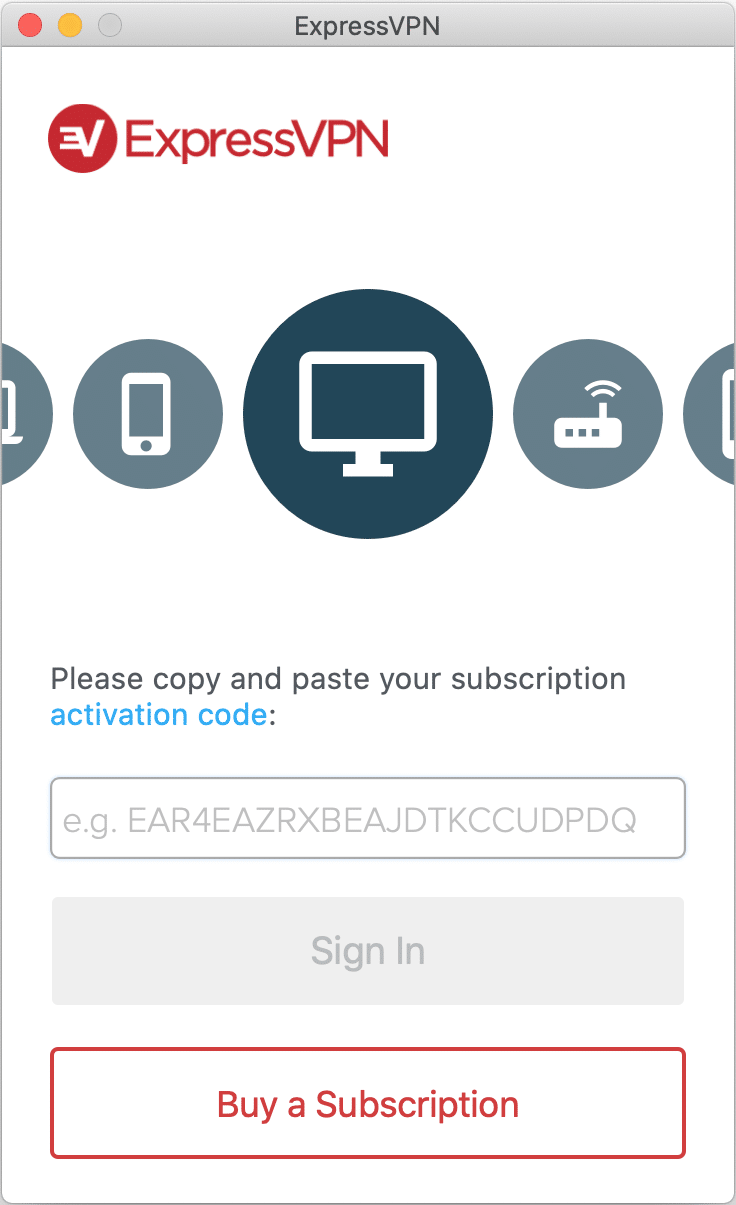
2. Log in to your account.
3. Activate ExpressVPN by entering the activation code.
4. Obfuscation is a built-in feature available for some servers. Therefore, if you reside in a country like China, you’ll have to use the designated obfuscated server for China users. If you don’t know the exact servers, ask the support team.
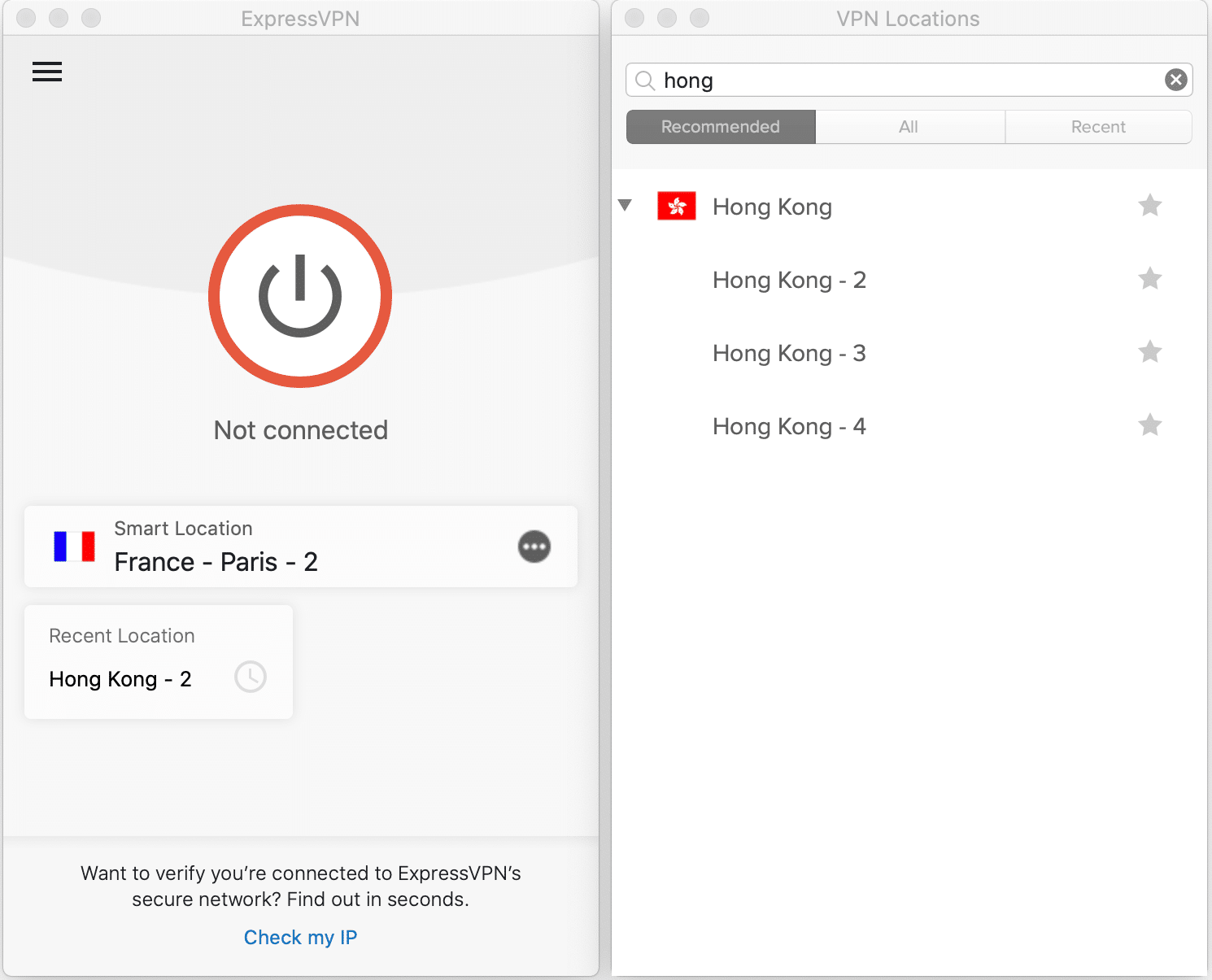
5. Navigate to “All Locations” and search for the Hong Kong server.
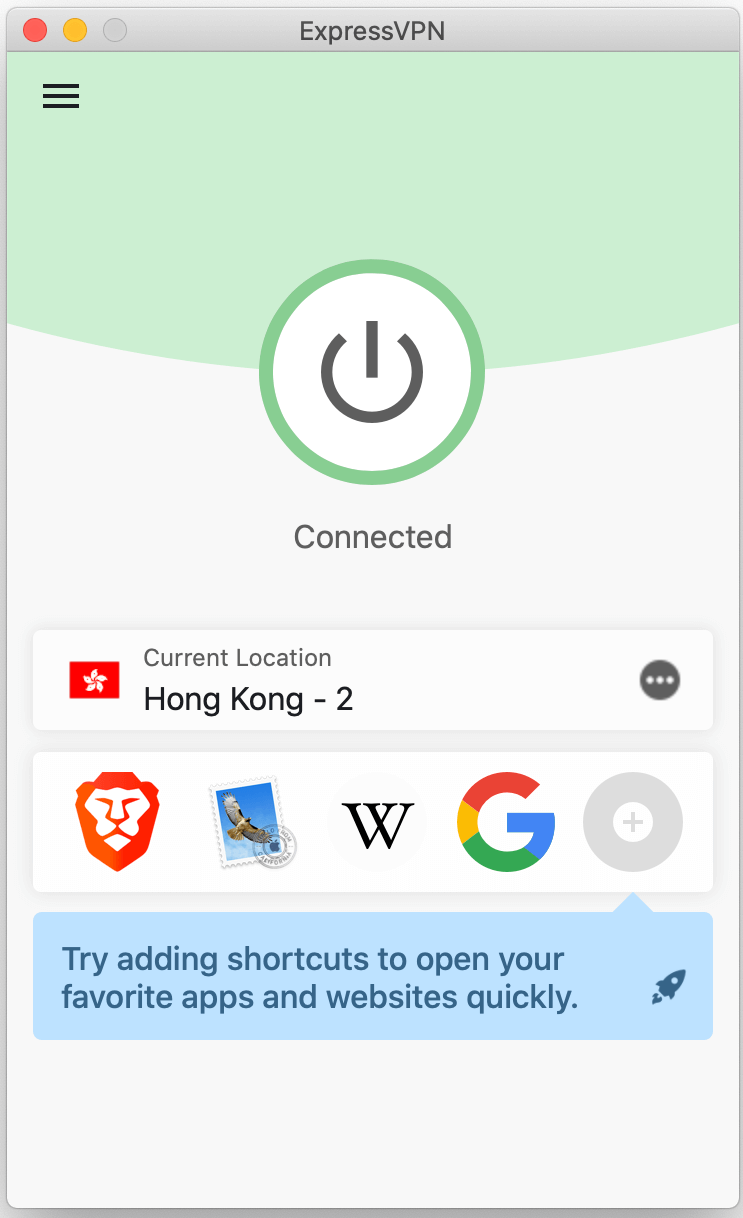
Then:
And finally:
NordVPN
What’s great about NordVPN is its affordable prices. With unlimited bandwidth covering more than 60 countries, it allows for fast streaming and specialized security and privacy optimizations.
It is also a good option for unblocking Netflix.
How to set up Obfuscation in NordVPN
- Download the NordVPN application, and enter the login details.
- Navigate to the settings.
- Click on Advanced Settings.
- Tick the “I know what I am doing” checkbox.
- Enable the “Obfuscated Servers” option.
SurfSurfsharkShark
The next best option to consider if you’re in an internet-censored country is Surfshark. What’s unique about Surfshark is that it allows you to connect with an unlimited number of devices with a single subscription. It unblocks the most restricted servers and keeps no logs of user traffic.
How to set up Obfuscation in Surfshark
You need to enable NoBorders, which allows VPN obfuscation in Surfshark.
- Open Surfshark and go to the settings.
- Select “Advanced.”
- Enable NoBorders.
VyprVPN
VyprVPN is a VPN service that provides a well-optimized encryption service with high-speed servers.
Chameleon Protocol is the Obfuscation mechanism used in VyprVPN. This code scrambles the metadata created in the OpenVPN and makes the signature unrecognizable to the Deep Packet Inspection algorithms.
Use these obfuscated VPN providers with their obfuscated servers to hide your internet activity.
Do free VPN have obfuscated servers?
A free VPN usually never has stealth VPN technology or obfuscation features. Their connection speed is also very slow. A free VPN is susceptible to VPN blocking.
How to Optimize Your VPN Obfuscation
There are several things you can do to improve the performance of your VPN obfuscation.
- Use the nearest VPN server. This can speed up your connection, as it takes less time for the data packets to travel.
- Change the default DNS address to the provider’s address. This is normally done by most VPN vendors.
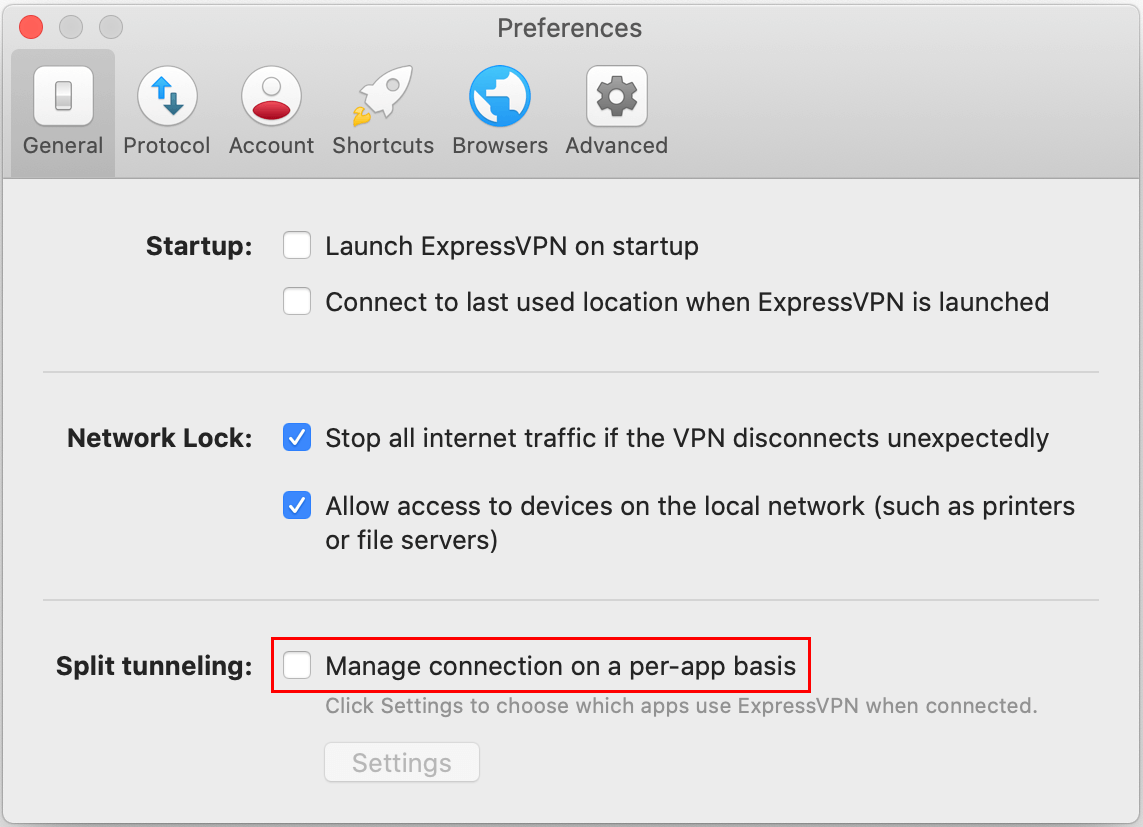
- Use split-tunnelling so that other traffic apart from VPN traffic flows through an unencrypted separate tunnel. This can make your internet traffic less weighty. Here’s how to use split-tunnelling with ExpressVPN:
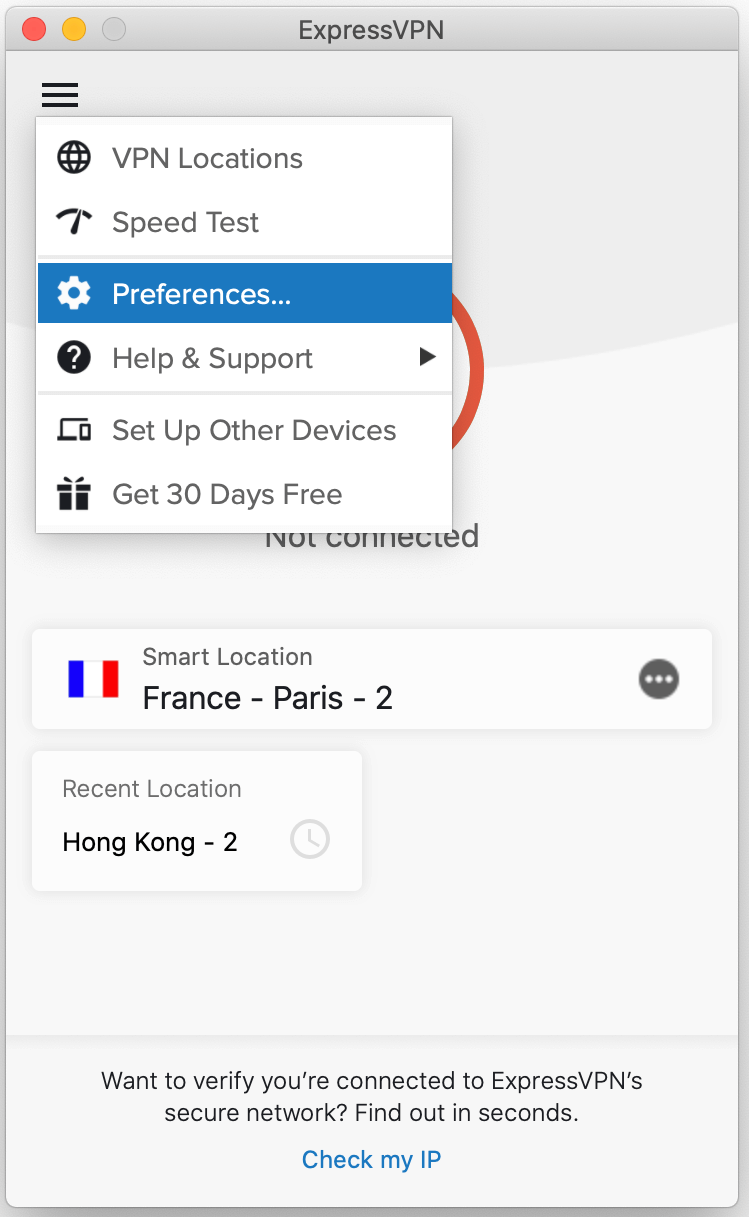
1. Select “Preferences” from the menu.
2. The “General” tab has an option for split-tunnelling. Enable it and click on Settings.
3. Now you can select how you want your internet traffic to use the VPN services.
To prevent leaks, employ a VPN kill switch or a double VPN. If it’s always on, you can be sure your internet traffic won’t be sent if the VPN goes down.
In ExpressVPN, Network Lock is the Kill Switch. You can enable it in the “General” tab under the “Options” window.
Not only can implementing all these measures help avoid slow connections, but it can also improve security.
Conclusion
VPN obfuscation is great for bypassing government- and ISP-deployed firewalls and improving your internet traffic’s privacy and anonymity.
But have you won? Aren’t their ways for the government to block VPN obfuscation, too? Well, not directly. But they can, of course, block the VPN providers’ official websites.
Then you’ll have no access to a reliable VPN. So if you live in a country where government censorship is serious, and if you’ve spotted a VPN that hasn’t been blocked yet, get your hands on it ASAP.
As you know by now, VPN obfuscation is fairly straightforward. All you have to do is take your pick from among the reliable vendors available. But if you live in a country that gives you the freedom to browse and shop online as you wish, our VPN recommendations above are yours for the taking.